What is a honeypot and how does it work?

A honeypot is a surefire way to attract someone to something. And like Winnie-the-Pooh, hackers find it hard to resist the allure of a honeypot. While honeypots may be used by criminals to lure victims, detectives and cybersecurity teams also use them to entrap criminals and hackers. Read on to learn more about honeypots and how they work. Then, get Norton 360 Deluxe to help protect your device from hacking and secure your digital life.
What is a honeypot?
A honeypot is a cyber trap or decoy designed to look like a legitimate part of a system, network, or other digital environment. Honeypots are used to lure cybercriminals away from real digital assets, and they can be modeled after software, server infrastructure, or even an entire network to look convincing to cybercriminals.
Honeypot meaning
While honeypots are tools used by cybersecurity teams to lure hackers and other criminals into environments that security teams can control and monitor, the basic meaning of a honeypot is much broader. A honeypot is anything or any location that attracts a certain type of person.
How honeypots work
Honeypots work like bait to lure hackers or criminals, just as honey can be put out to attract bears. In the field of cybersecurity, honeypots are fake digital assets or environments designed to attract cybercriminals. These assets could include software applications and data that act like a legitimate computer system, contain sensitive data, and aren't secure.
Honeypots usually contain a security vulnerability that isn’t too obvious, but obvious enough that many cybercriminals wouldn’t want to pass up the chance to get into the system. This lures or distracts them away from the real system, which is better protected.
For example, honeypots can be used as part of a bank’s IT security. You might set up a honeypot system that, to outsiders or hackers, looks like the bank’s network. This helps protect the bank’s real network by diverting malicious traffic.
Once the hacker accesses the honeypot, security teams can track their movements, allowing analysts to detect and defend against cybercrime by gaining an understanding of how hackers operate and what they want. Honeypots can also be used to determine which security measures are working and which need improvement.
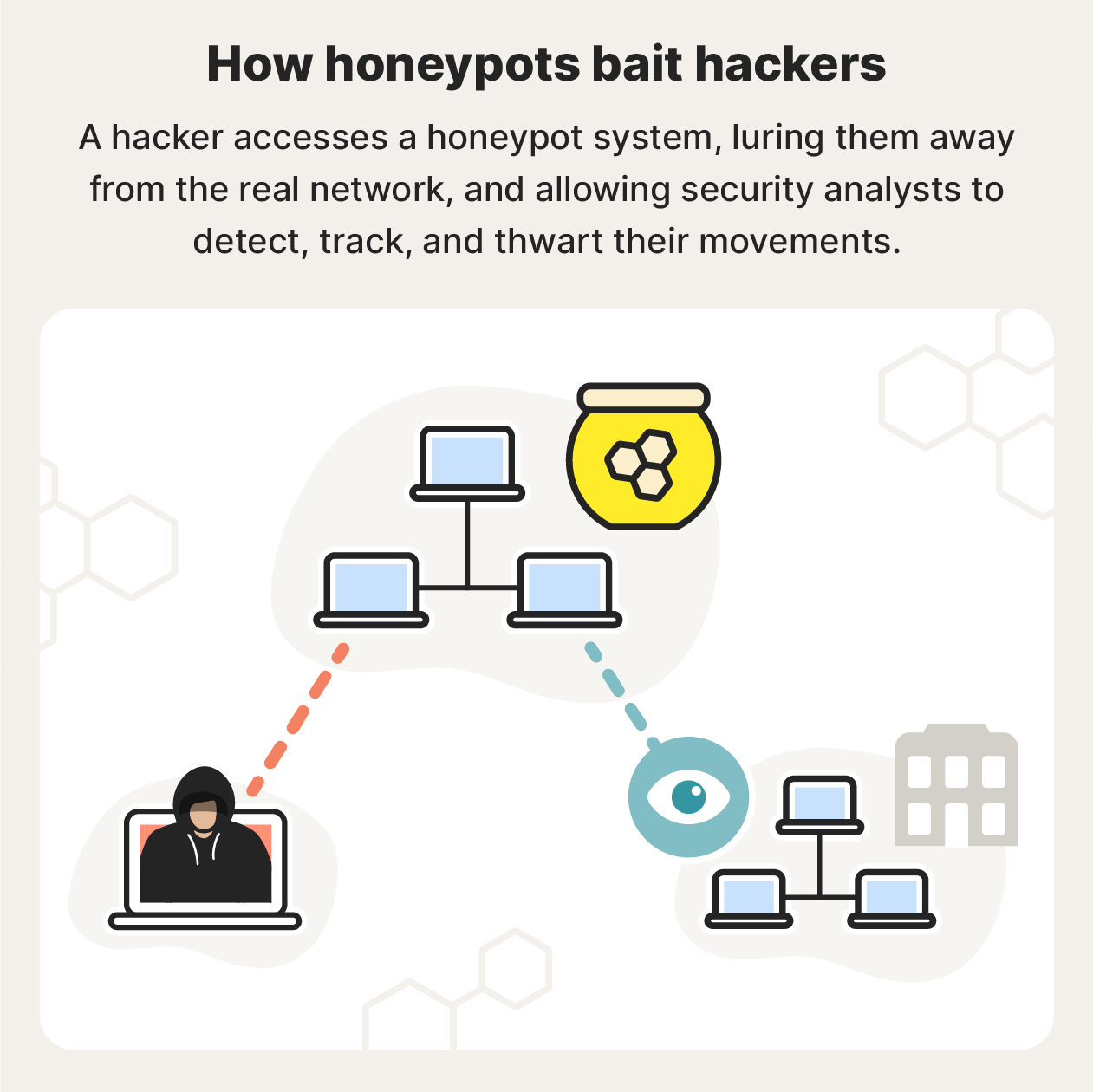

Honeypots can be useful in detecting and preventing outside attempts to break into internal networks. A honeypot could be placed outside an external firewall to attract, deflect, and analyze traffic.
What are honeypots used for?
Honeypots help cybersecurity teams protect valuable digital assets and figure out the best strategies for keeping hackers at bay. More specifically, honeypots are used for cybersecurity research and production.
- Research honeypots: Research honeypots allow administrators to study the activity of hackers to learn how to protect against digital threats. Honeypots can also help expose system vulnerabilities that might not otherwise be detected. For example, honeypots can be set up to receive only fake traffic. Then, if any real activity is detected, security teams know that cybercriminals may be active.
- Production honeypots: Production honeypots are usually placed inside networks to act as a decoy and lessen the risk of real assets being infiltrated. These honeypots serve to distract hackers from legitimate targets inside a network.
Hackers, for their part, may use something similar to a honeypot, known as a watering hole attack, which lures unsuspecting users into giving away their personal data or downloading malware. But “honeypot” in cybersecurity is more often used to describe defensive tactics by security teams rather than offensive ones used by hackers.
If you own a small business, it's critical to keep all your digital assets protected. Norton Small Business helps safeguard up to 20 of your company’s devices, both mobile and desktop, with powerful protection to suit your needs. Norton Small Business also provides 24/7 support, so we’re there when you need us.
Types of honeypots
Just as there are different types of cyberthreats and different types of hackers, there are different types of honeypots to gather intelligence on those threats.
Here are five common types of honeypots:
- Email honeypots (also known as spam traps) are fake email addresses created to attract and receive spam emails. They help block spammers from sending malicious emails to legitimate email addresses, and they’re used to study spamming activity.
- Database honeypots contain vulnerable and fictitious datasets to attract attackers who get through firewalls. These honeypots are used to monitor the type and number of attacks that occur in databases.
- Malware honeypots copy software apps and APIs (Application Programming Interfaces) to attract malware attacks. These can be used to find out what API weaknesses need to be addressed and help create anti-malware software.
- Spider honeypots are malicious bots and ad-network crawlers that prowl the web, looking to trap automated crawlers with accessible web pages and links.
- HoneyBots are the newest type of honeypot, developed by university researchers. Unlike other honeypots, a HoneyBot can interact with hackers, mimicking legitimate systems to look more convincing.
Pros and cons of honeypots
Honeypots can play a useful role in strengthening cybersecurity, but there are some limitations and risks to using them.
Benefits of using honeypots:
- Honeypots are effective threat detectors, luring hackers into a controlled environment so their activities can be monitored.
- They engage in real data collection about cyberattacks, including information on hacker behavior, tools, techniques, and new attack vectors. That helps security teams understand how cyberattacks work.
- Because hacker activities are their only genuine interactions, honeypots give fewer false positives when monitoring cybersecurity.
- They typically run on their own with minimal monitoring, so honeypots are cost-effective and low maintenance.
Drawbacks of using honeypots:
- Honeypots collect only attack data, limiting the scope of their usefulness to monitoring hacking potential and vulnerabilities.
- They may allow hackers to more easily avoid honeypots, as there can be telling characteristics behind how a honeypot works that signal to savvy hackers that they’re about to enter a trap.
- If they’re not properly secured, honeypots may actually increase the attack surface, providing hackers with another entry point into an organization’s system or network.
Help protect your devices against cybercrime with Norton 360 Deluxe
Honeypots can be an effective cybersecurity mechanism for monitoring attacks and tracking hacker behavior. But most of us don’t have the need, resources, or skill to build honeypots to secure our own devices. That’s where powerful, automated cybersecurity software comes in.
Norton 360 Deluxe is a comprehensive cybersecurity suite that helps defend your device against hackers, as well as viruses, malware, and other online attacks. Plus, it features a built-in VPN to encrypt your connection and help keep your communications private.
FAQs about honeypots
Do honeypots pose risks?
There may be some risks associated with using honeypots. If security teams rely too heavily, or solely, on intelligence gathered from honeypots, they risk missing other hacking activity that isn’t being caught by the honeypot. More sophisticated hackers may also begin to spot honeypots due to their static nature and fingerprinting.
Are honeypots illegal?
While honeypots themselves are not illegal, there are some legal and ethical issues to consider when using a honeypot, because honeypots collect and analyze personal data. Before employing a honeypot, consider all applicable privacy laws in your area, along with state and federal anti-hacking laws.
What is the difference between a honeypot and a honeynet?
The primary difference between a honeypot and a honeynet is that a honeynet is an entire network of honeypots. So honeynets can work on a much larger scale than a single honeypot. But for both, the main purpose — to collect and capture data on hackers — remains the same, as does their basic functionality.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.







Want more?
Follow us for all the latest news, tips, and updates.