What is an attack surface? Definition + reduction tips

An attack surface represents all the points where an unauthorized user could sneak into a computer system. Keep reading to learn more about what an attack surface is and the different types of attack surfaces that hackers exploit. Then, download Norton 360 Deluxe to help reduce your attack surface, prevent hacking, and protect your digital life.
What is an attack surface?
An attack surface is a cybersecurity term that describes all the possible points that an attacker could exploit to enter a digital system or organization. Hackers gain access via an attack surface by exploiting digital or physical security vulnerabilities or using social engineering techniques.
Types of attack surfaces
There are three different types of attack surfaces: digital, physical, and social engineering. Each attack surface has its own set of vulnerabilities, or attack vectors, that criminals can use to break into. You can think of the attack surface in the same way you might envision a ship’s hull. A leak in just one area can sink the whole boat, so it’s important to secure all possible entry points.
Digital attack surface
A digital attack surface describes threats associated with your network, operating system, software, and apps. Technology moves fast, and new security vulnerabilities can pop up at any time. And attackers can often exploit these vulnerabilities from anywhere in the world.
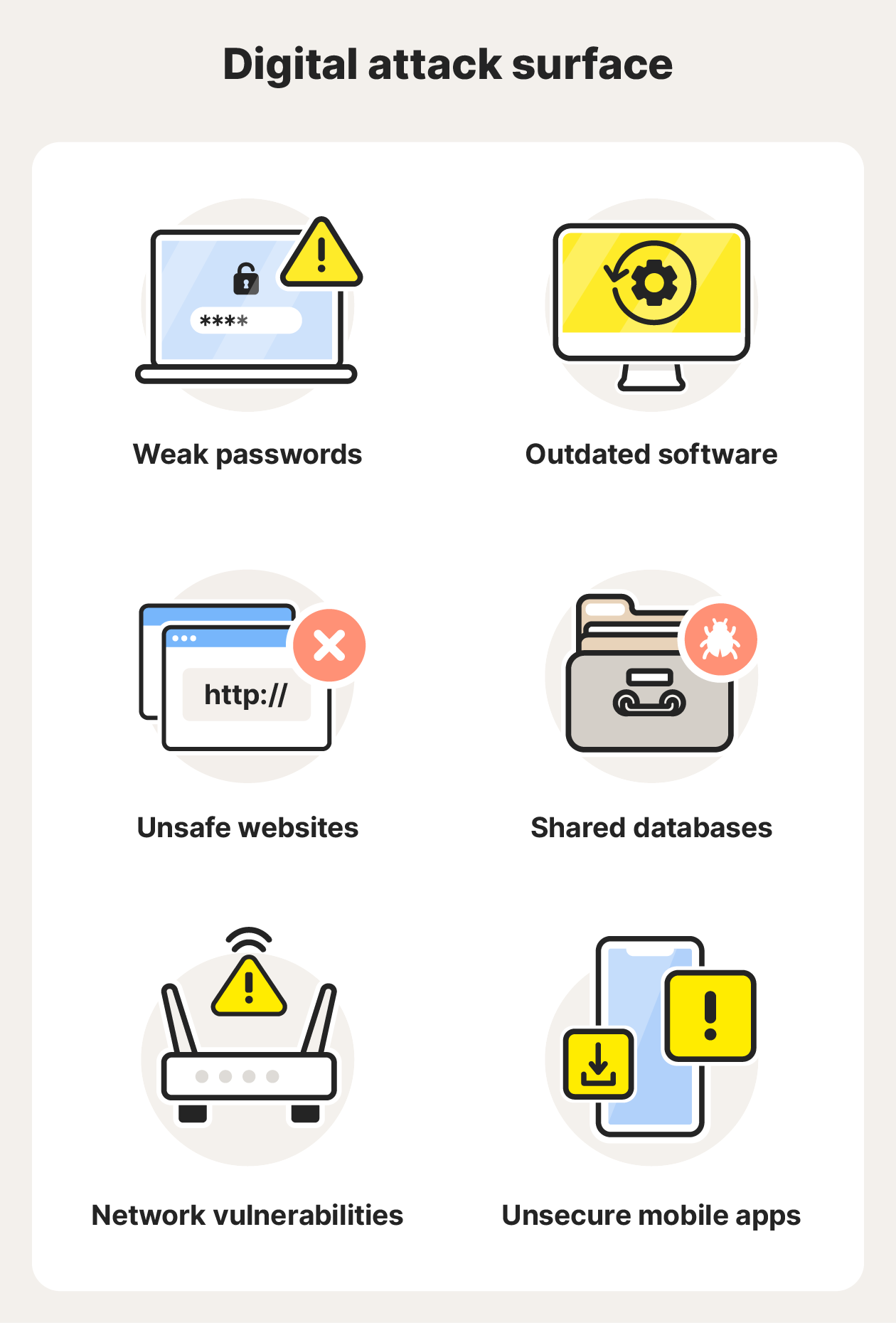
Digital attack vectors include:
- Weak passwords: Attackers can crack simple passwords. Shoring up your password security is one of the best ways to reduce your attack surface.
- Outdated software/operating system: Regular operating system and software updates are crucial because they patch potential security vulnerabilities to keep you safe.
- Unsafe websites: Visiting malicious websites (they’re often missing an SSL certificate) is like opening a door to your data and devices.
- Shared databases: Shared databases make it easy to share data and collaborate, but they also increase the risk of intrusion.
- Network vulnerabilities: Logging into unsecured networks or joining public Wi-Fi can make it easier for attackers to access your devices and data.
- Unsecure mobile apps: Apps downloaded from unsafe sites can be infected with malware and allow backdoor access for hackers.
Physical attack surface
A physical attack surface includes all the devices and physical assets an attacker could gain access to such as phones, laptops, hard drives, and USBs.
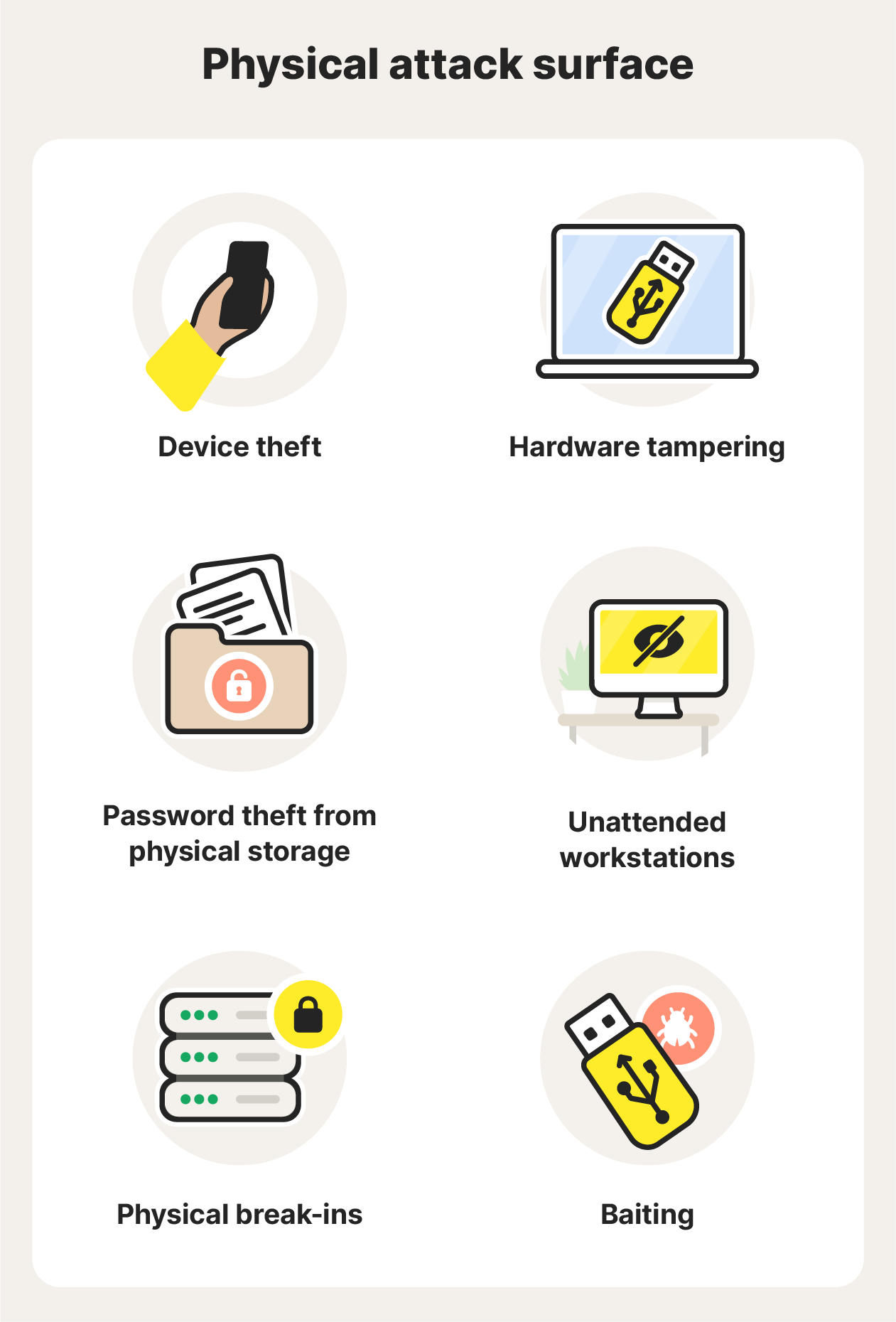
Physical attack vectors include:
- Device theft: Attackers can use a lost or stolen device to access secure networks, bank accounts, passwords — potentially your entire personal and professional life. They could even gain access to your device and install malware on it before giving it back to you.
- Hardware tampering: From modifying a server to sticking a USB with malware into a computer, hardware tampering allows attackers to gain unauthorized access without the need to do any digital hacking.
- Password/credential theft from physical storage: Notebooks, physical files, or hardware password managers containing sensitive information are easy targets for hackers.
- Unattended workstations: Out for lunch? Some office buildings aren’t locked during the day or have poor security. Attackers could walk in and access your computer.
- Physical break-ins: A physical break-in or tailgating attack gives cybercriminals access to computers, servers, ports, and more. For this reason, many businesses keep their servers in locked cages.
- Baiting: Attackers can leave a malware-infected USB lying around, hoping someone will connect it to their computer.
Social engineering attack surface
The previous types of attack surfaces describe software and hardware vulnerabilities that hackers can leverage for nefarious ends. Social engineering attacks deal with human manipulation, so social engineering attack surfaces refer to the different ways humans can be manipulated to compromise the security of systems they have access to. The attacker hopes to trick the target into giving away their personal data or clicking dangerous links.
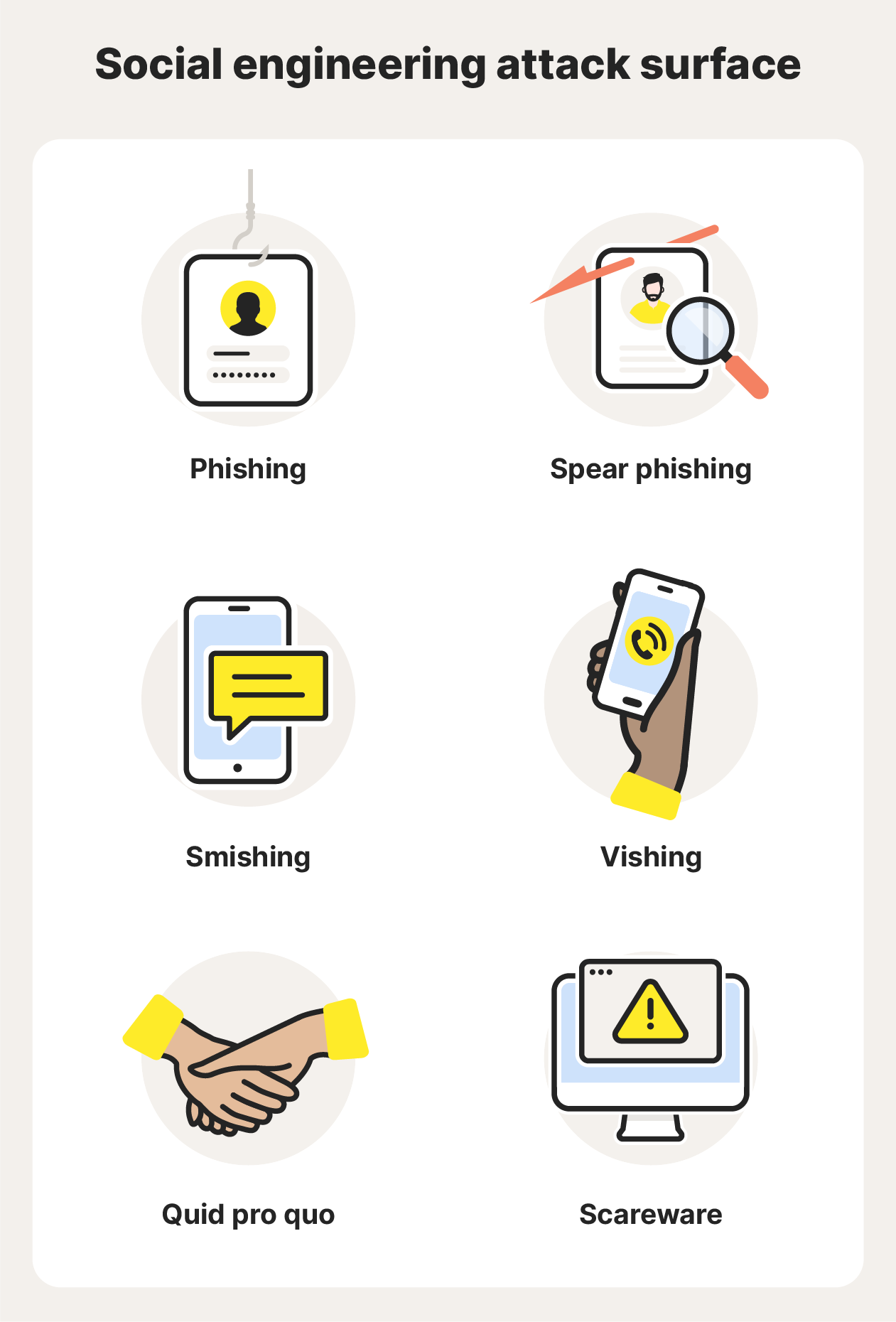
Social engineering attack vectors include:
- Phishing: A phishing attack happens when a fraudster imitates a trusted person or organization in order to gain access to sensitive information. Phishing attacks usually happen via email or text, but many types of phishing attacks exist. Learning how to spot a phishing scam is a crucial part of overall digital hygiene.
- Spear phishing: While phishing emails are often generic messages sent to many targets, spear phishing attacks target specific individuals with personalized, often highly convincing messaging.
- Smishing: Smishing is like phishing but via SMS (text messaging). The aim is usually to get victims to click a malicious link and enter personal details.
- Vishing: The word vishing is a combination of “voice” and “phishing.” It describes when an attacker makes a phone call to manipulate targets, usually imitating an organization the victim trusts (for example, pretending to be from the fraud team at their bank).
- Quid pro quo: This is when an attacker offers you something, such as a free in-app upgrade, in exchange for your login details or other sensitive info.
- Scareware: Scareware relies on fear tactics to scare you into taking action. This can include handing over confidential data or downloading malicious software to “fix” a cybersecurity problem that doesn’t exist.
Attack vector vs. attack surface: What’s the difference?
The biggest difference between an attack vector and an attack surface is that an attack vector is how an attacker exploits a system. By contrast, the attack surface is the sum of all the attack vectors or vulnerabilities that a cybercriminal could exploit.
As we saw above, there are three types of attack surfaces: digital, physical, and social engineering. Within each of these categories lie numerous attack vectors.
If you consider how many types of malware a hacker could use to harm your system or steal data, you can appreciate how hard it is to protect yourself from every threat. From ransomware to trojan horses to new, emerging malware strains, it’s nearly impossible to keep track of all of today’s digital threats.
That’s why you should use dedicated security software to help reduce your attack surface and prevent hackers from accessing your devices. A security solution like Norton 360 Deluxe helps defend against new and emerging threats, providing poweful protection against viruses, malware, hacking, and more. Plus, it includes a built-in VPN to encrypt your connection and help protect the data you share online.
7 attack surface management tips to reduce your attack surface
Attack surface management is the ongoing process of monitoring your digital and physical assets for vulnerabilities. The purpose is to mitigate your risk of being attacked.
How many hours a day do you spend online? The more connected you are, the more you expose yourself to hackers and other malicious actors.
The number of cyberattacks is growing rapidly — it increased by nearly 40% in 2022 alone. Thankfully, you can minimize your attack surface and strengthen your digital security by implementing a few simple tips.
Here are seven important tips to incorporate into your digital life:
- Use strong passwords: Strengthening your passwords is one of the easiest and most effective ways to reduce your attack surface. Some types of hackers are skilled at using brute force attacks to crack weak passwords, so it’s important to update them often and make them strong and unique.
- Enable 2FA: 2FA means two-factor authentication. It requires you to verify your identity in two separate ways to sign into an account. Usually, the first method is with your password. The second may be a code sent to your phone or email, a fingerprint, or a code from an authenticator app.
- Practice good cyber hygiene: Cyber hygiene involves using products and tools that fit your needs, performing digital hygienic tasks correctly, and setting a routine to look after your devices and protect your online activity.
- Use antivirus software: Antivirus software helps with attack surface reduction. This software keeps watch over your files, apps, and online activity to block attacks before they happen.
- Update software regularly: All software has vulnerabilities that hackers can exploit. As these cracks are discovered, developers create patches that fix them. If you don’t update your software, the cracks don’t get repaired and you become a target for attacks.
- Double-check suspicious emails, texts, and calls: If you receive a suspicious email or text from someone you don’t know, don’t click any links as they could be malicious. It also pays to be mindful of social engineering techniques that may involve a hacker imitating someone you know, like a colleague, friend, or family member.
- Keep your hardware and personal devices secure: Use strong passwords for all of your devices, even if it’s a desktop at home. If a criminal gets their hands on your hardware, they may be able to easily access your finances, social media accounts, and personal info, which could even lead to identity theft.
Protect your attack surface and digital life
Make sure you carry out an attack surface assessment on all your digital and physical assets, then close any holes. And use a trusted security app to take care of the risks you can’t see or predict. Norton 360 Deluxe helps protect against hackers, malware, and viruses, and it features a built-in password manager to help keep your passwords safe.
Plus, it comes with a VPN so you can encrypt your online connection and help keep your communications safe from prying eyes. Download Norton 360 Deluxe and help keep your attack surface clean.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.



Want more?
Follow us for all the latest news, tips, and updates.