What is cryptojacking? An overview + prevention tips
Cryptojacking Definition
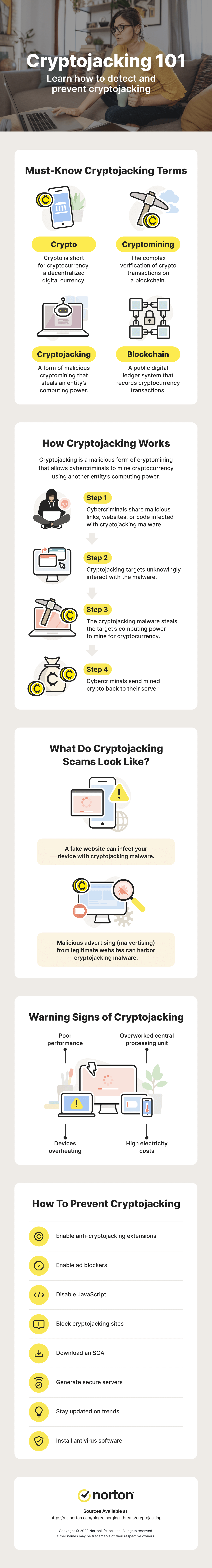
Cryptojacking is a form of malicious cryptomining that allows cybercriminals to mine cryptocurrency using another entity’s computing power.

Cryptojacking attacks nearly tripled in 2022, resulting in high electricity and cloud service bills for targets. As cryptojacking cases continue to rise, it’s more important than ever to understand how cryptojacking works and how to try and avoid it from happening to you.
Although legitimate cryptomining is a legal way to obtain cryptocurrency like Bitcoin, cryptojacking is a malicious form of mining that allows cybercriminals to mine for free.
Entities affected by cryptojacking are left to shoulder the high electricity and cloud service costs associated with cryptomining. Read on to learn how to detect and prevent cryptojacking in 2023.
How does cryptojacking work?
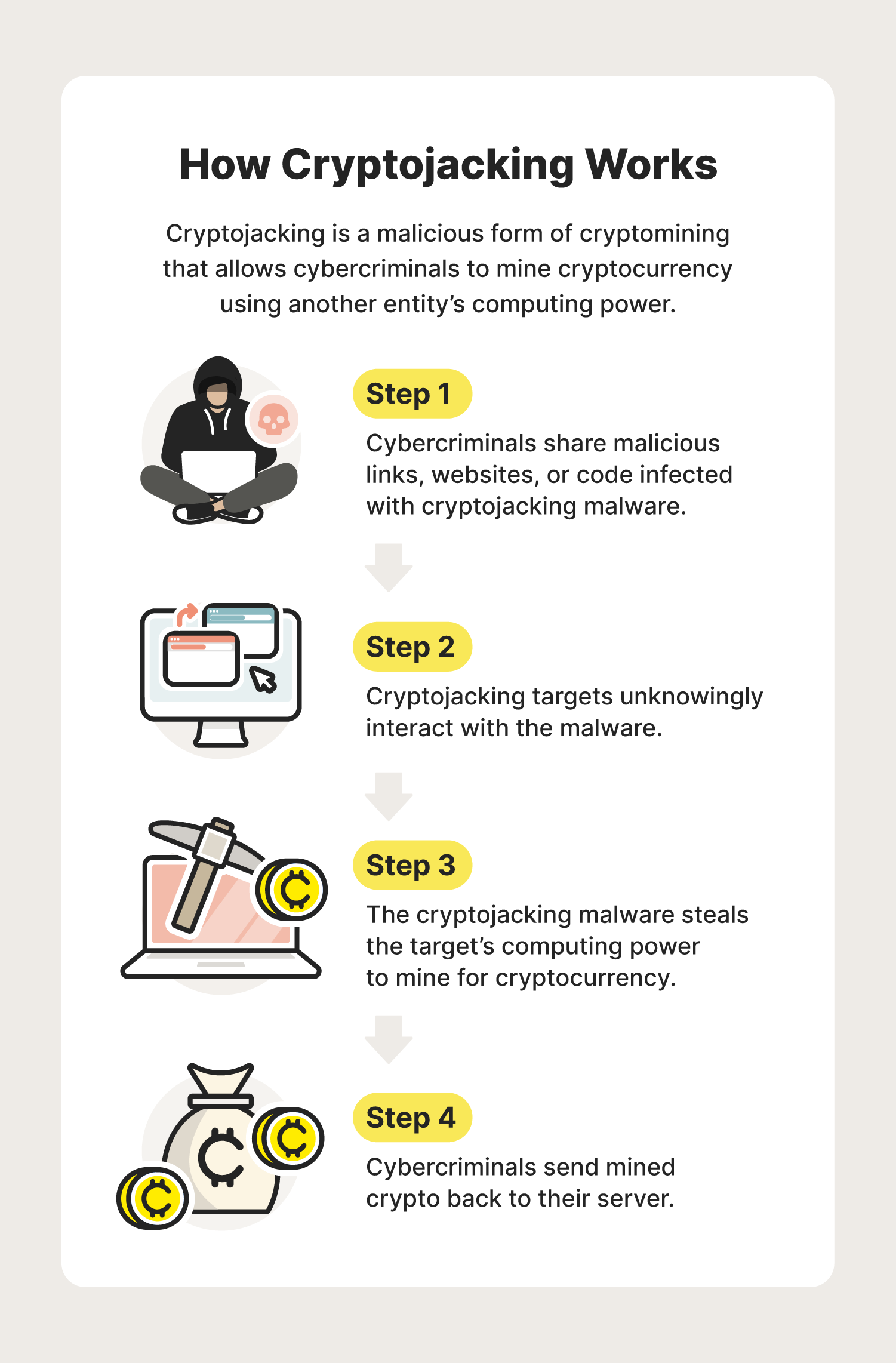
Cryptojacking is a cyberattack that hijacks the cryptomining process — the process of verifying cryptocurrency transactions by solving complex puzzles using computing power.
Cryptojackers aim to mine cryptocurrency for free by deploying malware on their targets’ servers. Once a target clicks a malicious link or downloads an infected file, malware is downloaded onto their device. Unbeknownst to the target, the malware will then begin to mine for crypto.
Once a transaction is verified using the target’s resources, the data is stored on a blockchain network and the cryptojackers receive cryptocurrency as payment. A successful cryptojacking cybercrime goes undetected by targets until the electricity or cloud service bill arrives.
Who is at risk of cryptojacking?
Anyone with an internet-enabled device can be affected by cryptojacking. That’s right — you do not have to buy, sell, trade, or hold cryptocurrency to be a target of a cryptojacking cybercrime.
Cryptojacking cybercrimes can affect both personal and business technology and are capable of infiltrating personal computers, smartphones, and tablets.
Since the goal of cryptojacking is to steal computing power without being detected, both adults and kids are equally at risk of becoming targets.
Types of cryptojacking
Before a cybercriminal can begin stealing computer power, they must first get their target to unknowingly install cryptojacking malware onto their device.
With that in mind, there are two main types of cryptojacking — via fake web content and via malicious links — and both rely on unsuspecting targets leaving their smart devices vulnerable to cybercrimes.
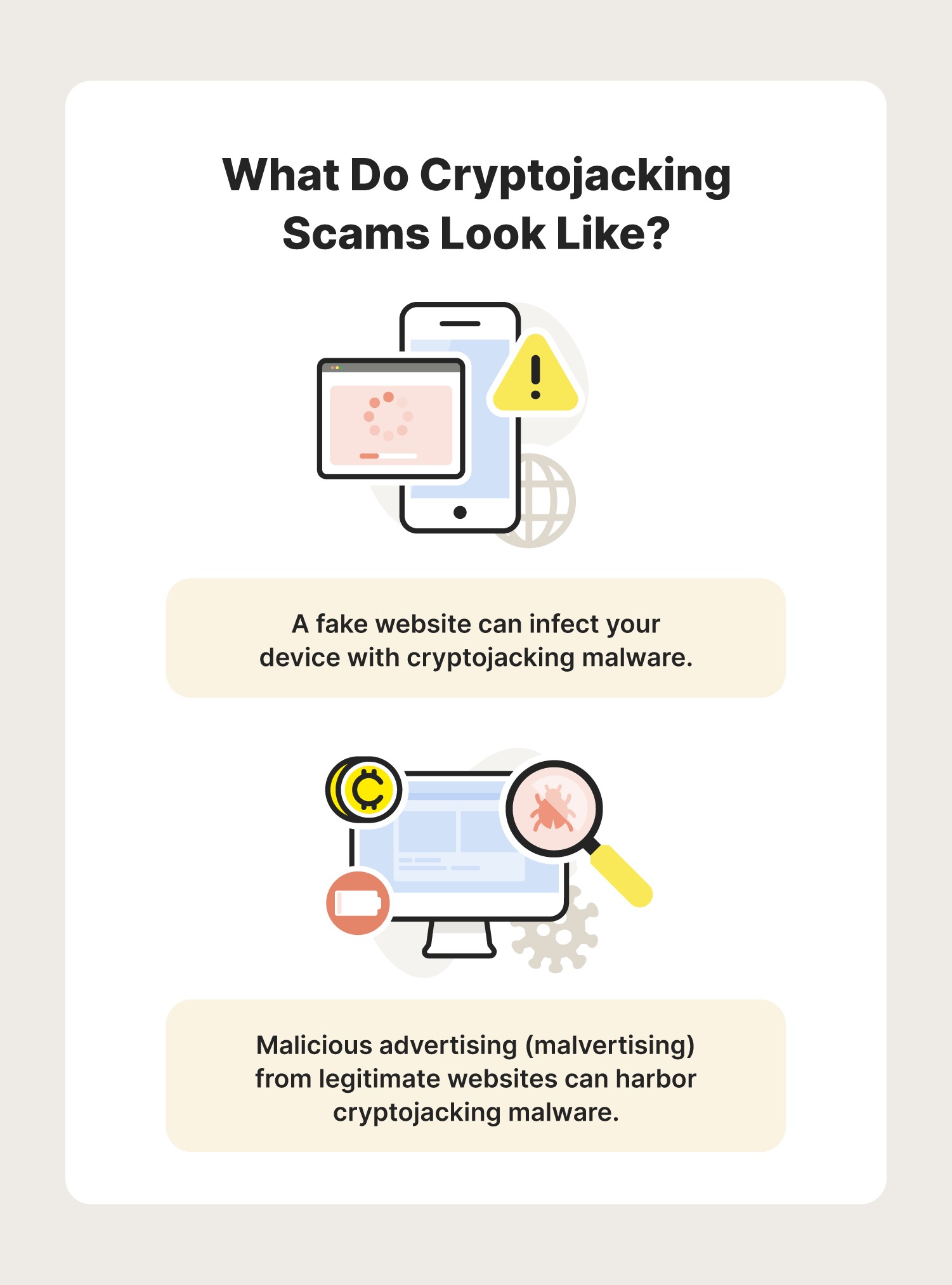
Cryptojacking via fake web content
Cryptojacking schemes that rely on infecting the web browser of their target’s device can take the form of:
- Malvertising: malicious advertising on a legitimate website
- Fake websites: scam sites designed to get targets to download malware
- Pop-unders: a hidden window designed to look like a pop-up advertisement
- JavaScript codes: embedded code that runs while targets browse the web
Browser-based cryptojacking can be extremely difficult to detect since the cybercriminals design their malware to resemble everyday advertising.
Cryptojacking via malicious links
Cybercriminals can also trick targets into downloading cryptojacking malware by using these common scam techniques:
- Phishing scams: a cybercrime that urges targets to click malicious links
- Clone phishing: a type of phishing scam that mimics a legitimate message
- Infected apps: mobile applications that have been infected with cryptojacking malware
Although these scams may appear to be legitimate, interacting with them can unleash a Trojan onto your computer network and allow cybercriminals to steal your computing power. Let’s explore how to detect cryptojacking crimes.
How to detect cryptojacking
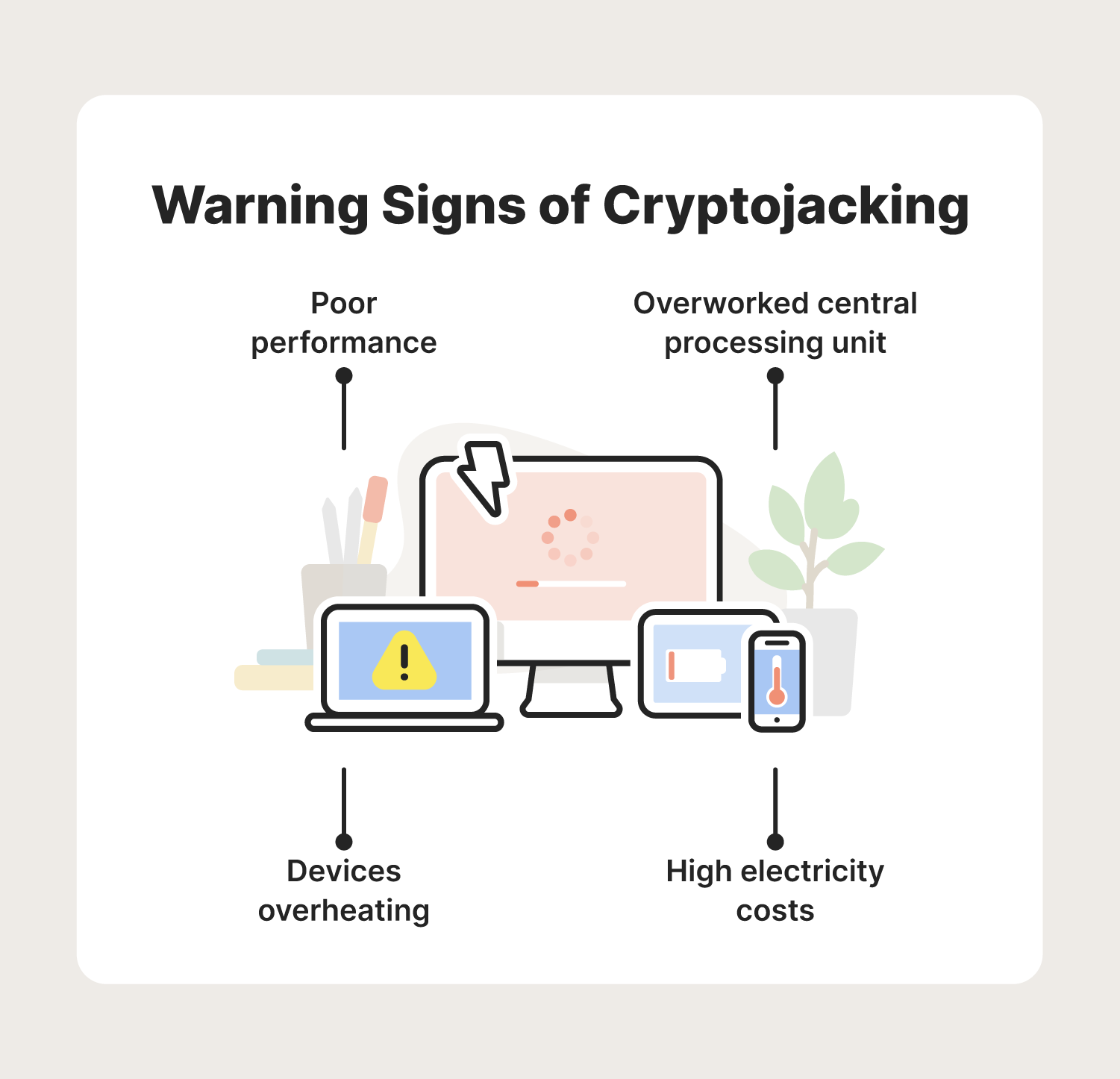
Although cryptojacking can be difficult to immediately notice, there are common warning signs that can help you detect this cybercrime:
- Poor performance: Your device is running slowly and is prone to crashing or shutting down unexpectedly from the extra cryptomining workload.
- Overheating: The fans of your device are running faster than usual and you receive a warning that your battery may overheat soon.
- Overactive CPU usage: Although you are engaging in basic tasks like web browsing, your device’s central processing unit (CPU) spikes in activity.
- High electricity costs: Your electricity bill does not match your expected electricity usage for the month.
Monitoring these elements of your mobile devices, computers, and tablets regularly can potentially help prevent cryptojacking attacks.
8 tips to prevent cryptojacking attacks
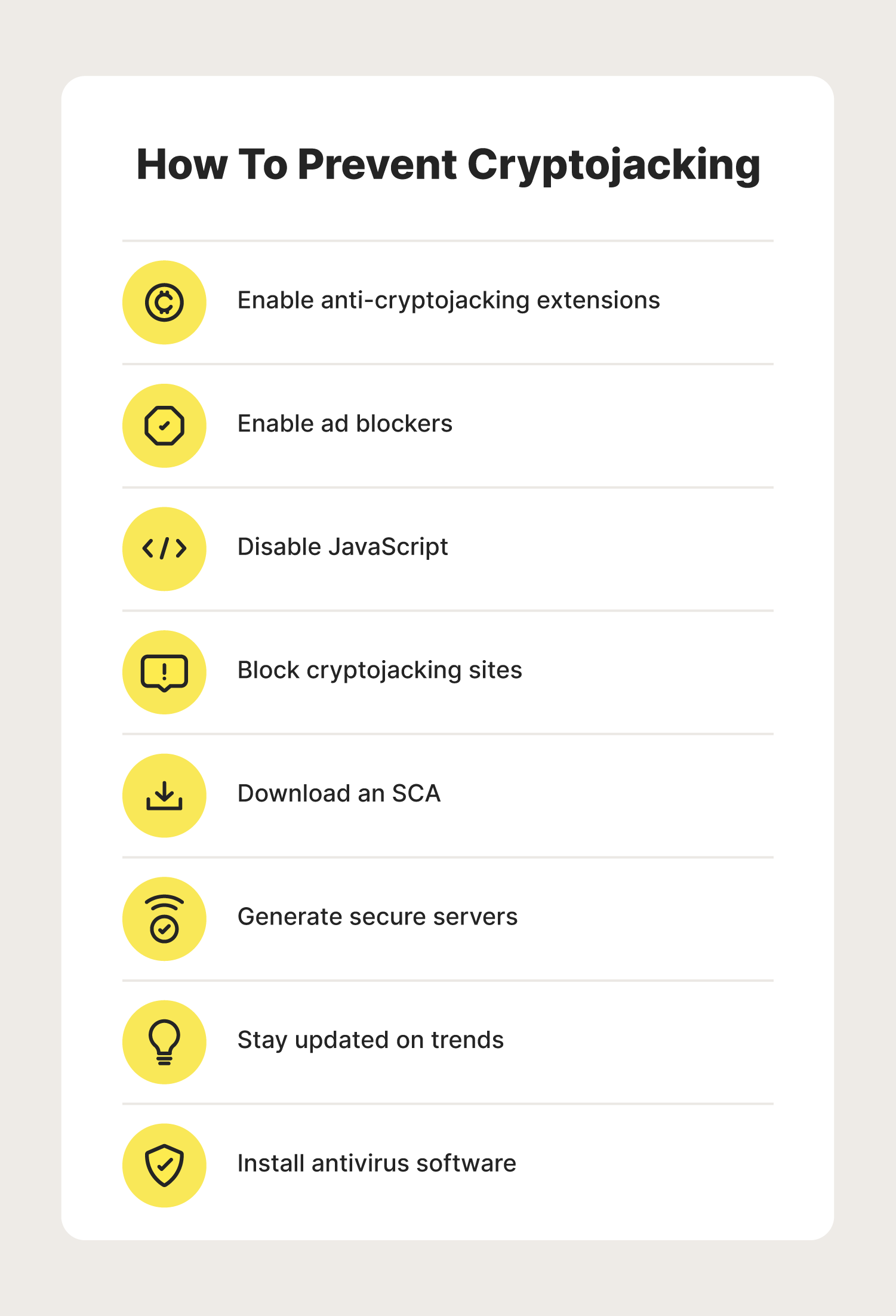
Having good cybersecurity hygiene is a proactive approach to combating cybercrimes. Follow these eight tips to prevent cryptojacking attacks:
- Enable anti-cryptojacking extensions: These browser extensions aim to detect and prevent cryptojacking malware from breaching your server.
- Enable ad blockers: Ad blockers will block all unprompted advertisements, including malvertising embedded with cryptojacking malware.
- Disable JavaScript: Disabling the use of all JavaScript code within your browser can help prevent cryptojacking script from entering your server.
- Block cryptojacking sites: Block sites that have been publicly declared as infected with cryptojacking scripts or malicious links containing malware.
- Download an SCA: Download a software composition analysis (SCA) that identifies open code that is potentially harmful to your device.
- Generate secure servers: Switch from public to private servers whenever possible to decrease the risk of exposure to cybercriminals.
- Stay updated on trends: Staying alert to the latest cryptojacking trends, scams, and malvertising techniques can help you spot red flags.
- Install antivirus software: Protect your computer against malware with the use of specialized antivirus software.
Protecting yourself online is key to avoiding becoming a target of cryptojacking attacks. Now that you know how to detect and prevent cryptojacking, consider learning how to protect yourself against other cybercrimes like identity theft.
Cryptojacking FAQs
Still have cryptojacking questions? We have the answers.
How do you detect cryptojacking?
You can detect cryptojacking by monitoring the performance, heat output, and CPU usage of your devices. Verifying that your electricity consumption matches your power bill is also a good way to detect if you are a target of cryptojacking.
Why does cryptojacking occur?
Cryptojacking occurs when a cryptominer wants to avoid high electricity fees by stealing the energy and computing power of another entity.
Is cryptomining a crime?
No, cryptomining is not a crime. Stealing electricity to illegally mine cryptocurrency for personal gain, however, is a crime known as cryptojacking.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.





Want more?
Follow us for all the latest news, tips, and updates.