Malware: what it is, how it works, and how to stop it

Malware is a real threat. With millions of new types of malware identified this year alone, protecting your personal data has never been more important. Install Norton 360 Deluxe to help you scan your system for malware, remove it, and prevent future infections.
What is malware?
Malware, short for "malicious software," is any kind of software designed to gain access to or damage a computer, usually without the owner's knowledge. Originally, software engineers created malware for experiments and pranks. Eventually, ill-willed individuals found it useful for vandalism and the destruction of targeted machines.
With almost 90 million new kinds of malware registered since the beginning of 2023 alone, there is no better time to step up your malware protection and overall cybersecurity than now.
Use this ultimate guide to learn how malware works, the varieties of malware seen on the internet, and malware attack prevention tips that can help keep your personal information and devices safe.
How do you get malware?
Users get malware when a hacker infects a device; this process typically follows three general steps:
- A hacker strategically places a malicious link, file, or attachment in front of their victim, potentially as a phishing email or other social engineering scheme.
- The victim clicks on the infected asset, unknowingly triggering the malware to install onto their device.
- The malware proceeds to steal, compromise, and/or destroy sensitive data stored on the device.
While you may download many kinds of malware from the internet, some hackers use USB sticks and flash drives to spread malware, because it’s harder for the system to detect infections that way. To avoid this tactic, never insert unfamiliar storage devices into your computer.
Malware detection tips
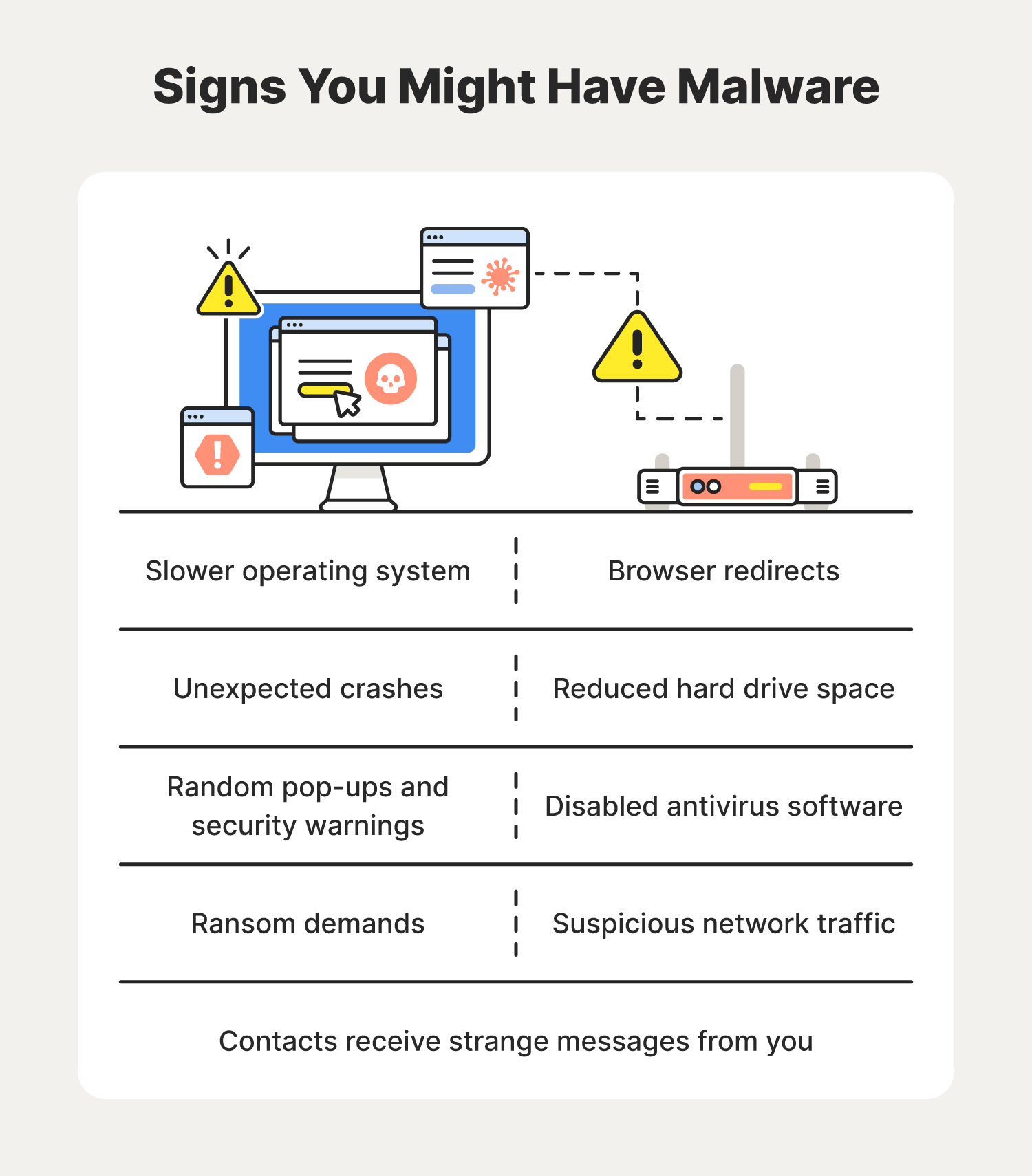
As you use your devices, keep these signs of malware in mind. Early malware detection and elimination of malicious software can save you time, frustration, and even money.
Check out the speed of your OS
If you notice a dramatic slowdown in your computer’s speed, that may be a sign that you accidentally installed malware on your device. You may also notice:
- Screen freezing
- Unexplained restarts
- Random Wi-Fi disconnects
Keep in mind that not all computers experiencing slower systems have malware infections. Sometimes, a lack of storage or skipping system updates can affect your device’s operating system.
Investigate unexpected crashes
Some system crashes have a root cause, like incompatible software or power issues. However, there are some instances where malware could be at play. If system crashes become constant, even with applications you know work for your computer, there is a chance it’s suffering from a malware infection.
Beware of pop-ups, security warnings, or ransom demands
Pop-up ads are annoying, which is why many browsers come with pop-up blockers pre-installed. If your pop-up blocker is on and you still see a flood of pop-ups on your screen, it could mean something infected your system with malware. Hackers use these malicious ads to install spyware and track your online activity.
Demands for payment displayed on your computer screen are a sure sign that your computer has malware. Hackers use different types of ransomware to take advantage of a person’s private information to make a profit for themselves.
Be skeptical of unexpected browser redirects
Though not every redirect is dangerous, some browser redirects could lead to potentially harmful websites. Hackers can send links or create browser extensions designed to automatically redirect you to their malware-infected sites. They’ll use these to collect and record your data.
Knowing the warning signs of unsecured websites can help you identify this malware attack tactic. That includes watching out for:
- Suspicious URL differences
- “http://” instead of “https://”
- Negative reviews
- Unsolicited pop-ups
Reduced storage space
Dramatic changes in your computer’s storage capacity could indicate that your device is hosting malware. Little to no space may mean that malicious software is slowly compromising files as the malware infection expands deeper into your system.
Disabled antivirus software
Hackers are smart enough to know that most people equip their devices with some type of malware protection. Their workaround was designing malware that can disable antivirus software or other security extensions that alert users of potential threats.
If you find these tools disabled on your computer, check if your device shows other signs of infection, such as a slower operating system or limited storage space.
Suspicious network traffic
A cybersecurity trick for recognizing suspicious traffic on a network involves checking your router to see which devices are using your Wi-Fi. While most of the devices you see should be yours (and maybe a neighbor who accidentally connected to your internet), there may be other devices you don’t recognize that use a lot of bandwidth. Change your password to prevent these devices from reconnecting.
Contacts receive strange messages from you
If your friends tell you about strange messages you’re sending them (other than the occasional meme), your personal phone number or email may be in the hands of a cybercriminal. Hackers might be using your phone number and stolen contacts to send phishing emails and spam texts to your contacts.
How to remove malware
There are a few methods of malware removal that you can use to eliminate dangerous software from a device. Whether you’re using a Mac or a PC, the steps are basically the same:
- Disconnect from the internet.
- Turn on Safe Mode.
- Look for malicious applications in the activity monitor.
- Use a malware scanner to find and remove these programs.
- Make sure your browser home page is correct.
- Clear the cache.
If you want to remove malware from an Android device, follow these steps:
- Disconnect from the internet.
- Turn off the device.
- Reboot in Safe Mode.
- Delete all suspicious apps.
Using security software not only makes removing malware from your devices easier, but can also help prevent infections from happening in the first place. Norton 360 Deluxe pairs trusted antivirus with a secure VPN, a password manager, and other security features to help you use the internet more securely.
Why cybercriminals use malware
The reasons hackers create and distribute malware can be as simple as trying to get money or as complicated as trying to destabilize a government. Around the world, cybercriminals use malware to:
- Steal data: The adage “information is power” can be very true. To amass power (and money), hackers deploy malware to steal secrets, ransom them to their original owners, or sell them to the highest bidder.
- Extort people: Ransomware is a perfect example of how cybercriminals use malware to make money. By encrypting and keeping an individual’s data locked, the hacker can demand payment to provide the victim with the decryption key.
- Commit corporate espionage: Some companies employ hackers to steal secrets, destroy research, or otherwise squash the competition.
- Commit sabotage: Whether committed for political or personal reasons, destroying data and compromising systems is a common use of malware.
- Mine cryptocurrencies: Mining cryptocurrency requires a lot of processing power. Malware can siphon off processing power from other people’s devices without them ever knowing it.
- Attack governments: Malware is used to cripple government infrastructure, steal or corrupt intelligence, and even destroy physical infrastructure. In 2010, the Stuxnet worm, developed by the US National Security Agency and the Israeli government, attacked Iran’s nuclear program, destroying nearly 20% of the country’s operating centrifuges.
You can do many things to protect yourself from a cybercriminal’s devious schemes, starting with learning about the categories of malware they like to use.
Common malware types
There are many different kinds of malware lurking online. Here are 14 of the most common types of malware seen on the internet:
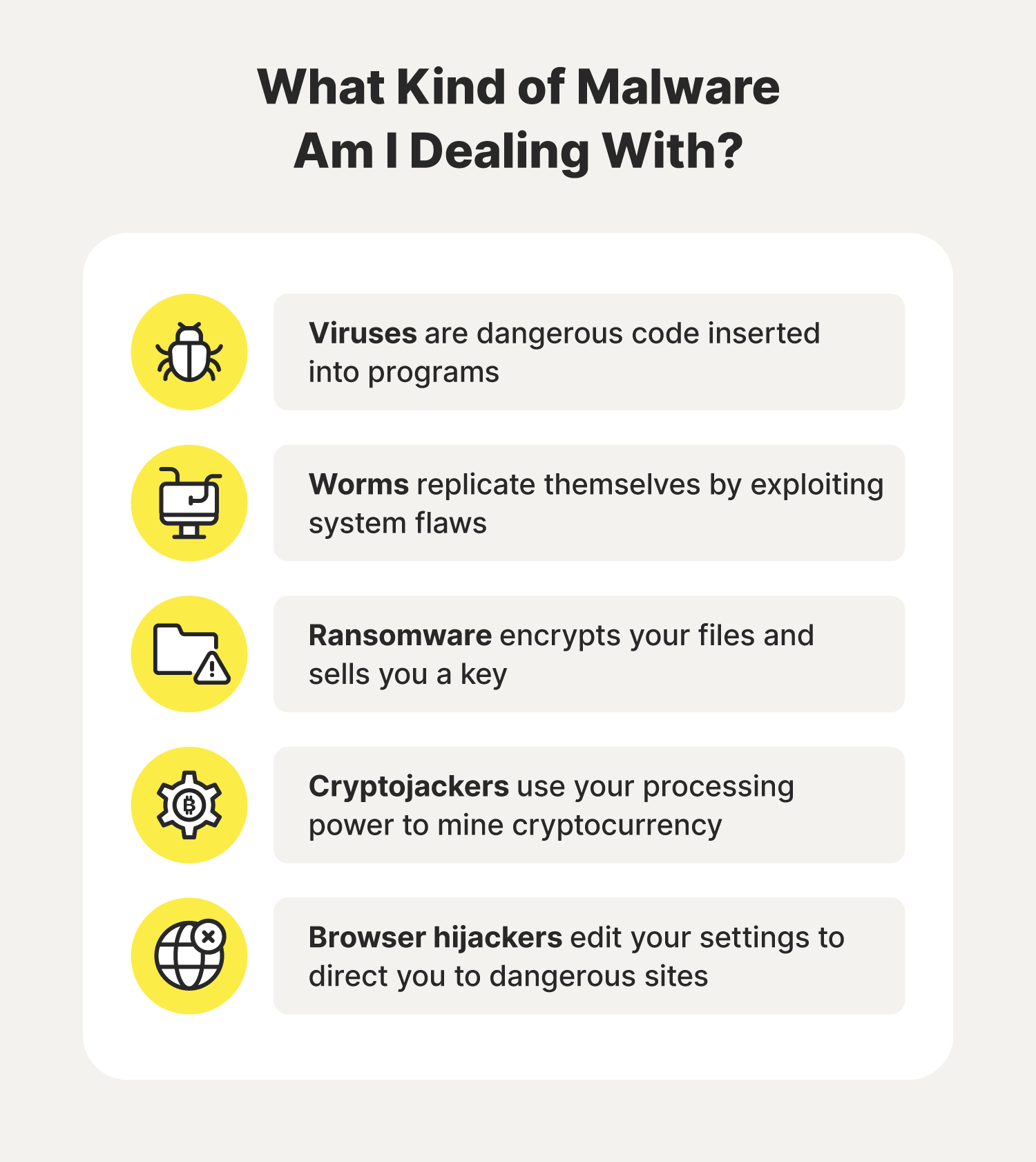
- Virus: These is a dangerous pieces of code inserted into a program or application and is often triggered by your actions.
- Worms: A worm is a type of malware infection that replicates itself and uses system flaws to make its way onto your devices.
- Ransomware: This kind of malware can lock, encrypt, and hold your data hostage before destroying your personal files unless you pay a ransom.
- Cryptojacker: To mine cryptocurrency faster, hackers create malware designed to take part of your device’s computing power to mine crypto on its behalf.
- Browser hijacker: This form of malware edits your browser's settings to get you to visit certain sites or perform other actions that the hacker wants.
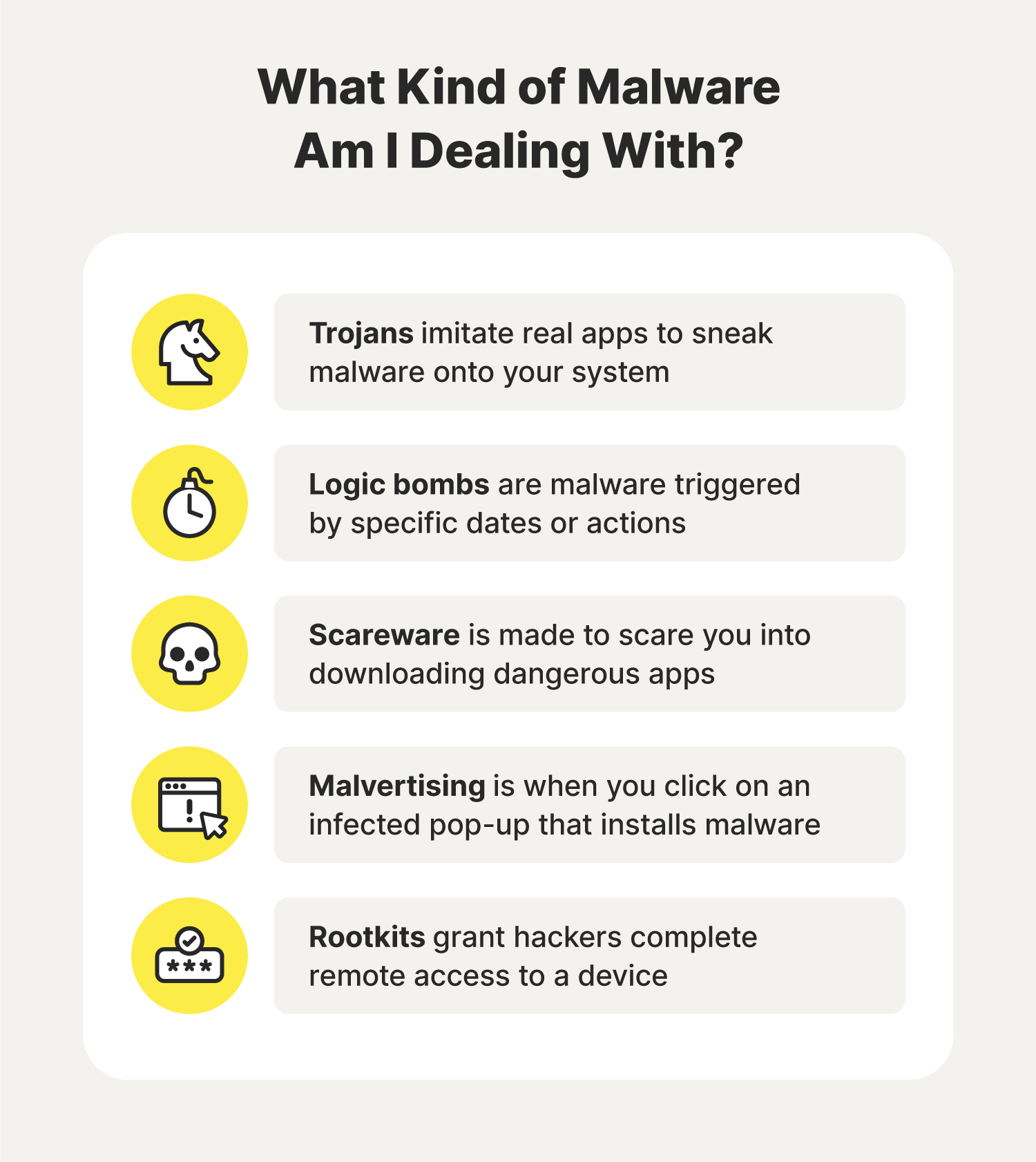
- Trojan: A Trojan imitates legitimate applications or programs to get you to download and unknowingly install malware.
- Logic bomb: A logic bomb is a type of malware that waits inside a system until you meet certain conditions or perform specific actions.
- Scareware: Scareware is designed to scare you into performing a specific action, like downloading fake security software.
- Malvertising: Infected ads loaded with malware download and install malicious programs onto your device after you click on a displayed pop-up.
- Rootkit: A rootkit is the kind of difficult-to-detect malware that grants hackers complete remote access to your device.
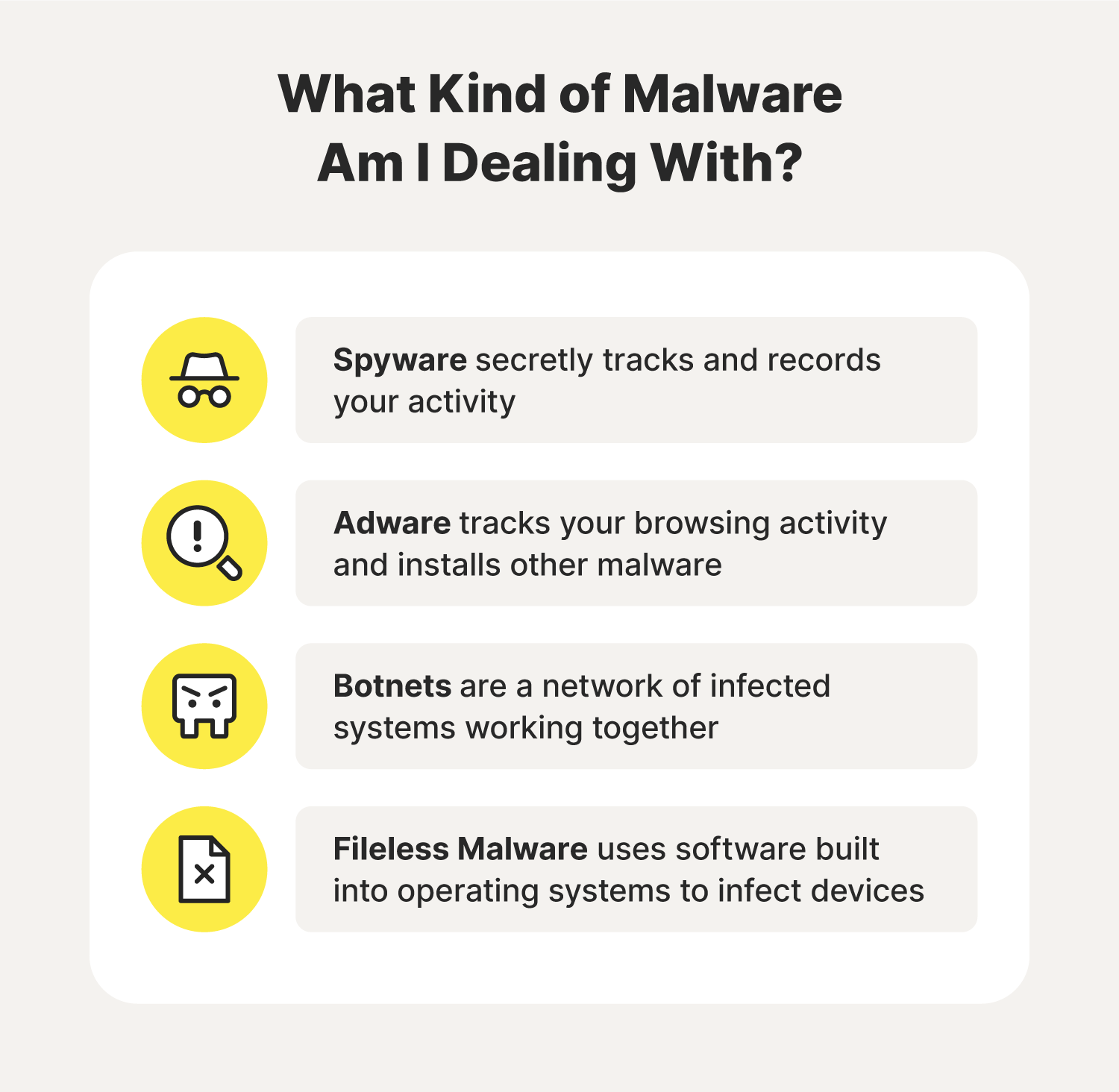
- Spyware: This type of malware secretly tracks and records your activity to learn more about you, and often tries to gain access to data or financial accounts.
- Adware: Taking the form of unwanted pop-ups, this type of malware can track your browsing activity and install other forms of malware like keyloggers or spyware.
- Botnet: These spider-like programs crawl the internet looking for security flaws to exploit by linking a network of infected systems together to further its reach and ability to do damage.
- Fileless malware: By using protocols and software already built into operating systems to infect devices, fileless malware can operate undetected for a long time as it slowly hogs your resources or steals your information.
Don’t let these malware attacks eat away at your sense of security online. There are steps you can take to protect yourself from malware.
6 malware protection and prevention tips
Malware is one of the original cyberthreats, which has given us a lot of time to learn about cyberattackers' tactics and how to use that information against them. Use these malware protection and prevention tips to stay ahead of hackers and boost your malware security.
1. Update operating systems regularly
Check your devices for software updates regularly. As mentioned, hackers often use botnets and other malware to expose zero-day exploits to compromise your devices and network.
2. Beware of suspicious links and attachments
Keeping an eye out for suspicious links and attachments may help prevent a malware attack from sneaking into your computer. These could look like URLs that don’t quite resemble what you’re used to seeing or email attachments from unknown senders. Cybercriminals love using these, in addition to other social engineering tactics, to trick you into handing over your private information.
3. Consider an ad-blocker
Cyberthieves may use pop-ups infused with spyware and/or adware to illegally track your network activity and install malware onto your device. Use an ad blocker to help get rid of pop-ups and prevent these kinds of malware attacks. This type of cybersecurity tool helps keep malicious advertisements from appearing on your screen, and, in turn, keeps you from clicking on them.
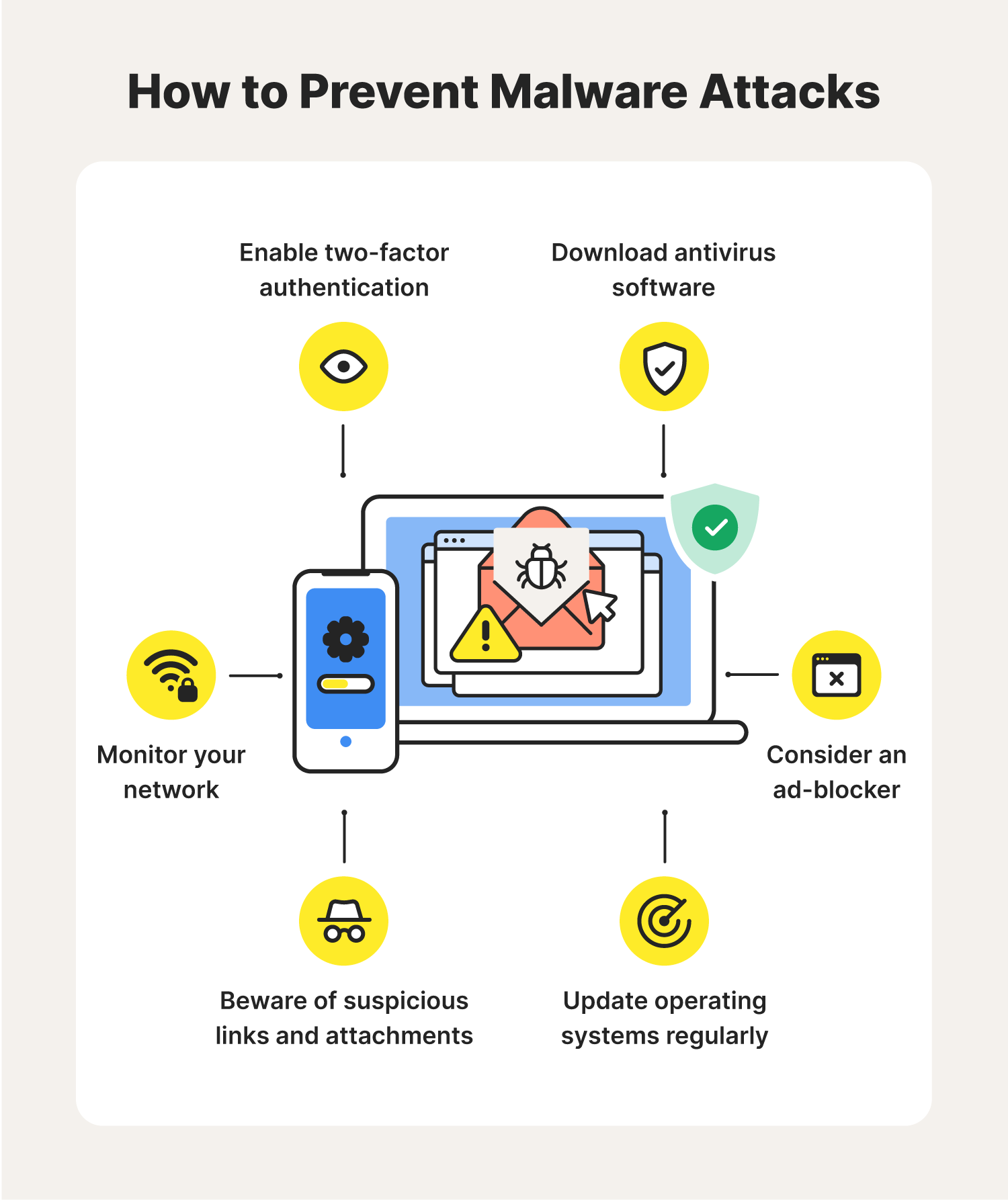
4. Enable two-factor authentication
Two-factor authentication (2FA)comes in handy if a cybercriminal can access your login credentials. Combining biometric security features, like fingerprint scanning and facial recognition, with authenticator apps makes 2FA a powerful way of guaranteeing that you’re the only one who can fully access your account. And since hackers probably won’t be able to replicate your DNA and/or facial structure, they’ll likely hit an obstacle to access.
5. Monitor your network
You can look at your network activity to see if you’re dealing with a malware infection. If you notice unfamiliar IP addresses taking up a large amount of your usage, a hacker could be trying to compromise the data on your devices.
6. Download antivirus software
Trusted antivirus software helps provide your devices with 24/7 protection against the malware attacks threatening your cyber safety. Often equipped with password managers and threat detection software, security software helps you browse more confidently, knowing you have the right cybersecurity tools working to keep you safe.
Start protecting your devices today
Norton 360 Deluxe helps protect your devices from malware and hackers by running constant scans. These scans help prevent cybercriminals from sneaking malicious software onto your computers and phones. Norton 360 Deluxe also includes a VPN for safer, more private surfing and a password manager that helps you create and securely store stronger, better passwords.
FAQs about malware
Check out some of the most commonly asked questions about malware to help protect against malware attacks.
Can malware spread through Wi-Fi?
Yes, malware can use Wi-Fi and other wired, wireless, and Bluetooth connections to spread and infiltrate devices.
How do I find hidden malware?
Use antivirus software to identify malware that may be hiding on your personal computer or other devices.
How do I know if I have malware on my phone?
There are several signs that your phone may have malware:
- You have apps you never downloaded
- Your phone slows down
- Apps take longer to start
- You’re using a lot more data than normal, even though your habits haven't changed
- Uncontrollable pop-up ads start appearing

Cyber threats have evolved, and so have we.
Norton 360™ with LifeLock™, all-in-one, comprehensive protection against viruses, malware, identity theft, online tracking and much, much more.
Try Norton 360 with Lifelock.
Is malware a virus?
A virus is just one type of malware. In fact, malware encompasses many types of malicious software, including viruses, spyware, ransomware, adware, zip bombs, botnets, cryptojackers, and more.
Can Macs be affected by malware?
Mac users are not immune from viruses and malware. No matter what kind of device you have, it can be infected with malware.
Can smartphones and tablets get malware?
Yes, tablets and smartphones can get malware. Whether you use an Apple device or Android, there is malware that can affect your tablet or smartphone.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.






Want more?
Follow us for all the latest news, tips, and updates.