Spear phishing: A definition plus differences between phishing and spear phishing
Not to be confused with an aquatic hunt on a tropical vacation, spear phishing is a targeted cyberattack toward a specific individual or organization with the end goal of receiving confidential information for fraudulent purposes.

Not to be confused with an aquatic hunt on a tropical vacation, spear phishing is a targeted cyberattack toward a specific individual or organization with the end goal of receiving confidential information for fraudulent purposes.
Per the name, it’s a form of phishing — and a popular one that, with 65 percent of all known cybercriminal groups apparently using this bespoke approach to gather compromising information for victims.
Of course, to fully understand spear phishing, you have to first understand phishing itself. Here’s an overview of the differences between phishing and spear phishing, including a spear phishing definition, along with what helps protect you from spear phishing.
What is spear phishing?
Spear phishing is an ultra-targeted phishing method whereby cybercriminals — or spear phishers — pose as a trusted source to convince victims to divulge confidential data, personal information, or other sensitive details. The cybercriminal will then use this information for malicious purposes, including identity theft or data breaches.
Spear phishers often prey on their victims via targeted emails, social media, direct messaging apps, and other online platforms. And the strenghth of these cyberattacks is that they’re tailor-made for victims and grounded in quality over quantity.
That’s because spear phishers do a great deal of reconnaissance, meaning research or homework, to be able to pull off a disguise of a trustworthy source. And that’s one of the biggest differences between traditional phishing and spear phishing.
Spear phishing vs. phishing
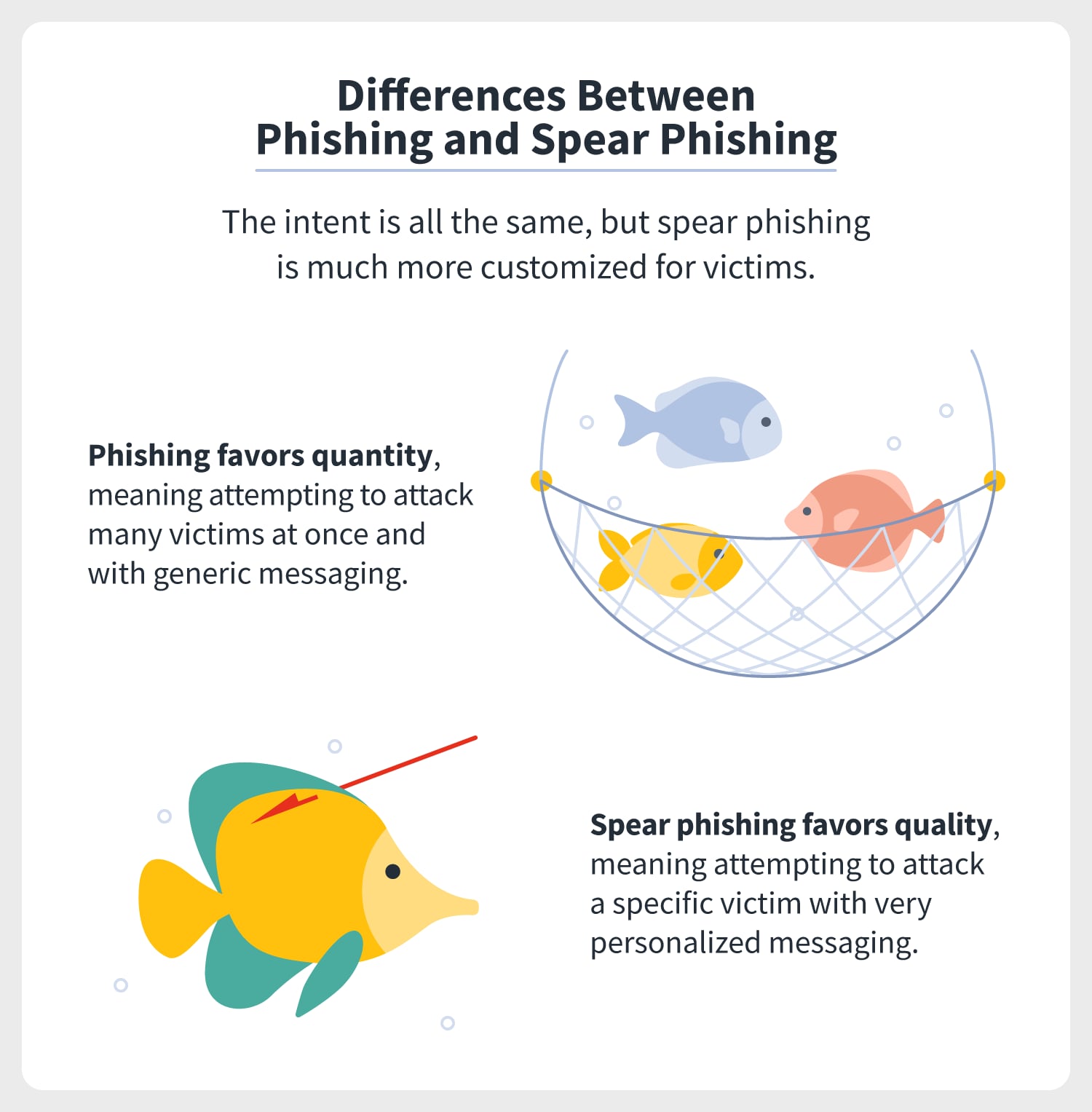
Spear phishing is different from phishing in that it’s a cyberattack toward a specific individual or organization, whereas phishing is a more generic, automated cyberattack that’s attempted in one sweep of a large group. You might think of phishing as casting a wide net over a school of fish, whereas spear phishing is using a spear to catch one single fish.
Phishing emails might be sent to hundreds of recipients simultaneously with little customization. Spear phishers, however, will pose as a friend, boss, family member, or enterprise to gain your trust and fool you into giving them your information. These emails are well-researched and personal, making it harder to distinguish between what is real and what is fake.
Ultimately, the intent of phishing and spear phishing is the same — acquiring confidential data or sensitive information for malicious purposes. Still, victims, much like consumers, can be more susceptible to a customized
experience, which in this instance is spear phishing.
How spear phishing works: 3 examples
Spear phishing happens — and is successful — through reconnaissance, meaning cybercriminals studying up on victims to pull off a trustworthy identity such as friend, boss, coworker, or family member. In fact, hacktivists and government-sponsored hackers are often identified as being behind spear phishing attacks.
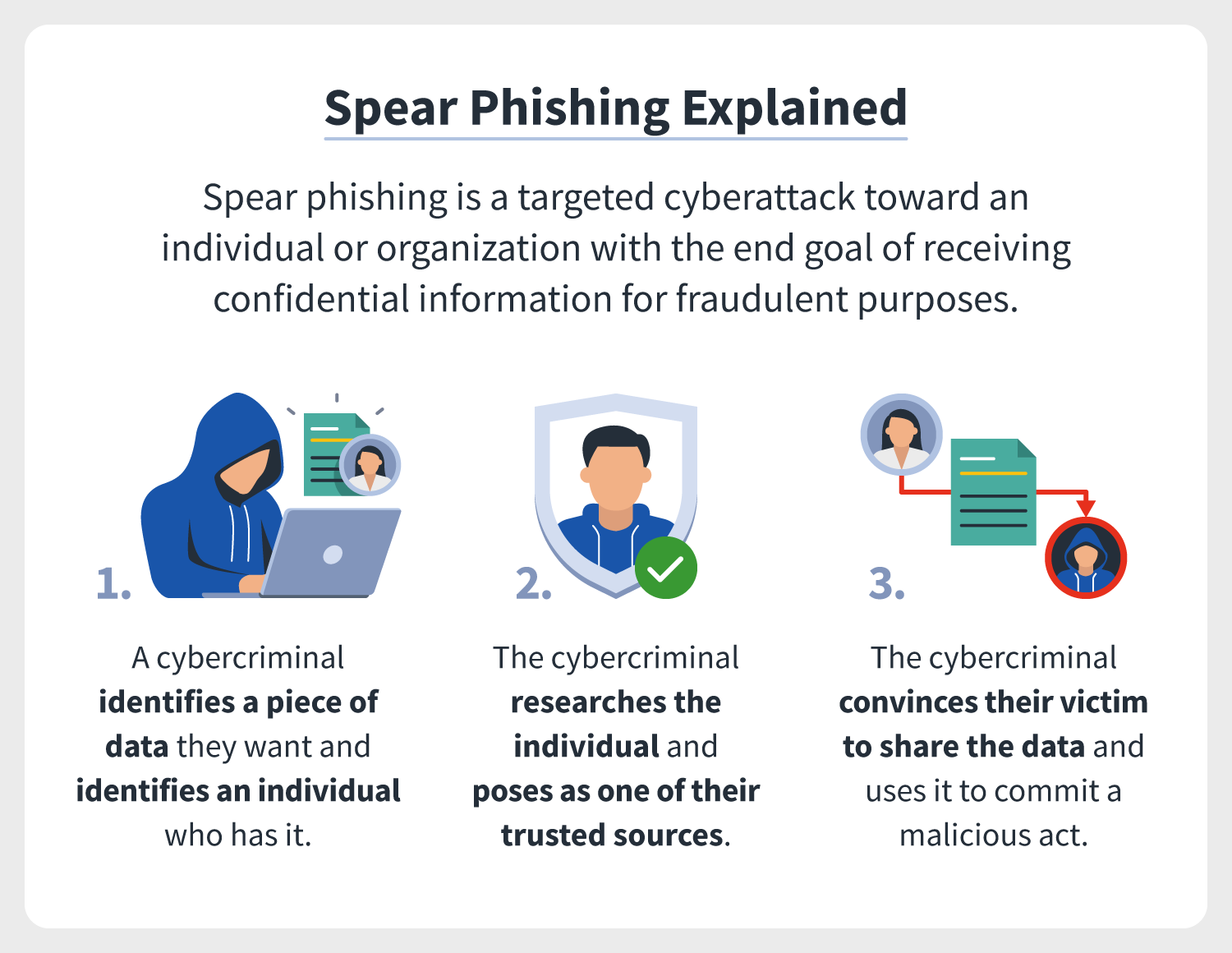
So, how do spear phishing attacks work? They can be summed up into a few steps:
- The spear phisher identifies a piece of data they want, whether that’s personal identifiable information like a Social Security number or payment methods, or usernames and passwords.
- The spear phisher identifies who has the piece of data by conducting research on an individual or organization, scoping out public profiles on social media or company websites.
- The spear phisher also researches the cybersecurity protections their victim has in place, including antivirus software, and any holes they can exploit.
- The spear phisher creates an email and maybe even domain name resembling the source they’re posing as and will craft a personal message to their victim. The message oftentimes has an urgent request and is sent as an email, via social media, a phone call (vishing), or text message (smishing).
- The spear phisher convinces their victim to divulge the piece of data they asked for and use it to commit a fraudulent act.
Of course, spear phishing techniques can differ. Here are just a few spear phishing examples to consider.
1. CEO fraud scams
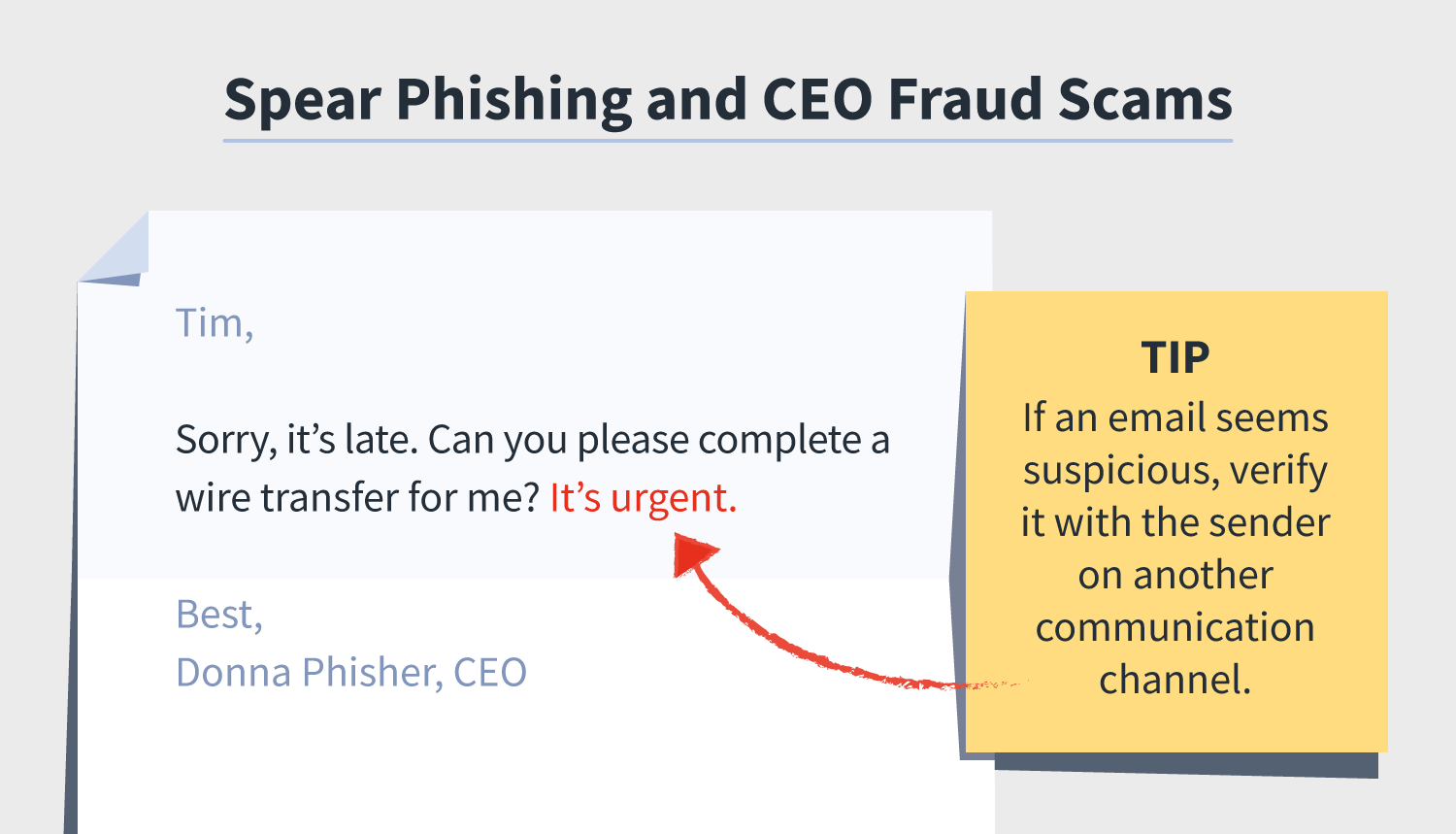
Not to be confused with whaling, which is a phishing attempt targeting a C-suite executive, CEO fraud scams can be considered a type of spear phishing in that cybercriminals pose as a C-suite executive to get an employee to fulfill an urgent request or divulge important data.
For instance, a “CEO” might be emailing an employee on a weekend and asking you to complete a wire transfer to a contractor. When, in fact, if the employee completes the transfer, they could be transferring company funds to the spear phisher.
2. Malicious attachments
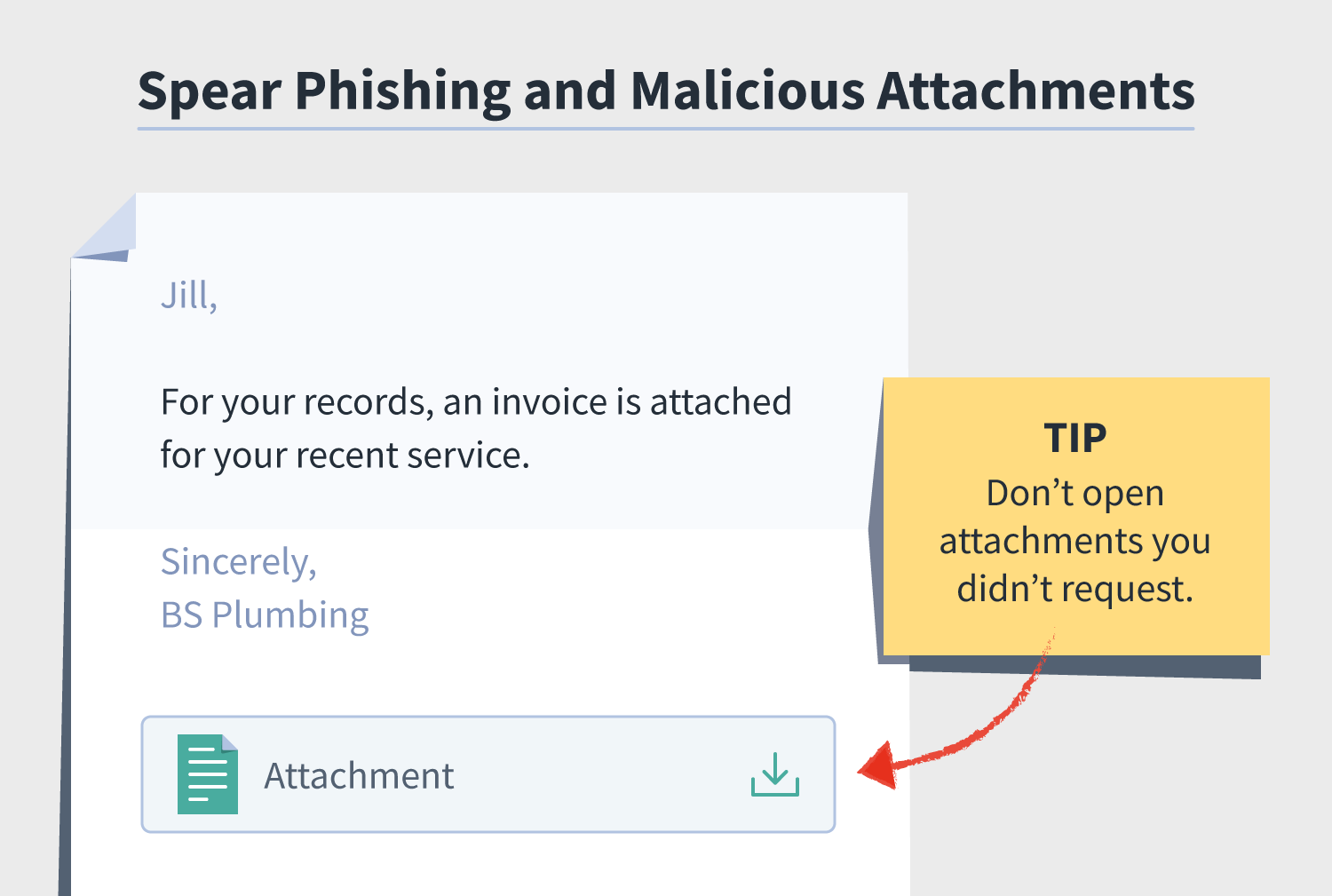
It’s not always the case that spear phishers just want you to hand them their desired data. Instead, they might want to watch you divulge the data on your own time and will do this via malware attachments.
For instance, a spear phisher might pose as a service provider sending you an invoice attached to an email. When, in fact, once you click that attachment, malware or a keylogger that traces your activity is downloaded onto your device.
3. Ransomware
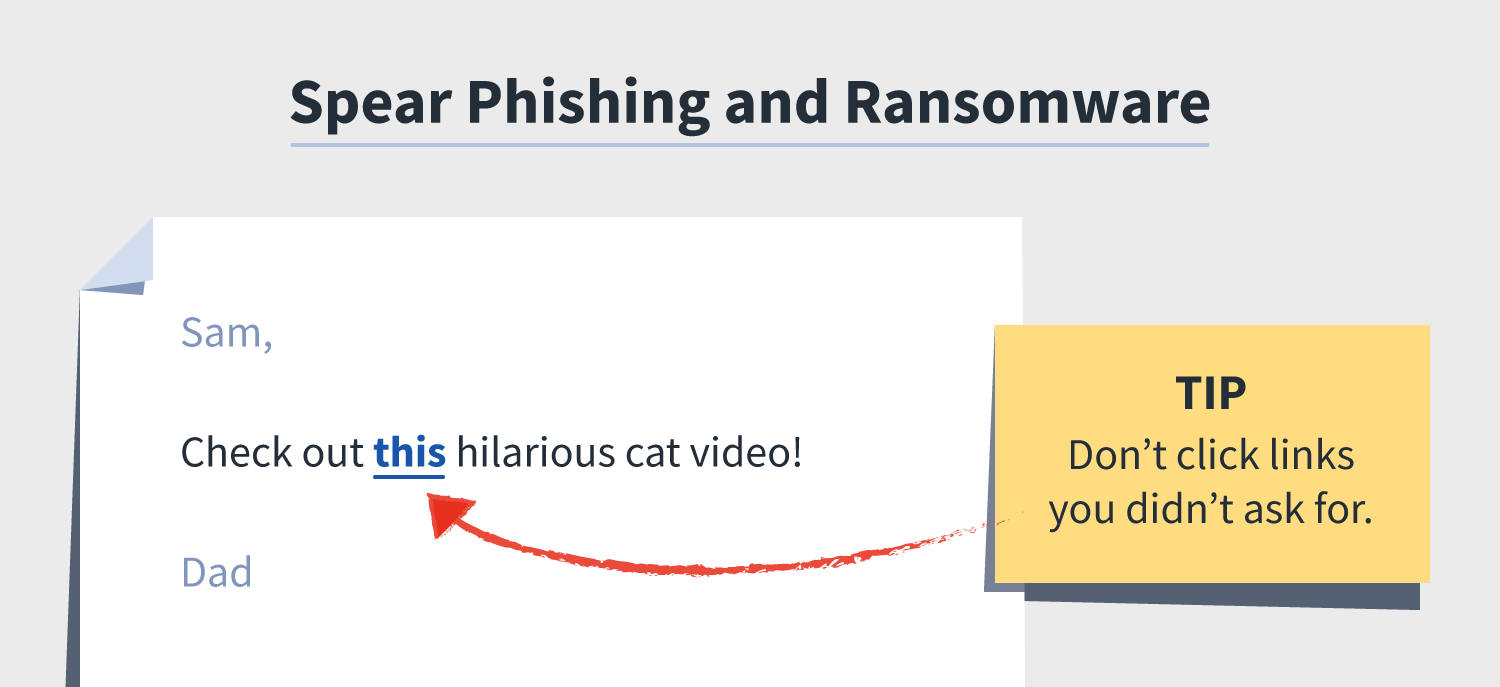
Some spear phishers might pair up their advances with ransomware — meaning, they might hold your device or sensitive information hostage until a ransom is paid.
For instance, a spear phisher might pose as a friend or family member messaging you a link to a “funny video” they found online. When, in fact, once you click the link, you’re informed that your device is no longer yours and you must pay up to get it back.
How effective spear phishing really is
Spear phishing is an effective cyberattack for individuals and organizations alike. And no one seems immune to them. Spear phishing attacks have even been attempted on presidential campaigns and nonprofits. In 2020 alone, 75 percent of organizations around the world experienced a phishing attack, including 35 percent experiencing spear phishing.
And the consequences can be dire, leading to manipulated stock prices, espionage, hijacked computers, also DDoS attacks.
Success rates can depend on how much reconnaissance and customization goes into the spear phishing attack. To this degree, you might consider spear phishing an extension of social engineering.
8 tips to protect yourself from spear phishing

Help avoid falling victim to spear phishing with these helpful tips, beginning with exercising caution with all your online activities.
1. Check sender addresses
Though a spear phishing email looks generally like a regular email from a friend or business, there are several ways to mark it as something more sinister.
Spear phishers can usually mimic the name of a person or organization you get emails from regularly but might be unable to perfectly mimic their tone. If you think an email might be suspicious, check the sender’s email address — typically, there will be subtle changes, such as the letter “o” replaced with a “0.”
2. Verify links
If an email includes a hyperlink, a quick way to check its legitimacy is to hover over the URL. Once your mouse hovers over the link, the full URL that is being linked to will appear. If it seems suspicious, don’t click it.
In addition, recognize you needn’t click on a link you didn’t ask for. Instead, go directly to a website to find a link yourself.
3. Try another communication channel
Spear phishing emails are sent under the guise of a friend or a trusted person. If you think it’s odd that a friend would be emailing you to ask for your password or username, use another form of communication like a phone call, text, or face-to-face conversation to ask your trusted source if the ask is legit. Keep in mind, you shouldn’t share passwords or usernames.
4. Keep your personal information close
Sure, not sharing sensitive data or personal information in all online interactions is among the more surefire ways to avoid spear phishing. But also not oversharing online via your social media accounts or even in bios on company websites can make it harder for spear phishers to conduct reconnaissance for their cyberattack.
You can also adjust your privacy settings across your devices and social media accounts to ensure only those you want to see your information can. Regularly take inventory of your online profiles and reset your privacy settings as you see fit.
5. Sign up for accounts sparingly
There’s a lot of information about you on the internet. Each time you make a social media post or fill out a quiz, for example, more of your personal information is uploaded to the web. Before you know it, things from your hometown to your pet’s name might have found their way online, onto data brokering sites, or in the hands of spear phishers.
Don’t sign up for apps, social networks, giveaways, or other accounts unless they’re absolutely necessary.
6. Keep your software updated
Beyond considering antivirus software that can flag phishing attempts, be sure this software and your devices’ operating systems are up to date. When your applications are up to date, it’ll make it harder for a spear phisher to
get through since updates often patch security holes.
7. Stay suspicious of the signs of spear phishing
It’s important to protect your data and a company’s data. Recognizing the characteristics of spear phishing can help:
- Urgent requests
- Strangely worded messages from a “trusted” source
- Links or attachments you didn’t request
- Asks for personal information
And if you think an email seems suspicious, trust your gut and investigate it further. In addition, mark the message as spam to avoid being contacted again and set your spam filters to a high protection level.
8. Know how to react
It can be easy to get duped by spear phishing attacks. If you do click on a phishing link in an email or download a suspicious attachment, here’s what to do next:
- Disconnect from the internet: Turning off your Wi-Fi or pulling out your ethernet cable can help stop the immediate spread of malware.
- Backup your files: It’s smart to frequently back up your files, but in the event of a spear phishing attack it becomes more crucial. Backup your important files to an external source so you’ll still have them if the cybercriminal deletes your data.
- Change your passwords: Once a hacker gains access to one of your accounts, they can work their way through others. If you think an account has been compromised, change all of your passwords as soon as possible and consider opting for two-factor authentication where possible.
- Scan your hardware: Using security software can help identify and eradicate the threat.
Becoming the victim of a spear phishing attack can feel invasive and unsettling, on top of leaving you with the clean-up task. It could take weeks or months to restore your internet security.
With vigilance and a few precautions, you can reduce your risk of being an easy target of these targeted cyberattacks.

Cyber threats have evolved, and so have we.
Norton 360™ with LifeLock™, all-in-one, comprehensive protection against viruses, malware, identity theft, online tracking and much, much more.
Try Norton 360 with Lifelock.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.



Want more?
Follow us for all the latest news, tips, and updates.