What is a VPN concentrator and how does it work

With the rise of digital technology, and in the wake of COVID-19, millions of people now work remotely. That means that VPN concentrators, which help keep remote working smooth and secure, are becoming more important than ever. Read on to learn more about VPN concentrators and how they work. Then, discover other types of VPNs, like Norton Secure VPN, that are better suited for personal use.
What is a VPN concentrator?
A VPN concentrator is a hardware networking device that creates multiple, simultaneous VPN connections to the same network. This allows individuals in different locations to access a central corporate network, which makes VPN concentrators especially useful for larger organizations with remote workers and two or more offices.
What does a VPN concentrator do?
A VPN concentrator creates multiple encrypted tunnels that secure internet traffic over a network, with the possibility of creating multiple VPN tunnels for a single network. VPN concentrators also encrypt and decrypt data sent over a network, assign IP addresses to users, and authenticate users accessing a central network.
Because VPN concentrators enable users from multiple locations to securely access a single network, they help organizations manage a large remote workforce that may be connecting to a certral network from various cities or countries around the world.
While VPN concentrators have a lot of benefits, they also have some downsides. Below, we review the pros and cons of a VPN concentrator.
| Pros | Cons |
| Quickly generates numerous VPN tunnels | Expensive |
| Strengthen remote access security | Can increase lag |
| Efficiently connects a large number of remote workers to an organization’s network | Complex setup |
| Centralizes management of multiple VPN connections | Single point of failure, so if the VPN concentrator fails, all the other network connections fail |
Organizations with a lot of remote workers or multiple office locations gain the most from a VPN concentrator. But, companies need to carefully invest in the hardware and software infrastructure to bear the expected load, and they need to establish strong cybersecurity safeguards to ensure the myriad connections that a VPN concentrator enables remain private.

A VPN hides everything employees do online, protecting both individuals and the companies they work for.
As more people working remotely, cybersecurity has become a crucial issue for businesses. The number of people working from home in the United States tripled between 2019 and 2021, from roughly 9 million people to more than 27 million people. With so many workers logging on remotely, solutions like VPN concentrators that help secure remote connections have become critical.
Popular VPN concentrators
There are a few VPN concentrators that have made a name for themselves recently. Prices and services vary, so it’s best to research thoroughly before choosing the right provider for your business.
- Cisco Meraki is a leading IT software and service provider and a major producer of VPN concentrators. Cisco’s primary clientele are large businesses and organizations, many of which aren’t IT-oriented, so Cisco’s VPN concentrators are designed to be simple to set up and provide a large number of connections.
- ShoreTel (now owned by Mitel) specializes in mobile communications, so its VPN concentrator is designed to set up a remote telephony network with VPN encryption.
- Aruba provides various products that can be configured as VPN concentrators.
VPN concentrator alternatives
If you find that VPN concentrators are too complicated to set up or out of your price range, or if you’re looking for a personal VPN, there are alternatives. Perhaps you run a smaller organization and don’t need the massive scale that a VPN concentrator offers. Below we explain some alternative VPN connectors to choose from.
VPN concentrator vs. VPN client
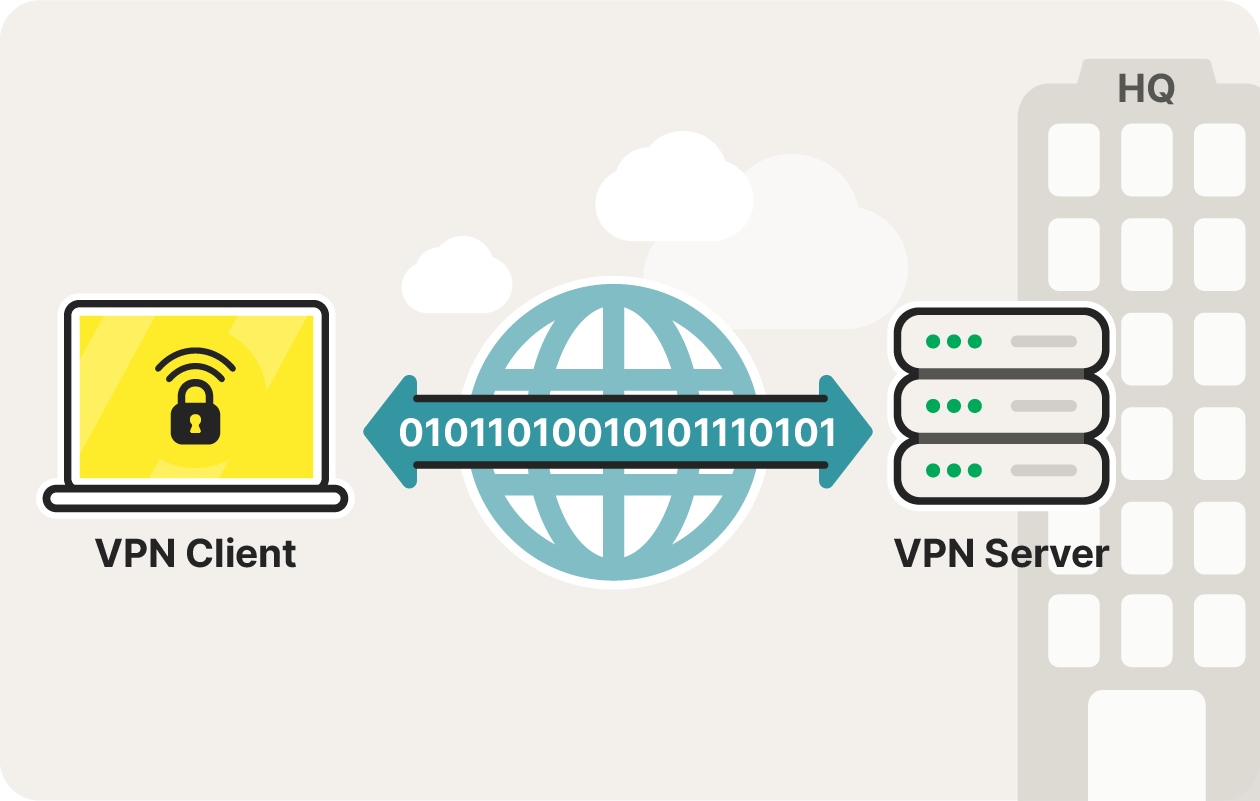
A VPN client is software on your device that securely connects you to a VPN server.
If you don’t want to add new hardware to your network setup, you can use a VPN client. Unlike a VPN concentrator, a VPN client is software that connects a single user to a VPN server. So a VPN client works like a VPN that many people use at home.
Unlike VPN concentrators, VPN clients are software, so they’re easier to set up than VPN concentrators. But, VPN clients are more difficult to scale, so if multiple people are connecting to a single corporate network, VPN clients may lead to lag and other connectivity issues.
But for individual users, households, and small companies, VPN clients are reliable tools that help safeguard your internet connection — and they’re very easy to set up and use. With Norton Secure VPN, you can encrypt your internet connection in just a few clicks.
VPN concentrator vs. VPN router
VPN routers encrypt the traffic of each connected device, similar to a VPN concentrator. It’s usually trickier to set up a VPN router than a VPN client, because you have to configure the router, unless you buy one with a VPN pre-installed. Depending on how many locations you need to service, setting this system up could take some time.
As VPN routers are generally configured to secure a limited number of devices, they can’t be scaled easily and may not be the best solution for certain office setups. A VPN router also only encrypts the communications of devices that are connected to the internet through that router. So this solution won’t help employees who travel, have off-site meetings, or work remotely. However, a VPN for iOS can provide a secure connection for those using Apple devices outside the office environment.
VPN concentrator vs. site-to-site VPN
A site-to-site VPN, or router-to-router VPN, establishes a secure tunnel between two or more separate networks. These networks may share similarities to one another, especially in the case of businesses. Site-to-site VPNs may be used by a company with multiple offices in order to connect their networks.
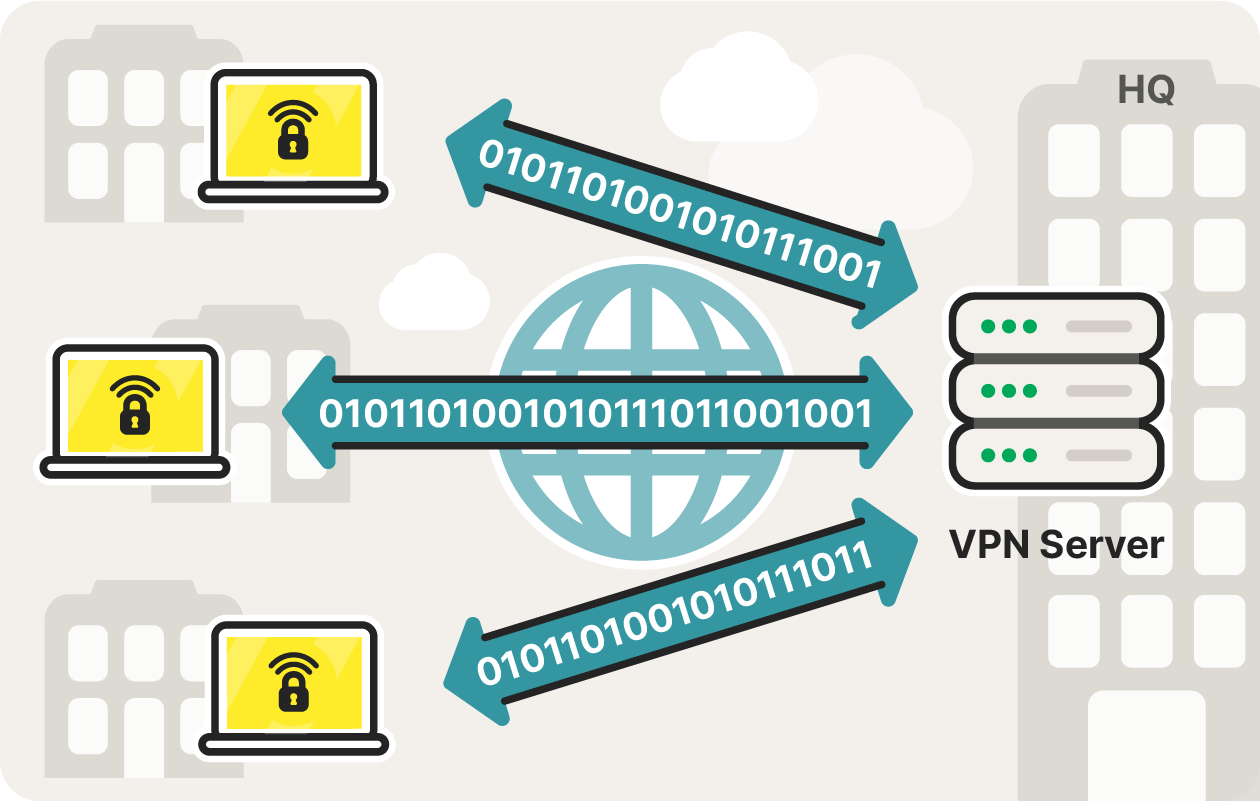
A site-to-site VPN is used when an enterprise has multiple locations to connect
Like VPN concentrators, site-to-site VPNs are often difficult to configure and require some network administration knowledge. The configuration of a site-to-site VPN involves defining the necessary parameters for entire networks to connect to each other.
VPN concentrator vs. IPsec encryption
IPsec stands for Internet Protocol (IP) security, and it refers to a suite of protocols that secure data traveling over IP networks. A regular internet connection doesn’t use IPsec.
Most VPN concentrators use IPsec encryption to protect data as it travels through a VPN tunnel. It gives end-to-end encryption by scrambling data at the transmitting device and unscrambling it at the receiving end.
Access the internet more securely with Norton Secure VPN
A VPN concentrator isn’t for everyone, especially for individuals and households. If you want protect a more limited number of devices, then a VPN client is likely your best bet. Norton Secure VPN is a powerful VPN client with bank-grade encryption, and it’s refreshingly easy to set up. Plus, it can be configured on up to 10 devices.
Whether you’re browsing the web, shopping, or banking online, get Norton Secure VPN to help keep your personal information private.
FAQs about VPN concentrators
VPN concentrators are a great solution for businesses, so you may have further questions about how they work. Here are the most frequently asked questions about VPN concentrators.
Which VPN concentrator protocol is the best?
As VPN concentrators are typically used to connect different users across different networks to a single one, a scalable protocol is best. IPsec is highly scalable, as it works to connect multiple users to a single network. Any VPN concentrator that uses OpenVPN as its default protocol is also a solid option.
Why use a VPN concentrator?
VPN concentrators can connect multiple users remotely to a central network, allowing them to access sites and services that they otherwise wouldn’t be able to. At the same time, the setup ensures a secure and private connection. If you run a large organization with remote workers and various office locations, a VPN concentrator is a security solution worth looking into.
Where should a VPN concentrator be installed?
A VPN concentrator can be installed parallel to or behind the firewall of the main network. As a VPN concentrator solution includes hardware and software, it should be installed in the same area as the main network that will require the VPN for remote access.
How much do VPN concentrators cost?
VPN concentrators can cost anywhere from around $200 to well over $1,000. Prices vary due to the manufacturer, performance, and capacity of the concentrator. VPN concentrators that can support hundreds or thousands of tunnels will cost more than those that can support only a few dozen connections.
Do VPN concentrators impact internet performance?
VPN concentrators, just like any type of VPN, can impact internet performance, as any request is routed through the VPN and encrypted, which takes more time than connecting directly.
The increased latency due to the way VPNs are set up can lead to lagging page load times or dropped requests altogether. But in most cases, the speed is only slightly slower than before. And a slightly slower connection is often a price worth paying for a more secure connection.
Who uses VPN concentrators?
Large organizations with a lot of remote workers often use VPN concentrators to ensure their employees can securely connect to their central corporate network. VPN concentrators are meant for large-scale use and have a corresponding cost and capacity.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.


Want more?
Follow us for all the latest news, tips, and updates.