What is a remote access Trojan? A cybersecurity guide

Trojan attacks are some of the most nefarious cybersecurity threats, and remote access Trojans (RATs) that give hackers total control over your device are especially dangerous. But knowing how a remote access Trojan works — and how to detect one — can help protect you from an attack, especially when combined with robust security software like Norton 360 Deluxe.
What is a remote access Trojan (RAT?)
A remote access Trojan (RAT) is a type of Trojan cyberattack that gives a hacker remote access to your device. Disguised as a harmless file or application, a RAT opens a backdoor to your device via a network, putting your data, security, and identity at risk.
In a standard Trojan attack, malware is disguised and packaged into a seemingly innocuous or even helpful file or app to trick you into unknowingly installing the malware onto your device.
A remote access Trojan is a specific type of Trojan attack that gives intruders unrestricted access to your device. They can take control of your hardware (such as your webcam) and software, or even access personal information like your financial accounts, Social Security number, or credit card details. Essentially, remote access Trojans can exploit your device in a variety of ways, and you may never know what’s happening.
How remote access Trojans work
RATs work like other Trojan attacks, meaning hackers get them on your device by manipulating or tricking you into compromising your security by installing malware that looks harmless. But how do they trick you into doing this? And how does the Trojan let hackers take control?
What the experts say
"On desktops, Remote Access Trojans like Wincir remain active… (but) today’s mobile threats remain mostly scam-driven rather than exploit-driven." - Gen 2025 Threat Report
Threat Research Team, Gen
Hackers typically disguise Trojan malware as something you want — an app, a program, or a download — so that you install it on your computer voluntarily. The RAT may be hiding in a phishing email, a torrent from the internet, or an enticing web link.
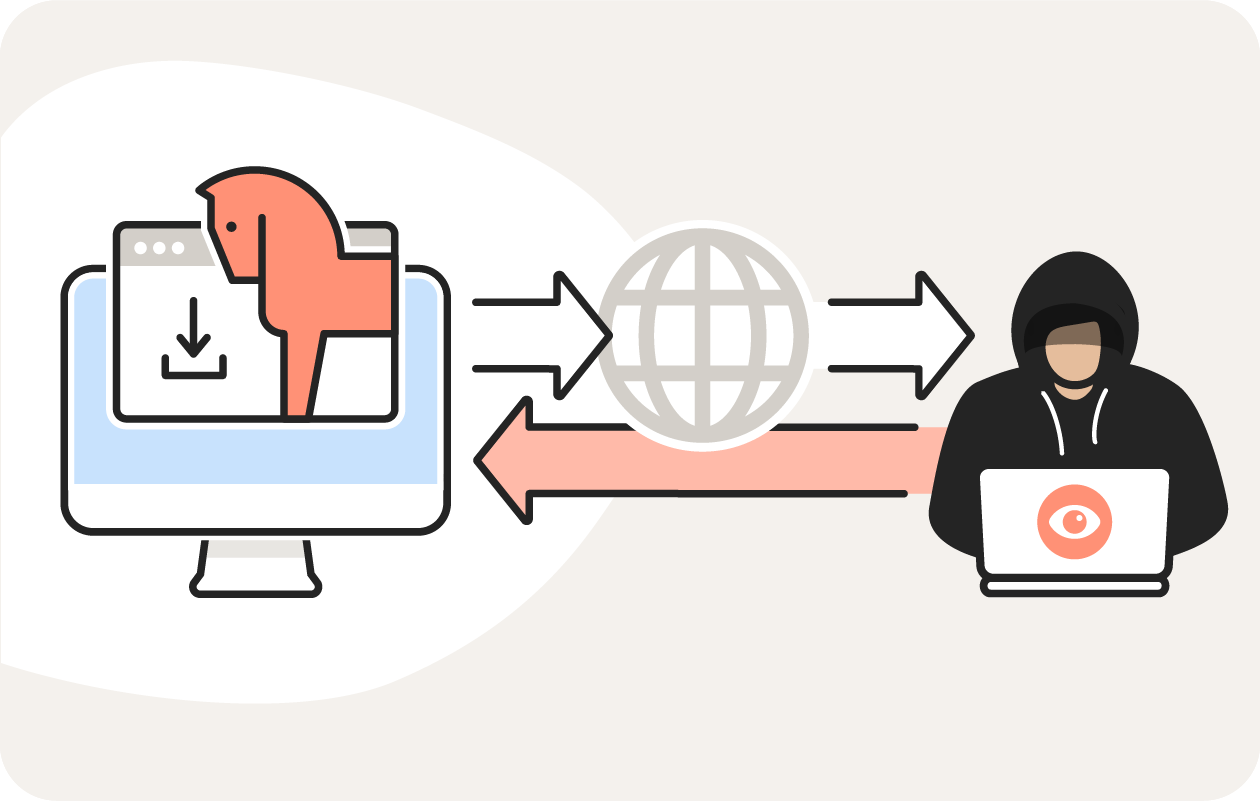

Once inside, the RAT cyberattack begins. The RAT connects to an open TCP port on your device, which enables it to form a network connection between your computer and the attacker’s machine. The RAT then connects to a command-and-control server, which is controlled by the attacker and gives them access to your device.
RATS are extremely dangerous because they don’t just deploy a specific malicious function on your device like other types of malware. They grant unrestricted access to human attackers who can use your device to perform any number of illegal operations.
Here are a few possible consequences of a RAT attack:
- DDoS attack. If a RAT hacker takes control of many devices, they can target a server with internet traffic from all of them. This is called a DDoS attack, and it can shut a server down and harm anyone connected.
- Invasion of privacy. With total access to your device and online activity, a hacker can easily learn your passwords, read your emails and messages, view your photos, access your accounts, and much more. They could use this information to blackmail you or steal your identity.
- Remote storage of illegal files. To protect themselves from the law and hide their activities, hackers may store their illegal RAT files, photos, and evidence on your computer without your knowledge. It could mean trouble for you if illegal material is discovered on your device.
- Data loss. When a RAT hack has been deployed, a hacker can enter your computer and take whatever they want. They may choose to steal and delete your files or lock you out of your device. This is just one reason why data backups are important.
- Cryptomining. Hackers can make a hefty sum by using your computer to mine cryptocurrency such as Bitcoin. Cryptomining is energy-intensive and can damage your hardware over time.
Another reason why RATs are so dangerous is that they spread quickly. Once an attacker has access to your device, it’s easy for them to deploy more RATs, spreading malware to your family, friends, and coworkers.
How to detect a remote access Trojan
Remote access Trojan malware is not easy to detect. If you want to know how to tell if you have a RAT on your computer, watch for the following virus warning signs that may indicate the presence of a RAT:
- Frequent website redirects. If your browser keeps redirecting your web searches to different pages, this could be a sign that someone else has control of your computer.
- Mysterious files. Hackers may try to store their files on your device to hide illegal activity. If you find strange files on your computer that you don’t recognize, don’t open them. Instead, check for a RAT by scanning for viruses.
- Your webcam is on for no reason. If your webcam is randomly on, it’s possible it was activated remotely, and someone may be watching. If this happens, cover your webcam until you know your connection is private.
- Poor computer performance. Poor or slow performance could indicate that a hacker is using your computer to carry out tasks in the background, such as mining cryptocurrency.
To help prevent a remote access Trojan from entering your device, use powerful cybersecurity software like Norton 360 Deluxe. You can protect up to five devices with one subscription, and it will help keep you safe from other types of malware and online threats, too.
Remote access Trojan examples
There are many remote access Trojans lurking on the web, just waiting for you to download them. Here’s a look at some of the most infamous RAT viruses.
- CrossRAT: CrossRAT is a highly versatile RAT that can access nearly all operating systems — including Windows, macOS, Linux, and others — allowing it to spread quickly and easily.
- Beast: Developed in 2002, Beast is one of the oldest RATs. It’s still going strong today, although it only affects Windows devices.
- Mirage: Mirage is an advanced RAT operated by a hacking group believed to be sponsored and directed by the Chinese government to target foreign governments and militaries.
- Saefko: A particularly stealthy RAT, Saefko monitors victims’ browsing history to steal cryptocurrency transaction data.
- Poison Ivy: Used to perpetrate numerous attacks on government organizations and businesses since 2005, it usually spreads through Word files or PDF attachments in spear phishing emails.
- Blackshades: A very dangerous RAT that’s able to self-propagate by sending links via victims’ social media accounts. It uses its RAT network of hostage computers to carry out DDoS attacks.
How to protect against remote access Trojans
The best way to protect yourself against Trojans is to practice good cyber hygiene habits. Here’s how to interact safely online and help shield yourself from RAT malware:
Enable two-factor authentication
Two-factor authentication (2FA) is a security protocol that requires you to input two forms of authentication to enter an account. For example, after entering a password, 2FA may ask you to enter a code you received via SMS to verify your identity.


Enabling 2FA can help keep a hacker out of your online accounts even if they find your password. So, it’s a smart idea to enable 2FA on critical accounts such as email, financial accounts, government accounts, and any other accounts that contain sensitive infot.
Avoid suspicious links and attachments
It might seem obvious to avoid suspicious links and attachments, but what if they’re sent by someone you trust? Whenever you receive a link or attachment in your inbox, consider whether it might be a form of phishing. This is especially true if you weren’t expecting to receive something from the sender.
Keep your operating system up to date
Software companies, such as Apple and Windows, are pretty good at patching security vulnerabilities as they are discovered. But to keep your device protected by the latest patches, you need to update your software regularly. Perform software updates whenever they’re released to ensure you have the best protection against RATs and other malware.
Go to your system settings to enable your device to check for software updates automatically.
Only install software from legitimate sites
App stores like those managed by Apple and Google help ensure the security of the apps they sell. But third-party app stores and websites usually don’t offer that protection. Sticking to legitimate websites and trusted app stores will reduce the risk of accidentally installing a RAT virus or another type of malware.
Use a VPN
A VPN is a privacy tool that encrypts your internet data and hides your IP address when you’re online. VPNs help block anyone trying to track you, including government agencies, advertisers, and the types of hackers who may target you with a computer RAT. VPNs offer many other benefits too, such as the ability to access content.
Not all VPNs offer the same level of protection against hackers and trackers. That’s why it’s important to choose a VPN like Norton Secure VPN that’s built specifically to keep you safer online, by automatically securing your network to help keep your web activity and the data you send and receive private. Download Norton Secure VPN on its own or get it as a built-in feature of Norton 360 DeluxePN
Use an intrusion detection system
An intrusion detection system (IDS) is a type of software that monitors network activity and alerts you if something unusual happens, such as an attempt to break through a firewall. Like a security camera for your network, an IDS knows how to detect RAT software, and it can alert you when suspicious activity is detected.
An IDS is essential for organizations that need to protect a network of devices, but it’s generally not recommended for personal use. To protect a personal device, like your computer or phone, get antivirus software.
Install antivirus software
Using antivirus software will help block remote access Trojans and other types of malware, such as ransomware. Antivirus software usually scans your devices for malware, RATs, or potential security threats and works in the background to shield your devices from attacks in real tim.
Stay safe from remote access Trojans
Understanding how RATs work and the tricks hackers use to deploy them on your devices is a good start, but the best way to protect your digital life from RATs and other malware is to use reliable cybersecurity like Norton 360 Deluxe.
Norton 360 Deluxe packs powerful threat detection with advanced tools and features such as a VPN, a password manager, and privacy monitoring.
FAQs about remote access Trojans
Are remote access Trojans illegal?
Yes, it is illegal to use a remote access Trojan. A RAT takes control of a device without the consent of the device owner. Gaining unauthorized access to a device that doesn’t belong to you or that violates someone’s privacy is illegal.
Of course, remote access itself is not illegal and is used by businesses to protect remote devices connected to their networks. And if you have a problem with your computer, you can give an IT professional permission to remotely access your machine to try to fix the problem.
What is the difference between RAT software and a RAT computer virus?
RAT software and a RAT computer virus are the same. A RAT in cybersecurity stands for a remote access Trojan. It’s a type of malware that gives a hacker control over an infected device. Because a RAT is technically a type of software, it’s sometimes referred to as RAT software. And because the malicious software infects your computer, it’s also known as a RAT computer virus.
Can a remote access Trojan access your webcam?
Yes, a remote access Trojan can access your webcam. If you notice that your webcam is on for no reason, it may be a sign that your computer has been infected by a RAT. Cover your webcam lens and check your computer for malware as soon as possible.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.







Want more?
Follow us for all the latest news, tips, and updates.