What is bluejacking? Definition + protection tips
What is bluejacking?
Bluejacking is a Bluetooth attack in which a hacker spams your device with unsolicited phishing messages.

When it comes to wirelessly pairing two devices, it's tough to beat the convenience of Bluetooth.
From wireless headphones to fitness trackers, you can connect your laptop, phone, or other mobile devices to wireless accessories with ease. While this is helpful for you, it also means it can be easy for hackers to exploit your Bluetooth device and carry out a bluejacking attack.
Bluejacking is a Bluetooth security threat in which a hacker spams your device with unsolicited phishing messages.
But what exactly is bluejacking, and how does it work? Follow this guide to learn more about the dangers of bluejacking, how to spot it, and protection tips to help you stay safe.
How bluejacking works
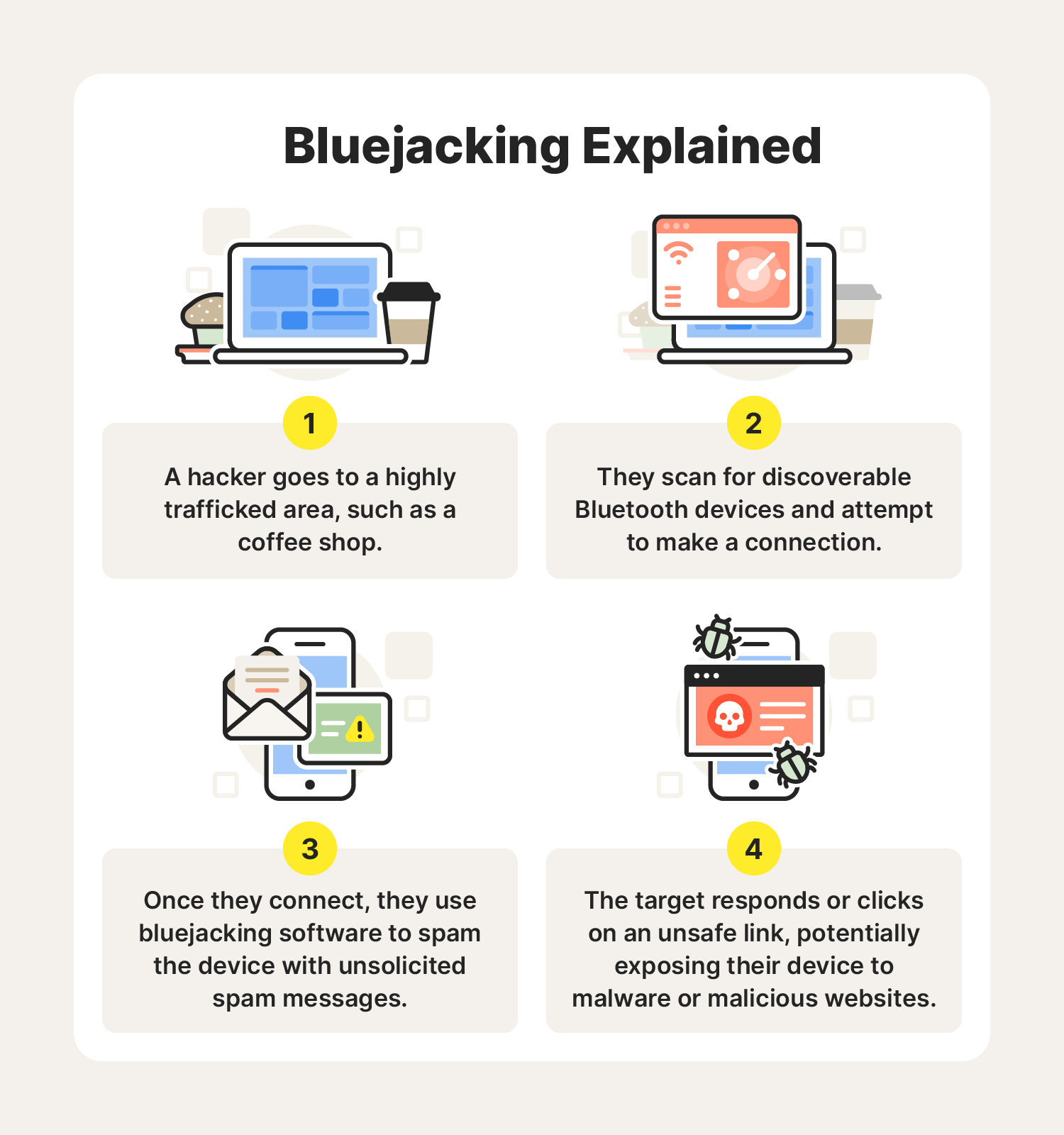
Now that you understand what bluejacking is, you may be wondering how it works. Before a bluejacker can carry out any attacks, they must first go where they are within range of other Bluetooth-enabled devices. Because of this, bluejackers may target highly trafficked areas like airports, malls, and coffee shops.
Once they are within range, they'll scan the area for Bluetooth devices. The bluejacker will then try to connect to your device using bluejacking software and send you unsolicited messages. These messages can range from harmless prank texts to dangerous phishing messages used to steal your information or infect your device with malware.
In some cases, more experienced hackers may also try to use a brute force attack to bypass password protection that could keep them from easily pairing with your device.
After learning about how bluejacking works, you might wonder how this differs from bluesnarfing, which is another Bluetooth-based cyberattack. Read along to learn more about how the two cyberattacks differ from one another.
Bluesnarfing vs. bluejacking: What’s the difference?
The difference between bluejacking and bluesnarfing is that bluejacking is an attack that involves spamming your device with unsolicited phishing messages over Bluetooth, while bluesnarfing is an attack that involves stealing your information using a Bluetooth connection.
Dangers of bluejacking
Even though bluejacking doesn’t involve the direct theft of your information like bluesnarfing does, it can still invade your privacy and potentially harm your device. To better understand the dangers of bluejacking attacks, let's take a look at the harmful activities hackers use bluejacking technology for:
- Malware: In some cases, a bluejacking spam message can include a link that may infect your device with different types of malware, including ransomware and spyware.
- Phishing scams: Some bluejackers may use bluejacking as a line of communication to bombard your device with different types of phishing attacks, such as whaling.
- Malicious websites: Another danger of Bluetooth jacking is that the hacker can send you website links to trick you into visiting a malicious website. From there, the hacker may attempt to steal your private information.
- Identity theft: Whether by catfishing or sending you to an unsafe site, bluejacking can be used to get you to hand over private information that the Bluetooth jacker can use to steal your identity.
- Harassment: While this may not be as damaging to your privacy as the other dangers, some bluejackers may use bluejacking to harass you. On top of being annoying, these bluejacking messages can also contain hateful and abusive content.
To help avoid these dangerous cyberthreats, continue reading to learn more about the warning signs that can help you spot a bluejacking attack.
How to spot a bluejacking attack
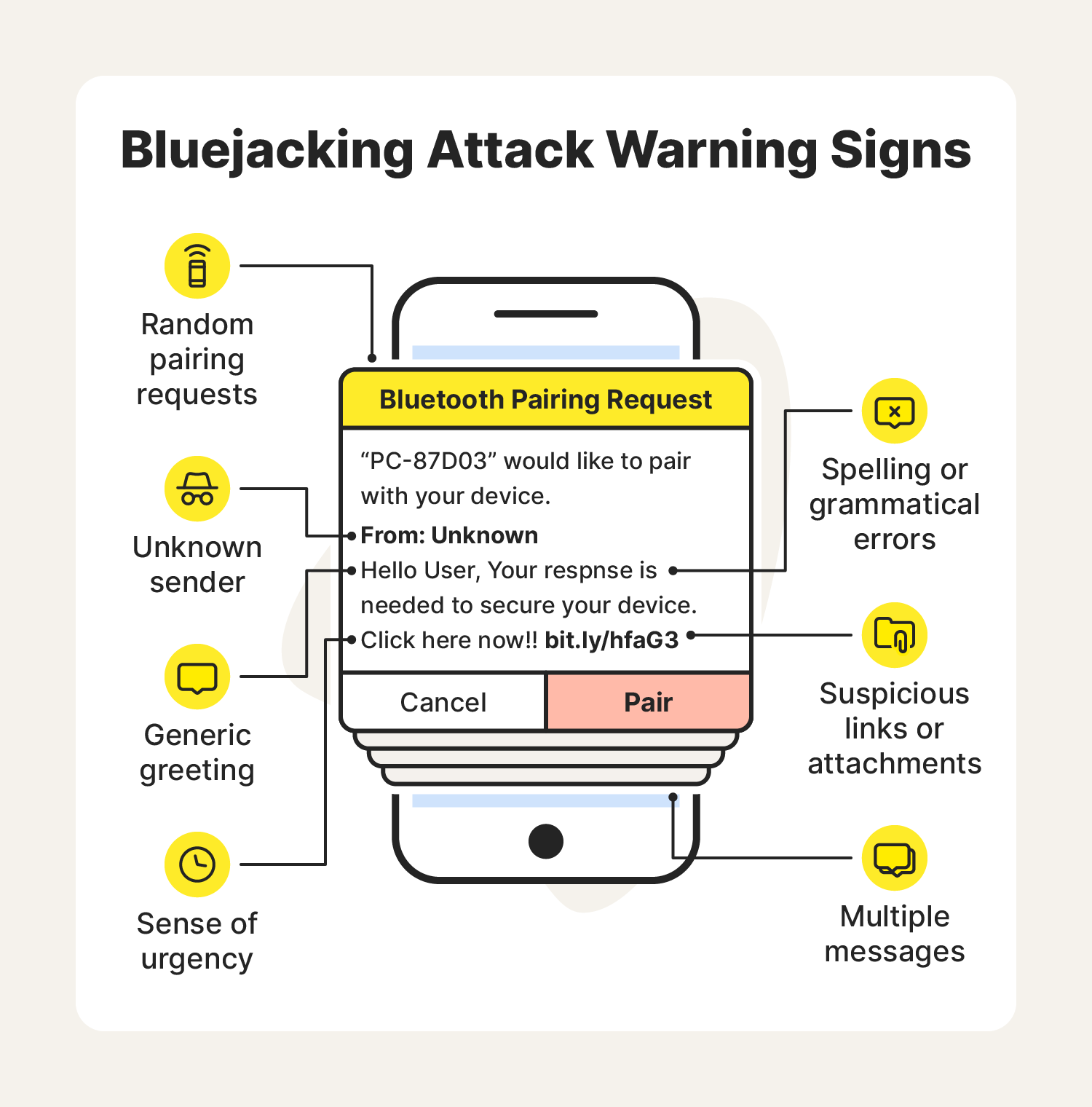
Bluejacking attacks often have similar traits to phishing messages that can help you identify them before they cause you any issues. Whenever you’re using a Bluetooth device, keep an eye out for these bluejacking warning signs:
- Pairing requests from unknown devices: If you start receiving random pairing requests from unknown devices while you’re in a public area, it could be a bluejacker attempting to carry out an attack.
- Unknown sender: You should always be skeptical whenever you start receiving random messages and are unsure who they’re coming from, as it may be a bluejacking attack.
- Generic greeting: A lot of times, bluejackers will have no idea who they are speaking to unless you've listed your name in your device name. Because of this, bluejacking messages may include generic greetings like “Hello” or “Hello user.”
- Spelling or grammatical errors: In many cases, bluejacking messages contain spelling or grammatical errors. Always be on the lookout for poorly written messages.
- Sense of urgency: Some bluejackers will use social engineering techniques to make you feel like you need to act immediately or something bad will happen. This is to get you to quickly visit a website without thinking or to give them personal information they can use to their advantage.
- Suspicious links or attachments: Like phishing emails, bluejacking messages may include suspicious links or attachments that can expose you to malware or unsafe websites.
- Multiple messages at once: Because bluejacking attacks only work when the hacker is near your device, they usually involve a bombardment of messages in hopes you panic and give the attacker what they want before you lose Bluetooth connection with them.
By keeping these warning signs in mind, you can quickly spot a bluejacking attack as soon as it comes across your device.
How to protect against bluejacking attacks
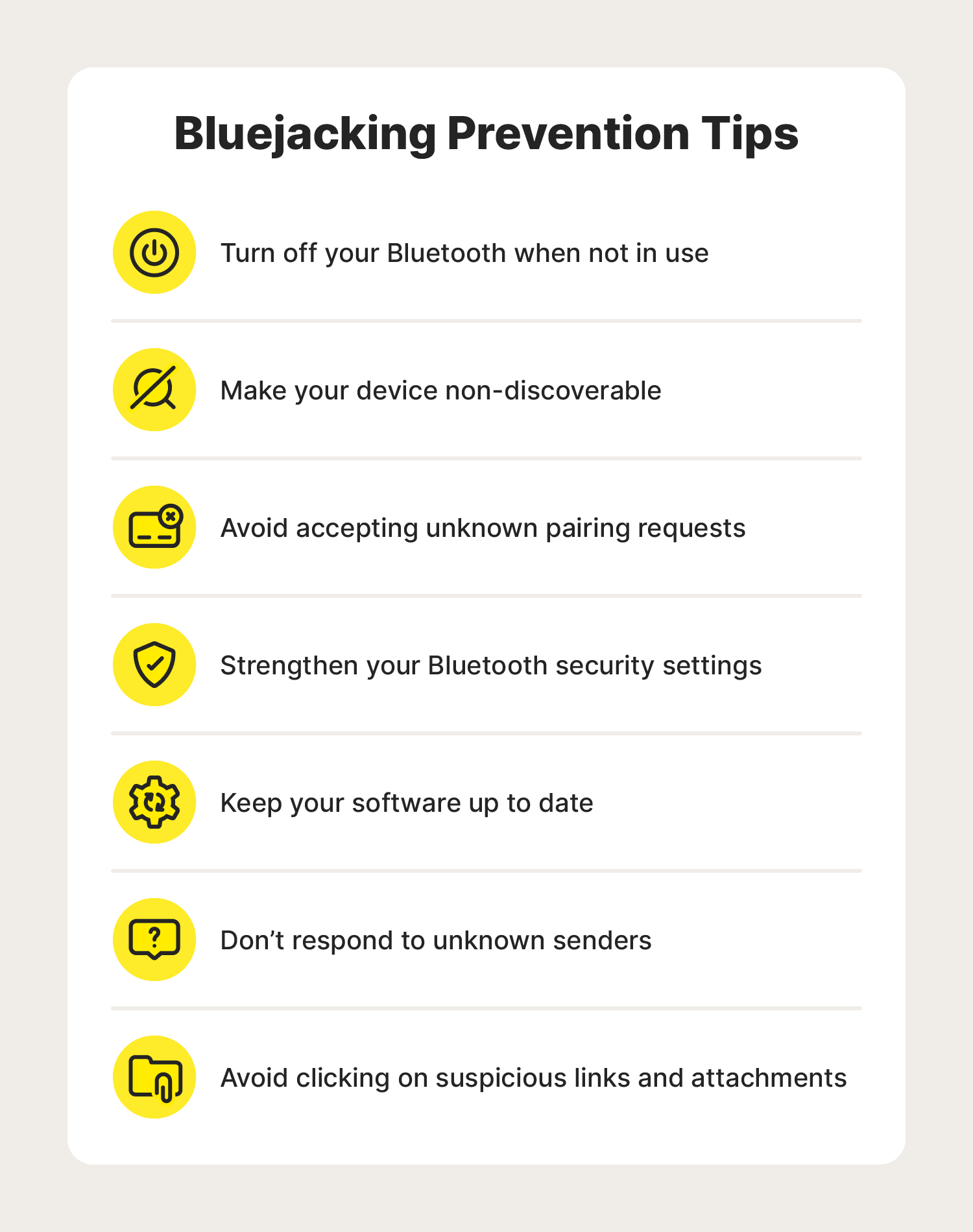
So how can you help protect against bluejacking attacks altogether? While hackers may continue to advance their bluejacking techniques, following these bluejacking protection tips can help you reduce your chances of being affected by an attack.
Turn off your Bluetooth when not in use
You can think of leaving your Bluetooth on like leaving your keys in your car while you’re away. While there is no guarantee you'll be affected by bluejacking, you’re leaving the door open for any clever bluejackers to try and connect to your device. Because of this, always turn your Bluetooth off whenever it's not in use.
Make your device non-discoverable
Similar to turning off your Bluetooth entirely, setting your device to non-discoverable can also make it more difficult for a bluejacker or any other hacker to easily target your device in a bluejacking attack.
Avoid accepting unknown pairing requests
As a general rule of thumb, you should never accept pairing requests from unknown devices. After all, it could be someone looking to bluejack a cell phone or attempt another Bluetooth cyberattack, such as bluesnarfing or bluebugging.
Strengthen your Bluetooth security settings
Depending on your device, you may be able to enable settings that require you to manually accept all pairing requests. That way, you can use your Bluetooth device with confidence, knowing that no unknown connections are slipping through the cracks.
Keep your software up to date
As with any cyberattack, bluejackers may also try to target devices with known security flaws that might make it easier to connect without being noticed. Always update your software to ensure you have the latest security patches to protect you from bluejacking and other cyberthreats.
Don’t respond to unknown senders
Whenever you receive a message from an unknown sender, it's always a safe move to ignore it. That way, you reduce the risk of engaging with someone who may have bad intentions, like using bluejacking as a way to steal your private information or scam you.
Avoid clicking on suspicious links and attachments
Whether it's a bluejacking message, email, or random social media post, be wary of opening any mysterious links or attachments. This is because bluejackers can use links and attachments to disguise malicious files, such as ransomware or spyware. In other instances, it could take you to a spoofed website.
By using your mobile device cautiously and following these protection tips, you can help reduce your chances of being affected by bluejacking. Want to protect yourself even further? Try using a trusted mobile antivirus software for Android or mobile antivirus software for iOS to help keep your mobile devices secured for you.
FAQs about bluejacking
Still curious about bluejacking? Read through the answers to some common bluejacking questions below.
What is the purpose of bluejacking?
The purpose of bluejacking a phone is for hackers to send you unsolicited messages over Bluetooth to either annoy you or distribute malware or other phishing scams.
What is an example of bluejacking?
An example of bluejacking is when you receive a random message from an unknown sender while using a Bluetooth-enabled device, likely while in a public place. The message may urge you to follow a link for important information.
After clicking the link, you land at an unsafe website requesting your personal information to see whatever the sender claimed to send you. Once you input the requested info, the scammer steals it and uses it for other purposes, such as identity theft.
Is it possible to bluejack a phone?
Yes, it is possible for a hacker to bluejack a phone if they are able to make a successful connection via Bluetooth.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.




Want more?
Follow us for all the latest news, tips, and updates.