Bluesnarfing: An overview + prevention tips
What is bluesnarfing?
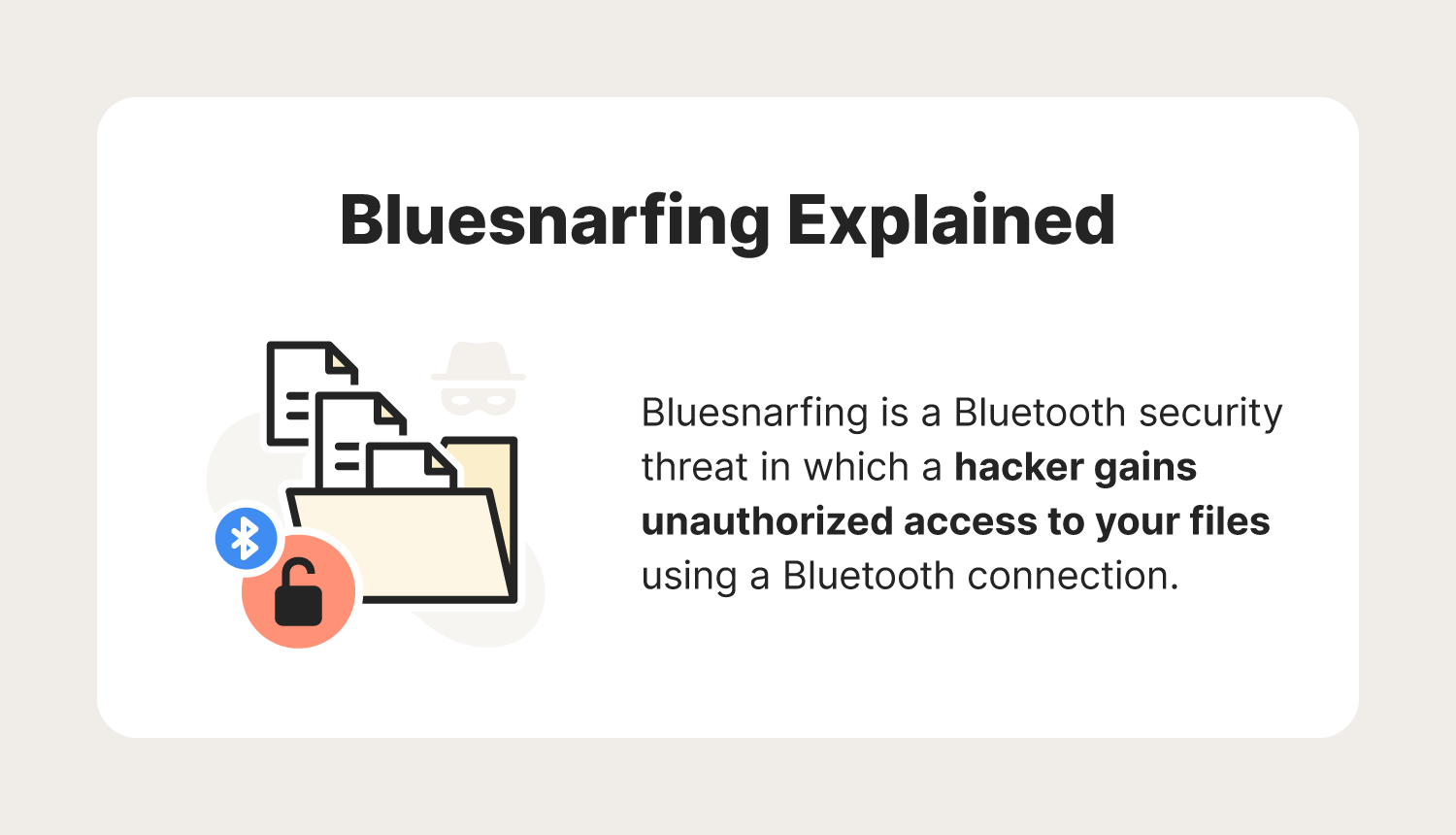
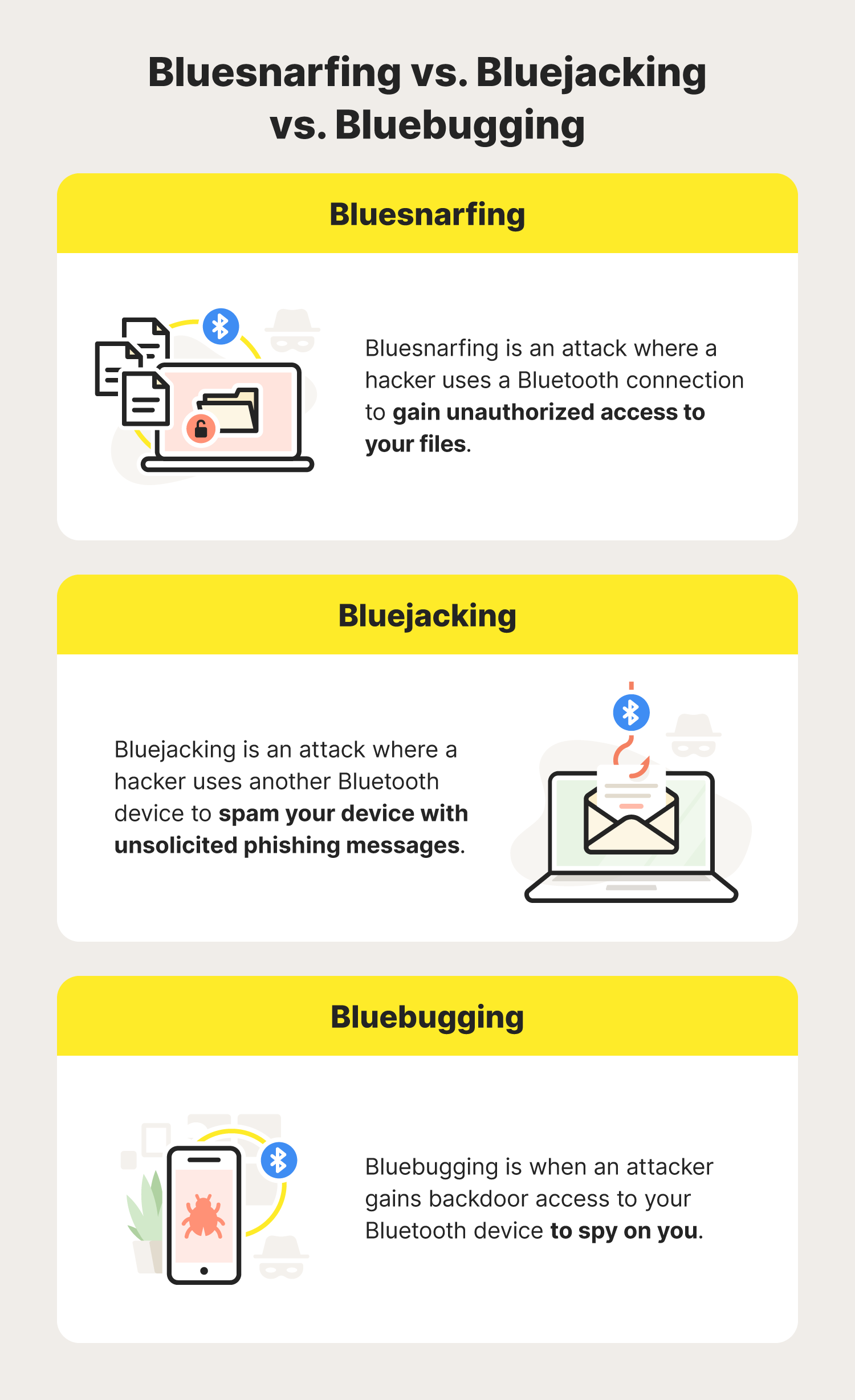
Bluesnarfing is a Bluetooth® security threat in which a hacker gains unauthorized access to your files using a Bluetooth connection

Nowadays, nearly all devices use Bluetooth. Whether it's your laptop, smartphone, or desktop computer, Bluetooth technology allows you to easily pair headphones or share files — all without the need for wires.
Think of all the important information you store on these Bluetooth devices: family photos, financial documents, login information, and more.
Now imagine if hackers were able to exploit this technology to steal these files right off your device without you knowing.
This is an example of a successful bluesnarfing attack.
Follow this guide to learn more about bluesnarfing, how it works, and how you can prevent an attack.
How does bluesnarfing work?
Hackers can initiate bluesnarfing attacks by exploiting vulnerabilities within the object exchange (OBEX) protocol. In other words, bluesnarfing targets security flaws within the technology used to share files between Bluetooth devices. Bluetooth testing tools like Bluediving identify these vulnerabilities and pinpoint OBEX flaws in Bluetooth-compatible devices.
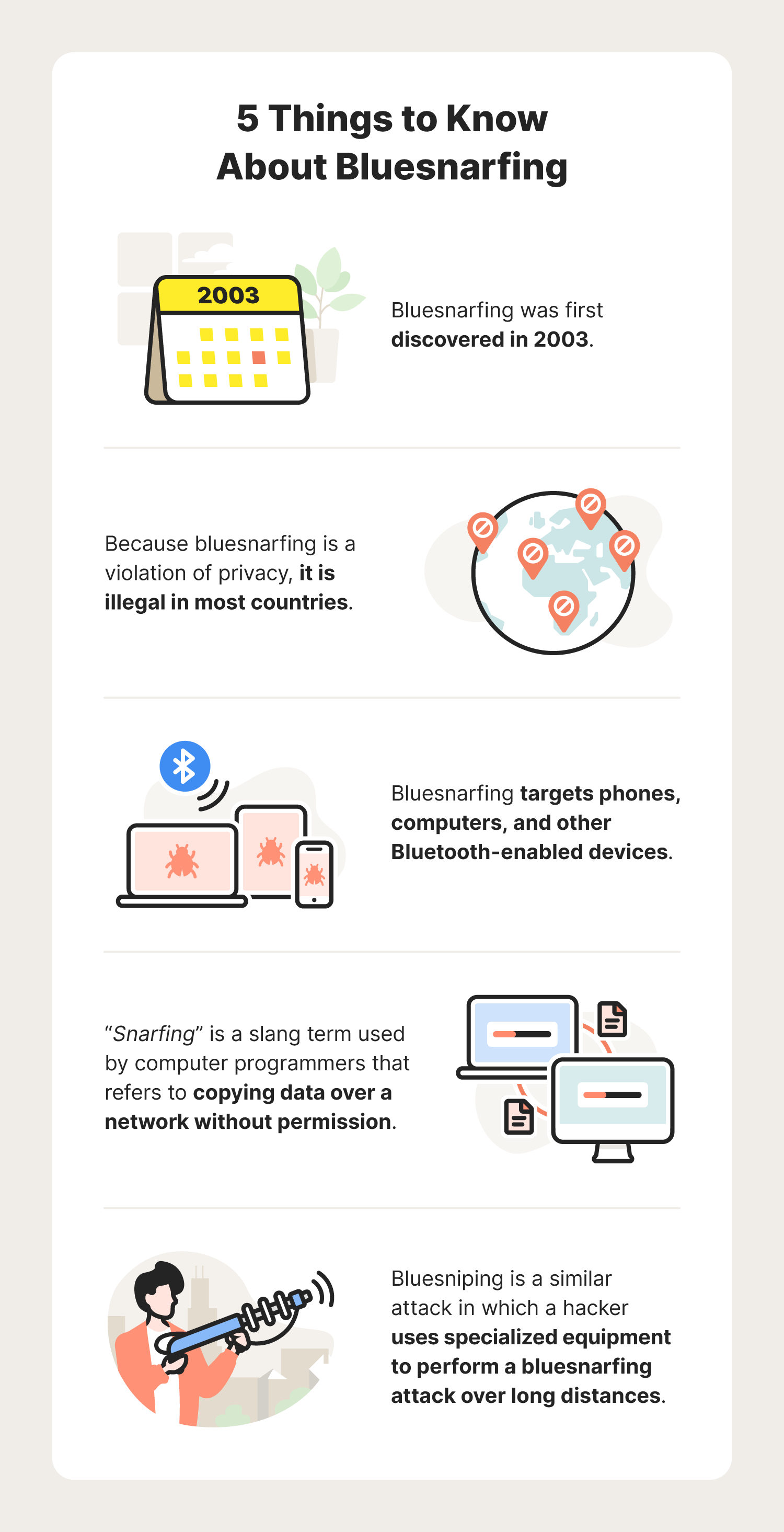
Cybercriminals may then program their own bluesnarfing tools, hire a skilled bluesnarfer to do it for them, or even download bluesnarf software off of the dark web. Once a hacker can exploit flaws in your Bluetooth device, they’ll pair their device to yours and attempt to steal your information.
If successful, the hacker may end up with your personal information including photos, emails, text messages, contacts, login credentials, and more. In many instances, a cybercriminal can steal your information without you ever even noticing.
The hacker will usually need to be within 30 feet of your device to carry out a bluesnarf attack. If the attacker is using specialized equipment, they may reach your device from further away. This is often referred to as a “bluesniping” attack.
Bluesnarfing vs. bluejacking vs. bluebugging: What’s the difference
Bluesnarfing is sometimes confused with other Bluetooth security threats, including bluejacking and bluebugging.
- Bluejacking is another attack in which a hacker uses another Bluetooth device to spam your device with unsolicited phishing messages.
- Bluebugging is when an attacker gains backdoor access to your Bluetooth device to spy on you.
So, the main difference between bluesnarfing and these attacks is that bluesnarfing involves the theft of your personal files.
How to prevent bluesnarfing: 10 cybersecurity tips
While detecting a bluesnarfing attack is tricky, there are some simple precautions you can take to help reduce the risk of bluesnarfing attacks while also improving your cybersecurity in the process. To help keep your device Cyber Safe and prevent a bluesnarfing attack from happening to you, follow these cybersecurity tips.
1. Turn off your Bluetooth when not in use
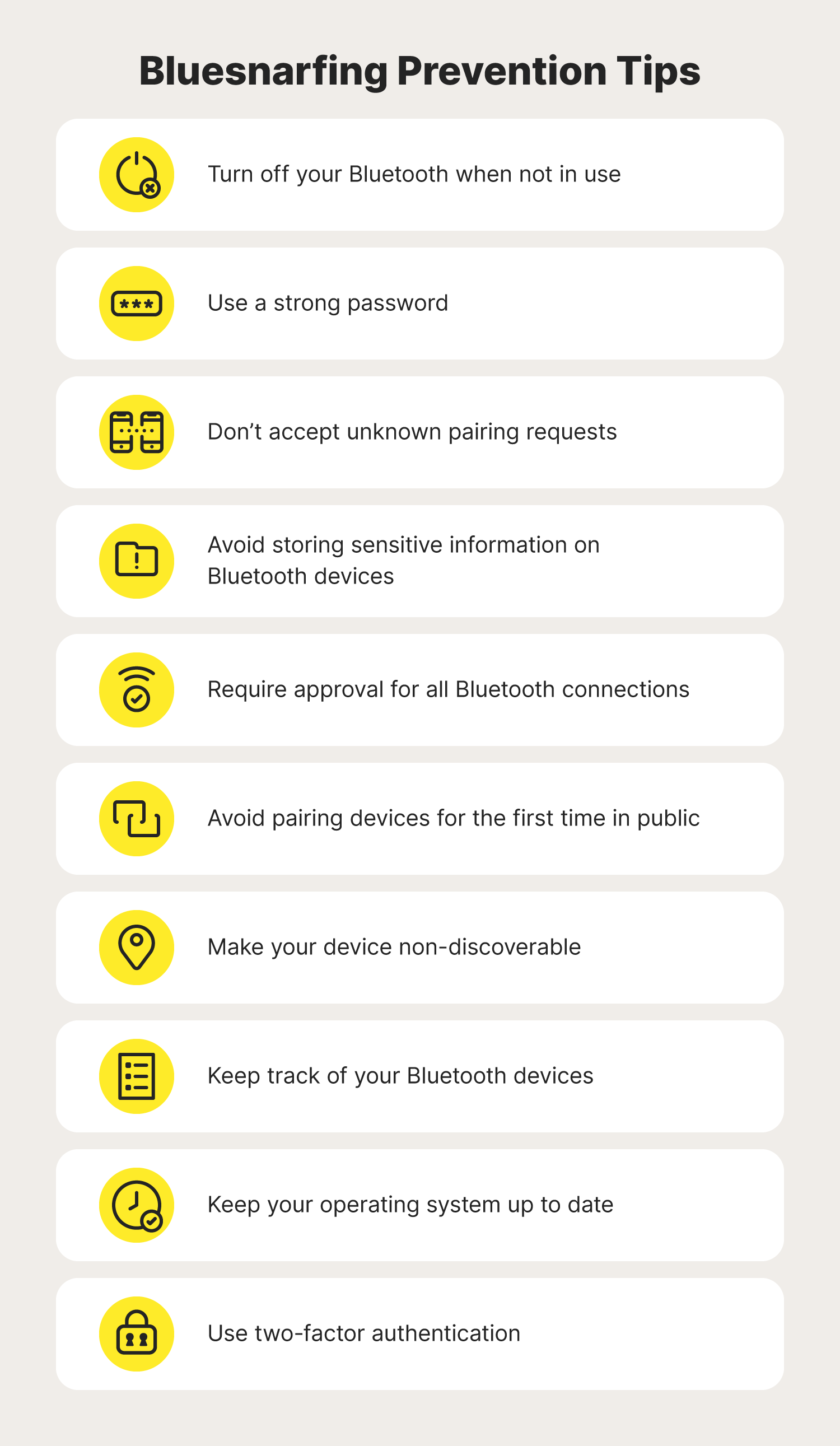
Above all, turning off your Bluetooth is the most effective way to eliminate the risk of a bluesnarfing attack. Just like how you'd never leave your door open when leaving the house, you should never keep your Bluetooth on when it isn't in use. If you do, you’re technically leaving the door open for cybercriminals to try and connect to your device. To be safe, only turn your Bluetooth on when you’re using it.
2. Use a strong password
No matter what aspect of your cybersecurity you’re dealing with, using a secure password is a must. That way, if a hacker does make it onto your device, they may be stopped by a password before they can steal your information. Not only can this prevent a successful Bluetooth snarfing attack, but it can help minimize the damage a hacker can cause by connecting to your device.
3. Don’t accept unknown pairing requests
Another way to prevent bluesnarfing attacks is to decline any pairing request you didn’t initiate. This can help you avoid accidentally letting in a Bluetooth hacker. Even if the device name seems familiar, always double-check before accepting. It’s possible that a hacker is attempting to impersonate a device they think you’ll connect with without question.
4. Avoid storing sensitive information on Bluetooth devices
While this technically won’t prevent a bluesnarfing attack on its own, keeping sensitive information off of your Bluetooth device is a great way to reduce the chances of it getting into the wrong hands, ultimately leading to other cybersecurity threats like identity theft.
5. Require approval for all Bluetooth connections
If possible, configure your Bluetooth device so it doesn’t automatically connect with new Bluetooth devices without your permission. That way, you can screen each Bluetooth pairing request and only connect with devices that you know are safe.
6. Avoid pairing devices for the first time in public
When pairing two devices for the first time, be sure to do it in a secure location like your house. If you pair the two devices in a populated area such as a coffee shop, it's possible that a Bluetooth hacker can pop in and hijack the pairing process and connect to your device.
7. Make your device non-discoverable
Similar to turning off your Bluetooth altogether, making sure your device is set to non-discoverable is another way to help prevent a hacker from seeing your device. While it may still be possible for a hacker to find your device if your Bluetooth is still on, turning off your discoverability can greatly reduce the chances that a hacker will discover your device.
8. Keep track of your Bluetooth devices
Knowing the location of your Bluetooth devices is a helpful way to make sure they are never in harm's way. For example, let's say you leave a Bluetooth device in your car while it’s parked in a populated area. If your device has its Bluetooth discoverability turned on, a nearby hacker may try to attack your device while you're away.
9. Keep your operating system up to date
In many cases, a Bluetooth device with an outdated operating system is a dream for a Bluetooth hacker because it will lack the most up-to-date bug fixes and security patches. This can make it easier for a hacker to exploit a security vulnerability and access your information. To prevent this, always update your device’s operating system.
10. Use two-factor authentication
While two-factor authentication (2FA) won’t stop a bluesnarfing attack from happening, it can help deter your attacker from easily accessing any of your online accounts. That way, even if the hacker finds one of your passwords, they can’t successfully log in to any account where you have 2FA enabled.
By keeping these good cyber hygiene habits in mind, you can use your Bluetooth device knowing you've taken the best precautions to avoid a bluesnarfing attack. Not only that, but they can help protect you from other emerging mobile threats.
FAQs about bluesnarfing
Continue reading to learn the answers to these common questions about bluesnarfing.
Is bluesnarfing easy?
Bluesnarfing is considered one of the easier Bluetooth attacks to implement. This is because hackers can easily find bluesnarf tools and instructions online, especially on the dark web. Fortunately, developments in mobile device software made newer devices far less vulnerable to these types of attacks than older devices.
What can a hacker access when bluesnarfing?
If successful, bluesnarfing hackers can access important information on your device, including:
- Photos
- Emails
- Text messages
- Contacts
- Login credentials
In some cases, the hacker may be able to do this without your knowledge.
Does bluesnarfing still work?
Bluesnarfing attacks are now less common, mainly due to newer Bluetooth devices having built-in authentication and improved security features. Keep in mind that older devices may still be more vulnerable to these types of attacks.
How do you know if you've been targeted by a bluesnarfing attack?
Unfortunately, bluesnarfing attacks can take place without you ever even knowing. Because of this, it’s important to always turn your Bluetooth off whenever it is not in use, as that is the best way to prevent a bluesnarfing attack.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.

Want more?
Follow us for all the latest news, tips, and updates.