What is encryption? How it works + types of encryption
What is encryption?
Encryption converts sensitive information or data into a secret code to prevent unauthorized access.

If you’ve ever made an online purchase, logged in to your social media accounts, or filled out an online contact form, your information already exists as encrypted data. Encryption is an essential online privacy tool used to safeguard sensitive, confidential, or personal information across the internet.
Encryption scrambles plain text into a type of secret code that hackers, cybercriminals, and other online snoops can't read—even if they intercept it before it reaches its intended recipients. When the message gets to its recipients, they have their own key to unscramble the information back into plain, readable text.
With one in three consumers falling victim to cybercrimes in 2021 alone, simple security measures like encryption can help protect the data you send, receive, and store on your electronic devices.
What is encryption?
Encryption is a cybersecurity measure that scrambles plain text so it can only be read by the user who has the secret code, or decryption key. It provides added security for sensitive information.
Huge amounts of data are managed online and stored in the cloud or on servers with an ongoing connection to the web. It’s nearly impossible to do anything online—from purchasing new office chairs to logging in to your HR portal—without your personal data ending up in an organization’s networked computer system. That’s why it’s crucial to know how to help keep that personal information private.
Encryption plays an essential role in this task.
When to use encryption
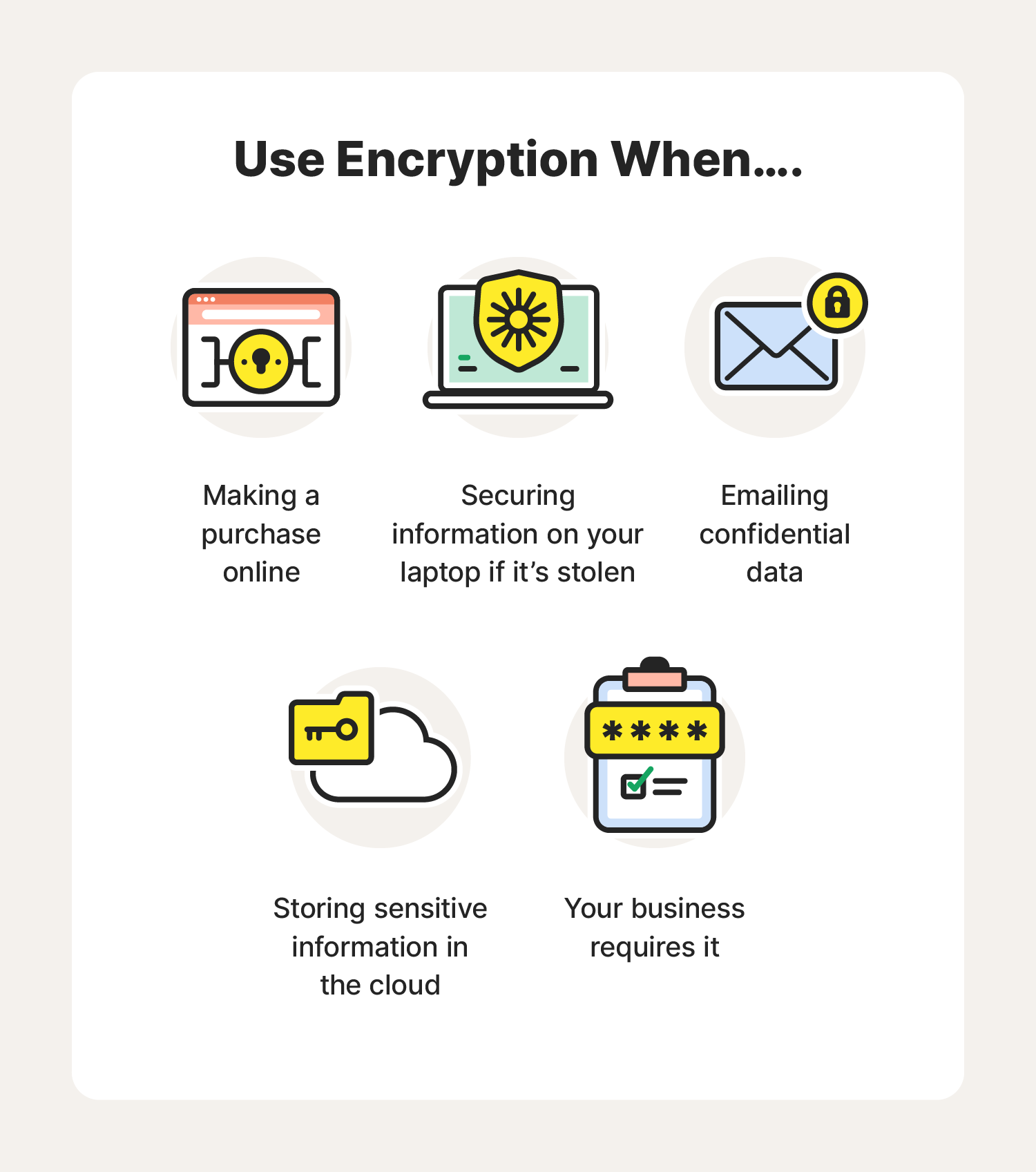
It’s important to encrypt messages, files, and data exchanged online whenever they contain personal, sensitive, or classified information like:
- Sending an email to your doctor regarding an illness
- Entering your financial information to log in to your online bank account
- Sharing a confidential report with your employer
Encryption ensures only the intended recipient can access the information you shared.
How does encryption work?
Encryption takes plain text, like a text message or email, and scrambles it into an unreadable format called ciphertext. This helps protect the confidentiality of digital data either stored on computer systems or transmitted through a network like the internet.
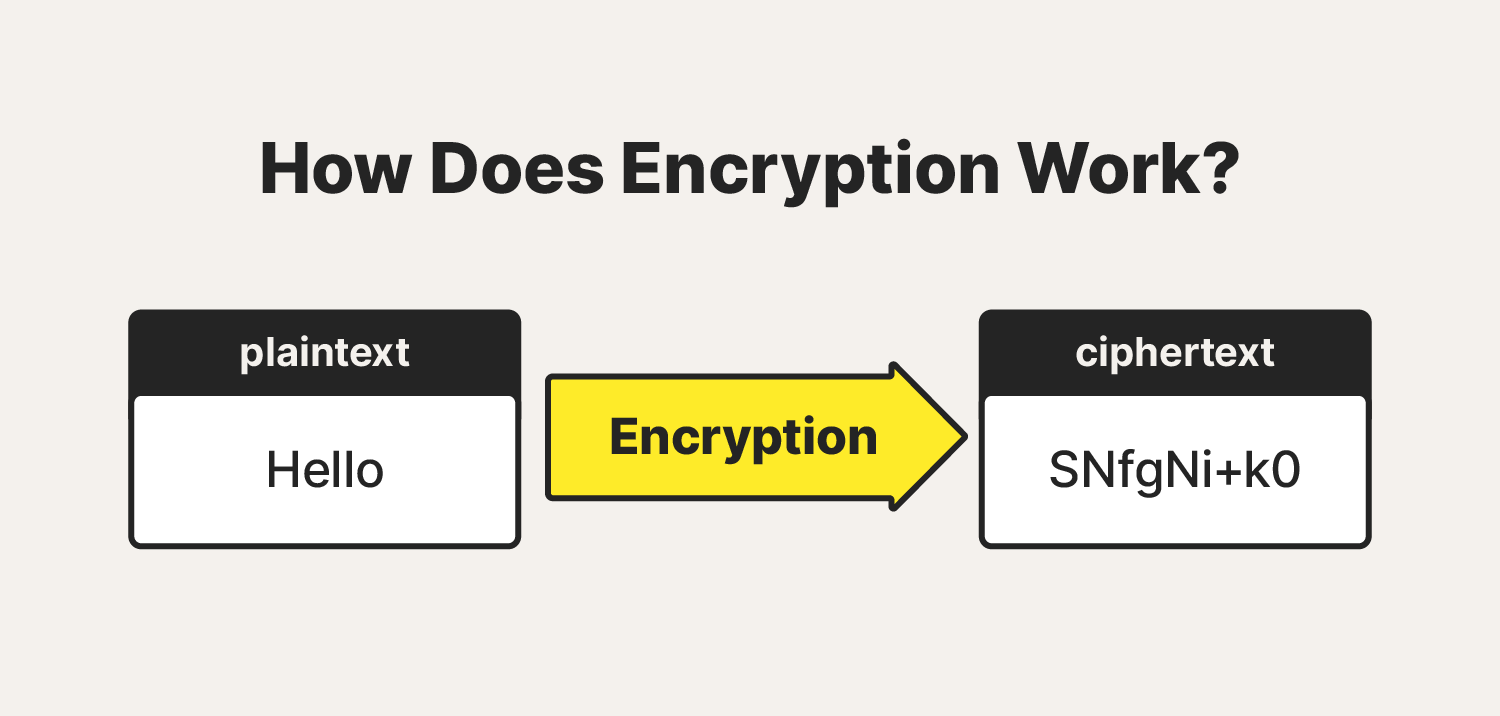
When the intended recipient accesses the message, the information is translated back to its original form. This is called decryption.
To unlock the message, both the sender and the recipient have to use a “secret” encryption key—a collection of algorithms that scramble and unscramble data back to a readable format.
Types of encryption
An encryption key is a series of numbers used to encrypt and decrypt data. Encryption keys are created with algorithms, and each key is random and unique.
There are two main types of encryption systems: symmetric encryption and asymmetric encryption. Here’s how they differ.
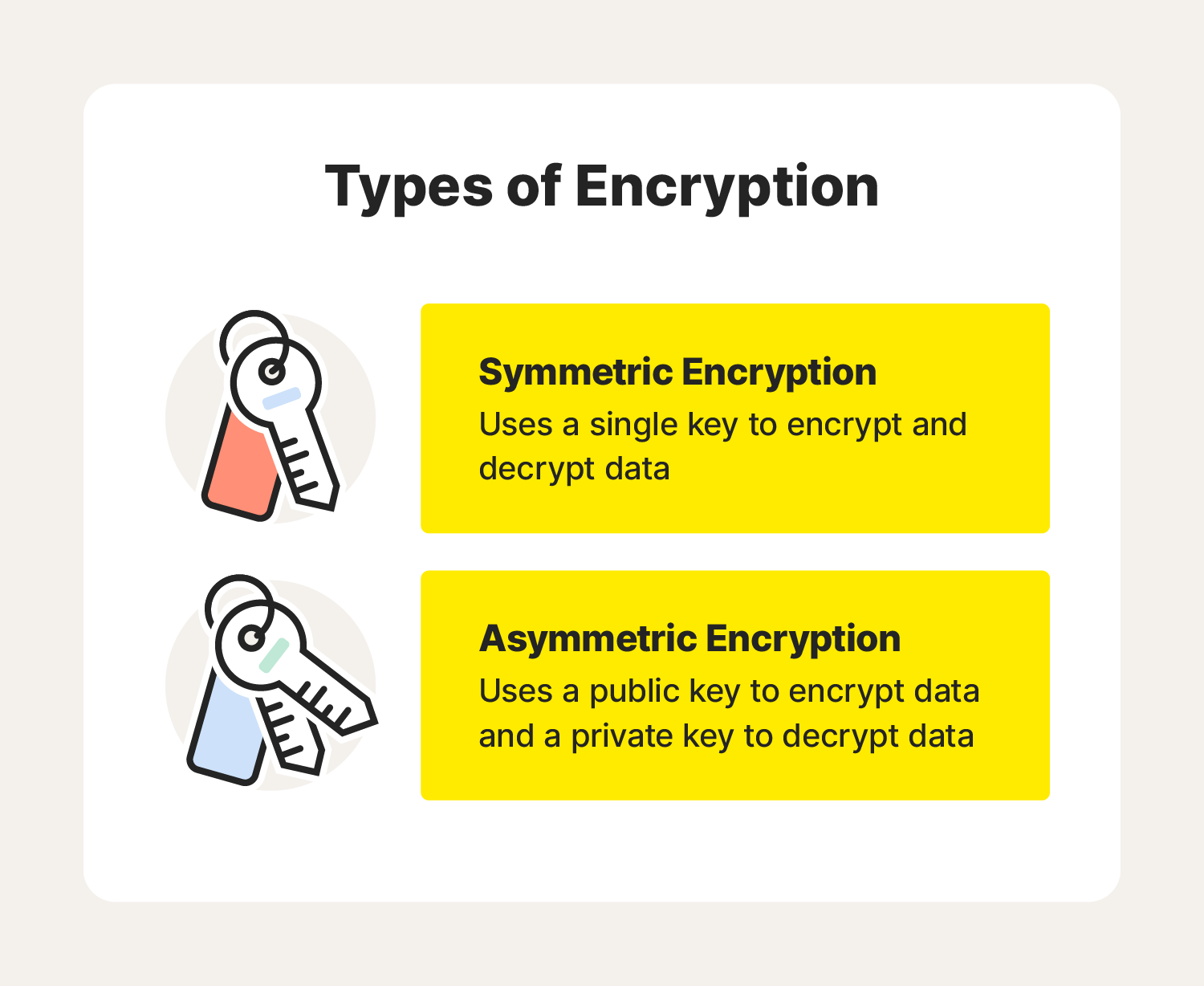
Symmetric encryption
Symmetric encryption uses a single secret password or key to encrypt and decrypt data. The key could be a code or a random string of letters or numbers generated by a random number generator (RNG), which is typically required for banking-grade encryption. Symmetric algorithms are the simplest and most used form of encryption.
Symmetric encryption algorithms are available in two forms:
- Block algorithms: Encrypt a group of plain text symbols as one block.
- Stream algorithms: Convert one symbol of plain text directly into ciphertext.
Although symmetric encryption has its weak spots, it makes up for them in speed and efficiency. Since only one key is shared between parties—and that key is typically much shorter than with asymmetric encryption—symmetric cryptography is faster to run.
Asymmetric encryption
Asymmetric encryption—also known as public key cryptography—uses two keys for encryption and decryption. A public key, which is shared among users, can either encrypt or decrypt the data. A private key can also encrypt or decrypt data, but it's not shared among users. The key you choose to encrypt or decrypt depends on the security measure you’re trying to employ:
- Encrypting with the public key: ensures only the intended recipient can use the corresponding private key to decrypt the message, even if the information was breached during transit
- Encrypting with the private key: allows the recipient of the information to verify the sender’s identity, since they won’t be able to decrypt data that’s been tampered with by an unauthorized user
Because asymmetric encryption uses two longer keys, it’s much slower and less efficient to run compared to symmetric cryptography. It can even bog down networks and create issues with memory capacity and battery life.
However, asymmetric encryption is considered more advanced in terms of security than symmetric cryptography. Both are still in use today—sometimes simultaneously to compensate for the other’s weaknesses.
What is an encryption algorithm?
An encryption algorithm is a set of rules, usually governing a computer or other tech device such as a smartphone, that turns readable data into scrambled ciphertext.
The data scrambled by these algorithms look like randomized code, but the algorithms configure this scrambled data in a purposeful way so that it can easily be turned back into a readable format by a decryption key.
6 types of encryption algorithms
There are several types of encryption, some stronger than others. Here are the most common examples of encryption algorithms.
Data Encryption Standard (DES)
Data Encryption Standard is an outdated symmetric encryption standard created in 1977 to protect government agencies. The system’s key length was a mere 56 bits—not nearly enough to keep cybercriminals from cracking the code. In 1999, it took engineers just 22 hours to hack a DES system. With modern tech, a 56-bit DES key can crack in as little as six minutes.
Because of advances in technology and decreases in the cost of hardware, DES is essentially obsolete for protecting sensitive data.
Triple DES (3DES)
Triple DES is a symmetric key block cipher that runs DES encryption three times. It encrypts, decrypts, and re-encrypts data—hence the name. It strengthens the original DES standard, which is now viewed by security experts as too weak for sensitive data.
However, even 3DES does not meet today’s security standards. With more effective algorithms available, like AES, the National Institute of Standards and Technology plans to deprecate DES and 3DES for all applications by the end of 2023.
Advanced Encryption Standard (AES)
Known for its impressive combination of speed and security, AES is the industry standard for encryption. AES uses both symmetric encryption and a substitution permutation network (SPN) algorithm to apply multiple rounds of encryption. These encryption rounds aid in security, since there are simply too many rounds for a cybercriminal to break through. Cracking a 128-bit AES key can take up to 36 quadrillion years.
The Advanced Encryption Standard replaced DES in 2002 as the U.S. government standard.
Rivest-Shamir-Adleman (RSA)
RSA takes its name from the surname initials of the three computer scientists who created it. This asymmetric system gives users the option to encrypt with either a public or private key, making it ideal for sending private data across the internet. When the public key is used for encryption, only the intended recipient can use the private key to decrypt it, even if the information was breached during transit.
On the other hand, encrypting with the private key allows the recipient of the information to verify the sender’s identity. If the data was stolen and modified in transit, the recipient wouldn’t be able to decrypt the new message with the public key, so they’d know it’d been tampered with.
Twofish
Twofish is considered one of the fastest symmetric encryption algorithms and is free for anyone to use. The system relies on a 128-bit key, making it almost impenetrable to brute force attacks—it could take decades for a hacker to decrypt one single message. It’s ideal for both hardware and software.
Elliptic curve cryptography (ECC)
Considered the next generation of cryptography, ECC is an asymmetric encryption algorithm that uses the mathematics behind elliptic curves. This method is almost impossible to crack since there is no known solution to the mathematical problem the algorithm is based on. This provides a significantly more secure connection than first-generation systems like RSA.
How does encryption keep internet browsing secure?
Most legitimate websites use encryption protection called Transport Layer Security (TSL)—an updated, more secure version of Secure Sockets Layer (SSL). This form of encryption protects data sent between systems, like credit card information sent through an ecommerce website or a payroll app receiving personal employee information from another server. This keeps attackers from accessing sensitive information while it’s in transit.
Want to make sure a site is using this technology? Look for the padlock icon in the URL bar, and the “s” in the “https://”. If you see these signs, you'll know that your connection to that site is encrypted.
It’s a good idea to access sites secured with a TLS certificate when:
- You store or send sensitive data online. If you use the internet to carry out tasks such as filing your taxes, making purchases, renewing your driver’s license, or conducting any other personal business, visiting sites using TSL is a good idea.
- Your work requires it. Your workplace may have encryption protocols, or it may be subject to regulations that require encryption. In these cases, encryption is a must.
Why you need encryption
Whether you’re a national bank safekeeping millions of financial documents or someone just texting their address to a friend in town, taking extra safety precautions like encryption to safeguard your data can help avoid serious cybersecurity threats.
Internet privacy concerns are real
Encryption helps protect your online privacy by turning personal information into “for your eyes only” messages intended only for the parties that need them—and no one else.
You should make sure your emails are being sent over an encrypted connection, or that you are encrypting each message.
Most email services come with the option for encryption in their settings menu. If you check your email with a web browser, take a moment to ensure that encryption is enabled on your account.
Hacking is big business
Did you know over 75% of cyberattacks start with an email? Cybercrime is a global business, and consumers are participating whether they know it or not. Nearly every action you take online—from forwarding an email to scrolling through Facebook—can be an opportunity for cybercriminals to target your personal information.
Cybercriminals are often out to steal sensitive data for financial gain. Encryption can help ensure your data is safe from prying eyes.
Regulations require it
In some cases, encryption isn’t just an internet best practice to follow—it’s required by law. For example:
- The Health Insurance Portability and Accountability Act (HIPAA) requires healthcare providers to implement security features like encryption to protect patients’ sensitive health information.
- Higher learning institutions must take similar steps under the Family Education Rights and Privacy Act (FERPA) to protect private student records.
- Retailers must contend with the Fair Credit Practices Act (FCPA) and similar laws to help secure sensitive consumer information, such as credit card numbers and shipping addresses.
Encryption helps organizations stay compliant with regulatory privacy requirements and standards. It can also help protect valuable proprietary data and customers’, clients’, and patients’ sensitive information.
Can scammers use encryption to commit cybercrimes?
Encryption is designed to protect your data, but it can also be used against you.
Targeted ransomware is a cybercrime that occurs when hackers deploy ransomware to encrypt various devices, including computers and servers, making the information stored on them inaccessible. The attackers often demand a ransom before they agree to decrypt the data. The goal is to persuade individual internet users or organizations to pay up in order to recover access to their important files, data, video, and images.
Ransomware attacks aimed at large organizations and government agencies tend to generate the biggest headlines. But ransomware attacks can also happen to you.
Here are some tips to help protect your devices against ransomware attacks and the risk of having your data encrypted and inaccessible.
- Install and use trusted security software on all your devices, including your mobile phone, and keep it up to date. Security software can help protect your devices against ransomware and other cyberattacks.
- Update your operating system and other software. Developers often release updated versions to address new security vulnerabilities, so don’t keep closing that pop-up asking you to update.
- Avoid reflexively opening email attachments. Email is one of the principal methods for delivering ransomware. If you can’t verify who the email is from, don’t open any links or attachments and report it as spam.
- Be wary of any email attachment that advises you to enable macros to view its content. If you enable macros, macro malware can infect multiple files.
- Back up your data to an external hard drive. If you’re the victim of a ransomware attack, you’ll still be able to restore your files if they were compromised or lost.
- Consider using cloud services. This can help mitigate a ransomware infection, since many cloud services retain previous versions of files, allowing you to “roll back” to the unencrypted form.
- Don’t pay the ransom. You could pay a ransom in hopes of getting your files back, but there’s no guarantee the cybercriminal will release your data.
Encryption is essential to help protect your sensitive personal information. But in the case of ransomware attacks, it can do more harm than good. It’s smart to take steps to help you gain the benefits and avoid the damage.
FAQs about encryption
Read along to learn the answers to some common questions surrounding encryption.
Which type of encryption is most secure?
Advanced Encryption Standard (AES) uses a very long key, making it harder for hackers to crack the code. Even in its most efficient 128-bit form, AES has never been cracked, which is why this type of encryption algorithm is the standard for government and military applications.
Can a hacker see encrypted data?
A hacker can see encrypted data, but they won’t be able to understand it. Encrypted data is scrambled and unreadable until the user applies an encryption key or password to decrypt it. If a cybercriminal gets their hands on the encryption key or is able to crack the algorithm, then they’ll be able to decrypt and access the data.
What is the most common encryption attack?
Brute force attacks are the most common method for cracking encryption algorithms. The hacking method uses trial and error to systematically check every possible solution. That said, well-designed and secure cryptosystems have long encryption keys that would take billions of guesses to crack, making them virtually impervious to brute force attacks.
How do you keep encryption safe?
A few of the best ways to keep your encrypted data safe include using end-to-end encrypted messaging apps, enabling encryption across all your devices, using strong passwords and two-factor authorization, and keeping your devices and apps updated.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.





Want more?
Follow us for all the latest news, tips, and updates.