What is an evil twin attack? How to spot and avoid them
What is an evil twin attack?
An evil twin attack is when a hacker creates a Wi-Fi hotspot that impersonates a legitimate Wi-Fi network and then uses it to spy on your internet activity and steal your information, such as login credentials.

Be it a coffee shop, airport, or hotel, we've all been to places where we've needed to use a Wi-Fi connection other than our own.
Public Wi-Fi networks make this super easy — perhaps a little too easy, as hackers have quickly created clever attacks to take advantage of public Wi-Fi networks and their users.
An evil twin attack is a perfect example.
In an evil twin attack, a hacker creates a twin network to impersonate an existing Wi-Fi connection in order to lure unsuspecting users into their trap, where they'll then steal your personal information or infect your device with malware.
So how do evil twin attacks work, and what can you do to spot and avoid them? To find out, follow our total protection guide.
How evil twin attacks work
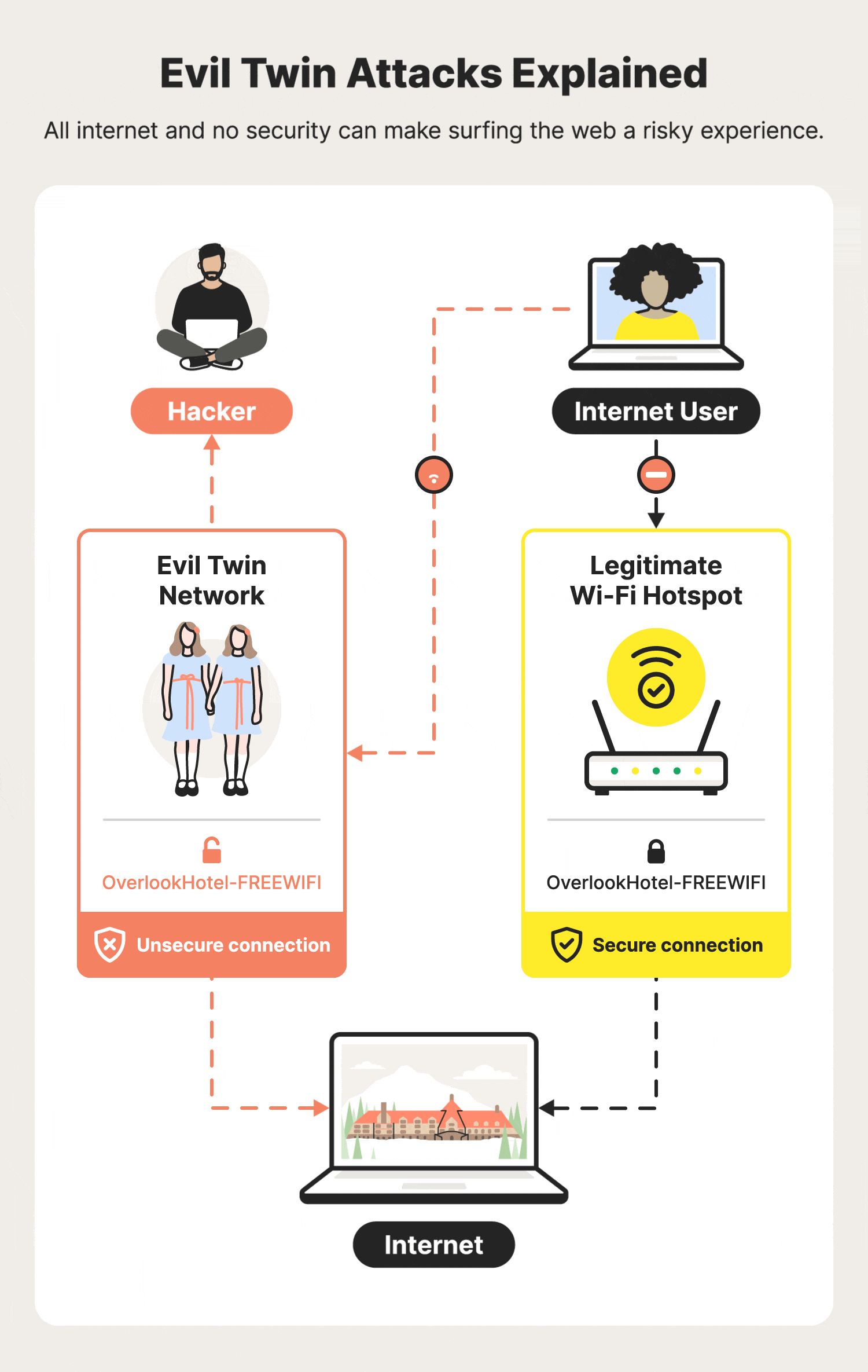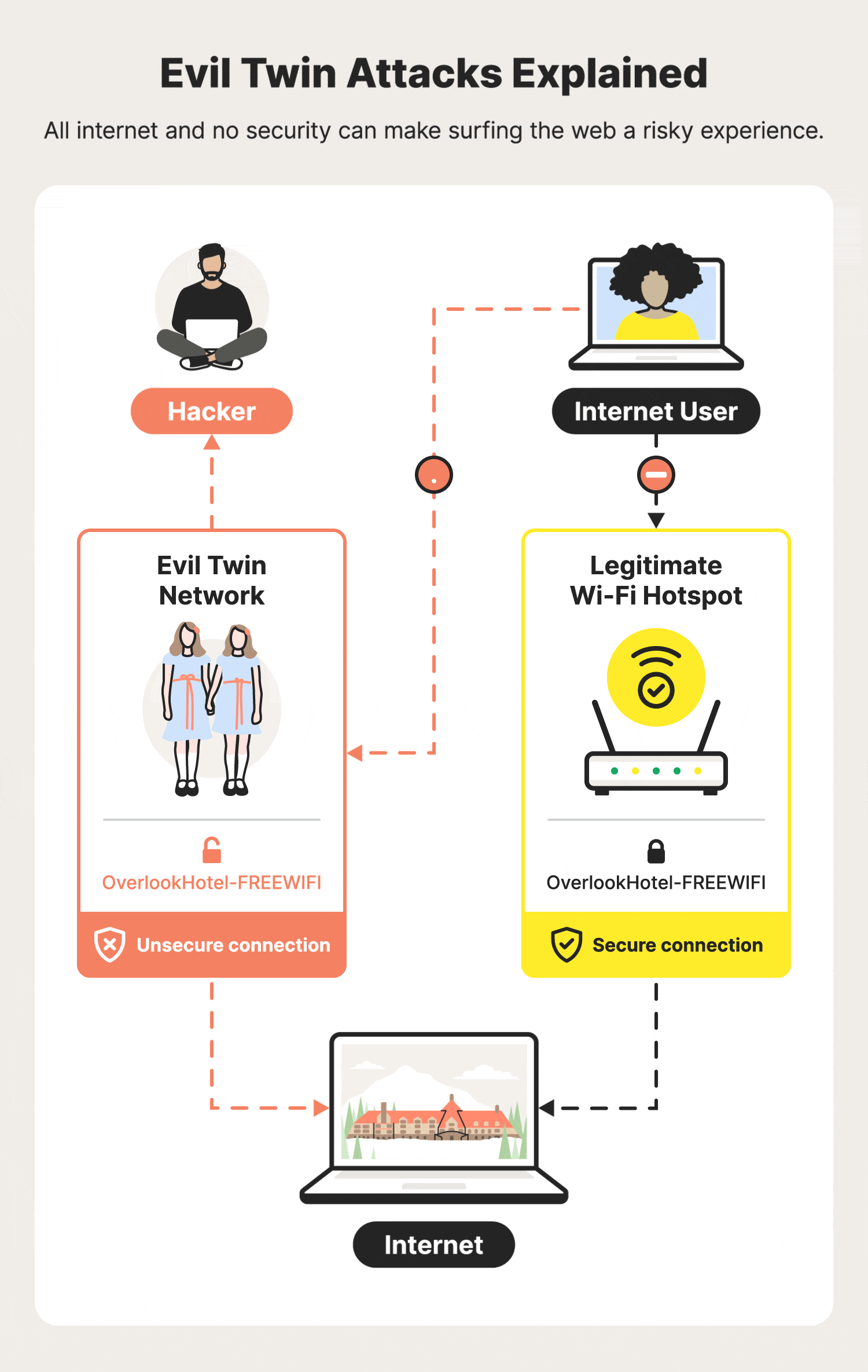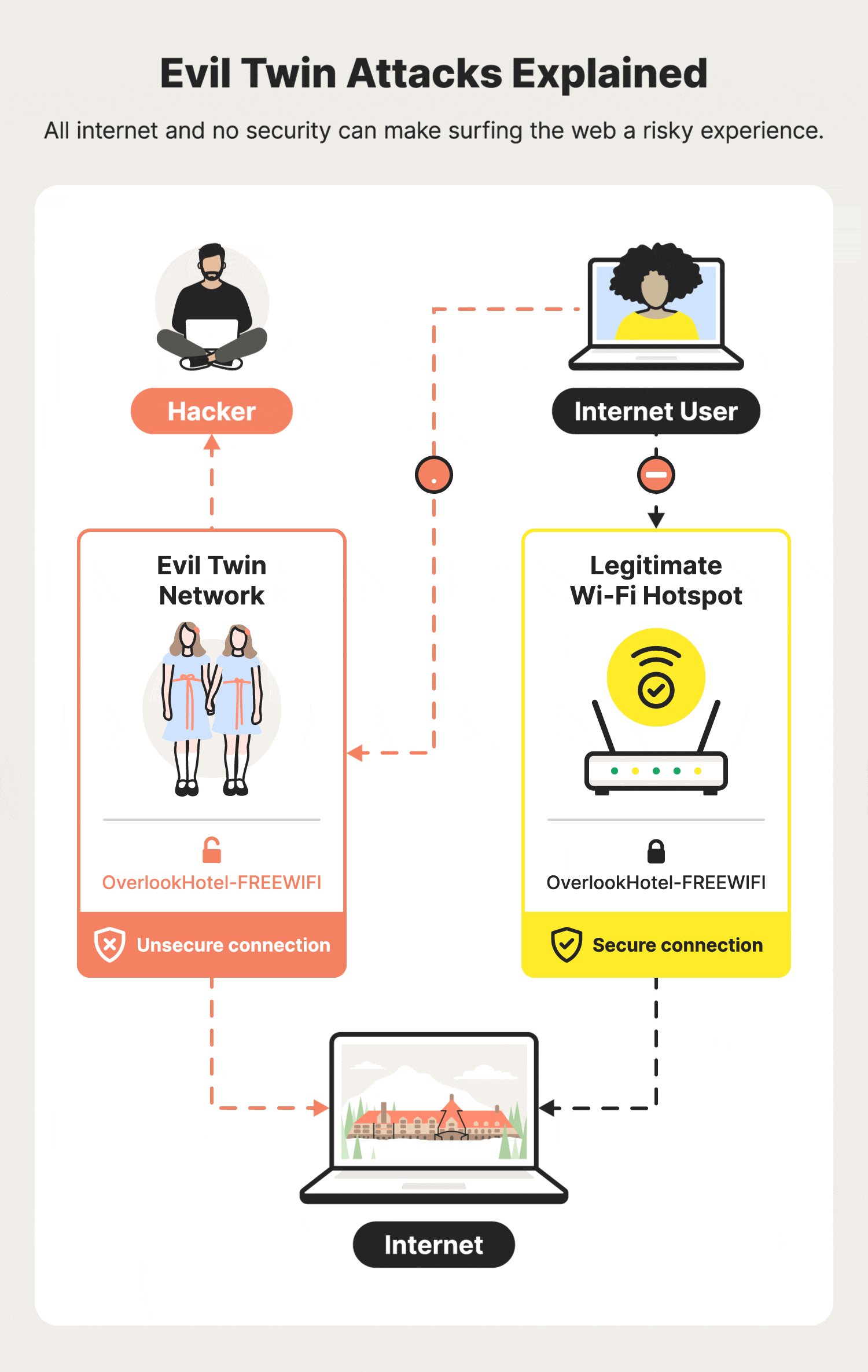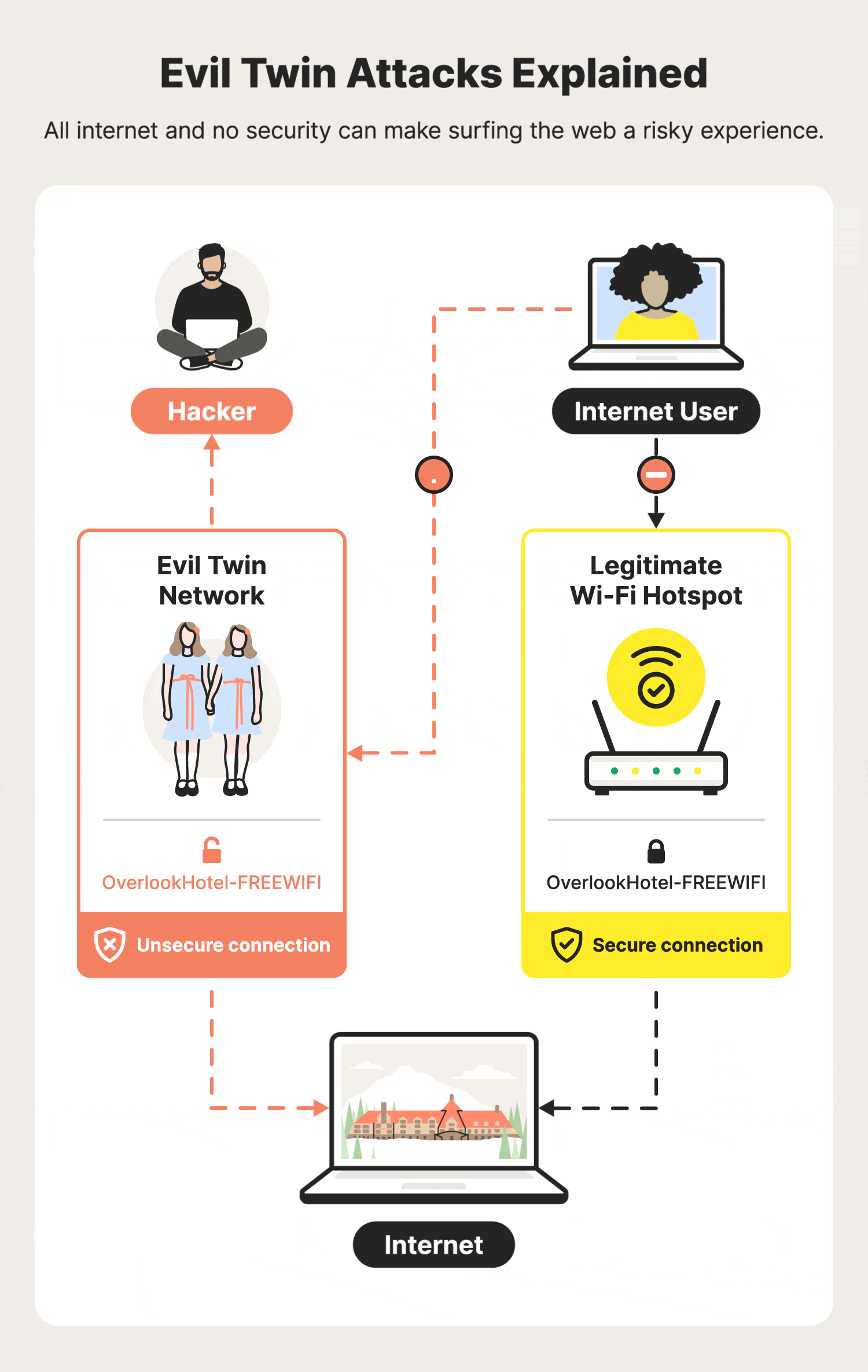
Hackers can thrive using evil twin attacks by convincing users that they are connecting to a legitimate Wi-Fi router when they are actually walking right into the hacker’s trap. You might think of it like the Overlook Hotel in “The Shining” — while the Wi-Fi connection may look perfectly fine on the outside, there's in fact a malicious party haunting the inside.
To make the attack as successful as possible, the hacker will usually follow these steps:
Step 1: They select a location
Before a hacker can carry out an evil twin attack, they must first decide where to do it. In most cases, evil twin attacks are carried out in busy areas with a popular free public Wi-Fi connection, such as a coffee shop, library, airport, or college campus.
Because these areas can sometimes include multiple Wi-Fi hotspots under the same name, it’s easy for the hacker to mask their evil twin network without looking suspicious.
Step 2: They set up an evil twin network
Next, the hacker will set up their evil twin network using the same service set identifier (SSID) name as the genuine Wi-Fi router in the area. The hacker may do this using a phone, portable hotspot, tablet, or computer.
While people in the area look for Wi-Fi networks to connect to, they won’t be able to easily distinguish which hotspot is legitimate, making it easy for the hacker to get people to connect to their malicious hotspot.
Step 3: They create a fake captive portal page
Once the hacker sets up their evil twin network, they’ll create a fake captive portal page. If you’ve used public Wi-Fi, then you’ve likely seen a captive portal page before. A captive portal page is a webpage that automatically opens once you connect to a Wi-Fi network, prompting you to enter basic information to continue using the network.
Not only do fake captive portal pages help the Wi-Fi connection seem more genuine, but hackers will specifically set them up to trick you into giving up personal information or clicking a suspicious link.
Step 4: They make their network easily accessible
With everything configured to the hacker's liking, their focus will be to move their hotspot to an area most accessible to potential targets. By placing their hotspot as close as possible to the largest number of people, they maximize their chances of people connecting to their evil twin access point, as it may provide a stronger signal than the legitimate network in the area.
Step 5: They steal your data
Finally, the hacker will use their evil twin network and fake captive portal page to steal your data. In this classic man-in-the-middle (MITM) attack, the hacker will be able to monitor everything you do online. If you log into any personal accounts while connected to their network, the hacker could capture your login credentials and use them to access any of your accounts that use the same password.
Not only are evil twin attacks an invasion of your online privacy, but they are also extremely dangerous, especially if you use the same password for multiple accounts. On top of that, these fake captive portal pages could also be used to sneak malware onto your device.
Evil twin attack example
Let’s say you get to the airport early one day and decide to catch up on some work before getting on your plane. You open your laptop and connect to the free Wi-Fi hotspot with the strongest signal. Even though your device says that the Wi-Fi network is “unsecure,” you connect to it anyway, assuming it’s only because the hotspot doesn’t require a password.
After finishing up your work, you decide to check your bank account to make sure your most recent paycheck has come through. Without thinking twice, you log into your bank account and go about your day, browsing social media and watching your favorite TV show while waiting for your flight.
But all the while, a hacker has been monitoring everything you’ve done and has captured your login credentials to your bank, Facebook, and Netflix accounts. After landing at your destination, you realize that someone has been tampering with your social media accounts and has transferred money out of your savings account.
This is an example of a successful evil twin attack. To help prevent an attack from going this far, look at some of the warning signs of an evil twin attack.
How to spot an evil twin attack: 3 warning signs
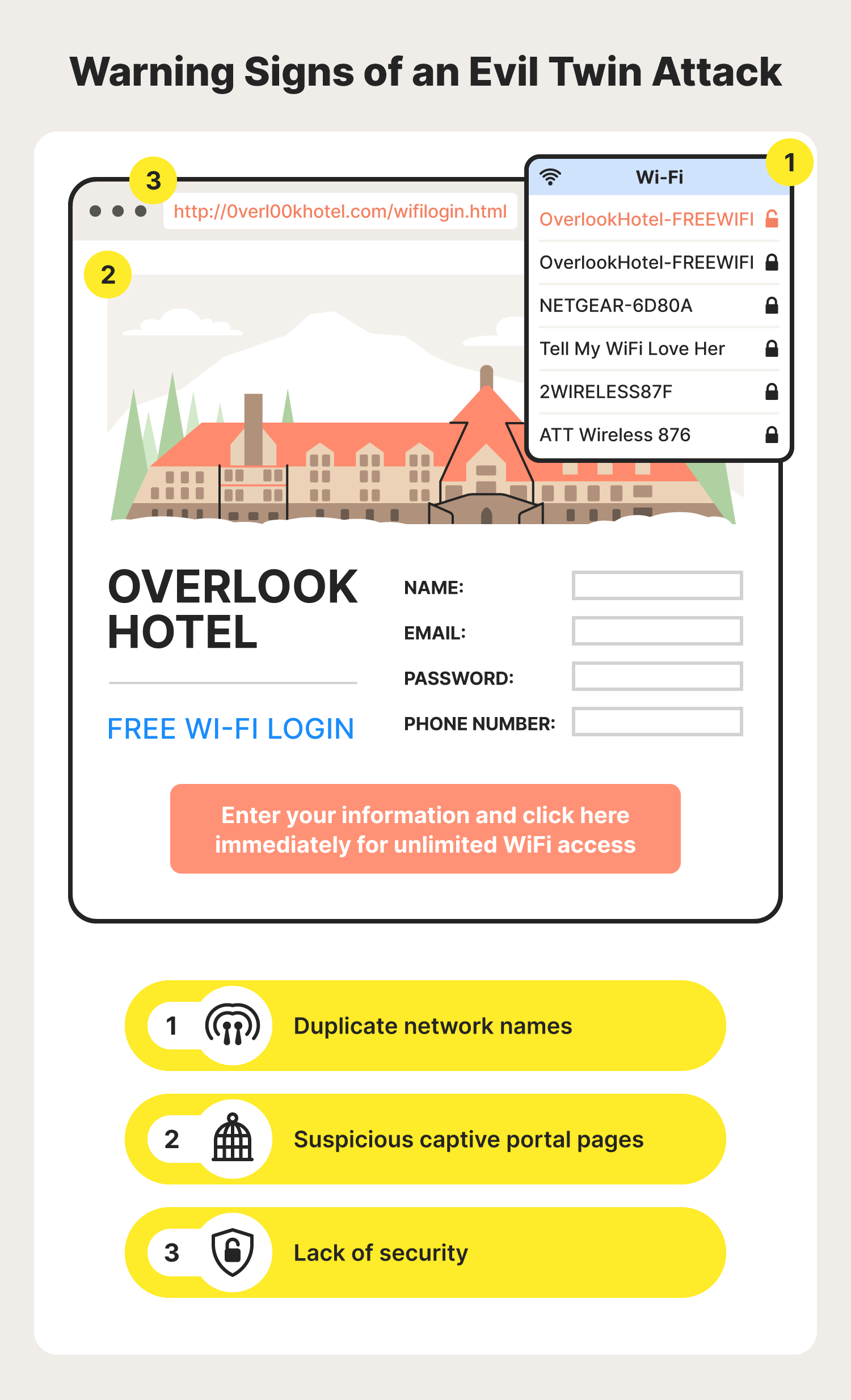
Without specialized tools that may be hard for common users to access and understand, evil twin attacks can be difficult to detect. But there are some warning signs you can look out for to sniff out a fishy Wi-Fi connection, including:
- Duplicate network names: While multiple legitimate public hotspots can share the same name, it is also a possibility that the duplicate network is an evil twin router in disguise. Evil twin names often copy another Wi-Fi network’s name exactly. Because of this, always be wary if you notice a duplicate network name in an area that usually only has one connection option.
- Suspicious captive portal pages: Whenever you’re directed to a captive portal page, be sure to take your time to assess the legitimacy of the page before blindly inputting whatever information they ask for. Keep an eye out for any typos, grammatical errors, or suspicious links that could take you to a malicious website.
- Lack of security: Oftentimes your device will give you clues if you’re about to connect to an unsecure network. For example, it may say “unsecured network” underneath the network name. If you ever see any warning related to the security of a Wi-Fi hotspot you want to connect to, you may want to avoid the network altogether.
No matter where you are, always be sure to take a close look at the Wi-Fi hotspot you’re connecting to. Additionally, if you connect to a new network that features a captive portal page, be sure to give it a thorough look before inputting any information.
How to avoid an evil twin attack: 7 protection tips
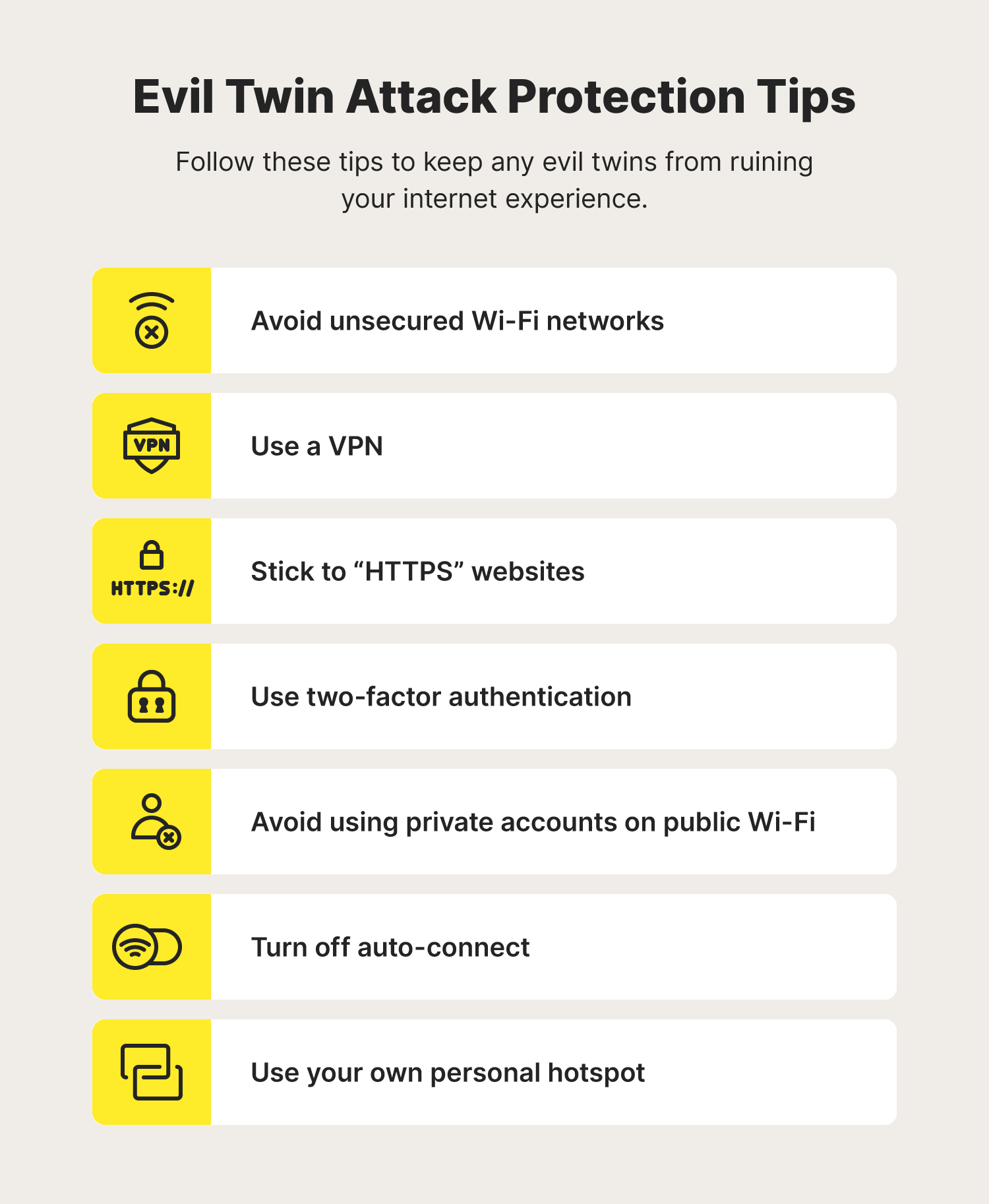
Because evil twin hacking may not look as obvious as other cybersecurity threats, it’s important to prioritize doing whatever you can to protect yourself. To help reduce the risk of falling for an evil twin cyberattack and the resulting damage, keep the following protection tips in mind.
Avoid unsecured Wi-Fi networks
If you ever see a network marked as unsecure while searching for a Wi-Fi connection, it’s best to avoid it, as most evil twin networks will be marked as unsecure. Even if it isn’t an evil twin network, unsecure Wi-Fi networks are susceptible to other Wi-Fi threats like MITM attacks.
Use a VPN
Using a VPN is a great way to increase your privacy and security when using public Wi-Fi connections. One of the benefits of using a VPN is that all your internet activity will be encrypted before the evil twin hacker can see it. This additional layer of protection could be the difference between successful and unsuccessful evil twin Wi-Fi attacks.
Consider a trusted virtual private network like Norton Secure VPN that encrypts personal information you send and receive.
Stick to “HTTPS” websites
Whenever you use a public connection, be sure to stick to websites that begin with “HTTPS.” These types of websites include SSL certificates and are encrypted, preventing any evil twin hackers from viewing your browsing activity.
Use two-factor authentication
Two-factor authentication (2FA) is a great way to protect unsuspecting users from accessing your online accounts. With 2FA enabled, a hacker will be unable to access your accounts even if they capture your login credentials with their evil twin network.
Avoid using private accounts on public Wi-Fi
When using public Wi-Fi networks, it's best to remain signed out of any sensitive accounts. That way, if someone is snooping on your browsing activity, they won’t be able to see your login credentials and access any of your accounts.
Turn off auto-connect
Some devices have an auto-connect feature that automatically connects to any nearby Wi-Fi hotspot you’ve connected to before. This can be dangerous, especially if you’ve ever accidentally used a fake Wi-Fi connection in the past. To make sure you’re always carefully selecting the Wi-Fi network you use, disable auto-connect.
Use your own personal hotspot
Your own personal hotspot is a safe alternative you can use when you’re away from your home Wi-Fi network. Whether you own a personal hotspot device or use your smartphone, personal hotspots are a great option to ensure you’re connected to a trusted network. Just be sure to set a secure password on your hotspot to keep out any unauthorized users.
What to do if you encounter an evil twin attack
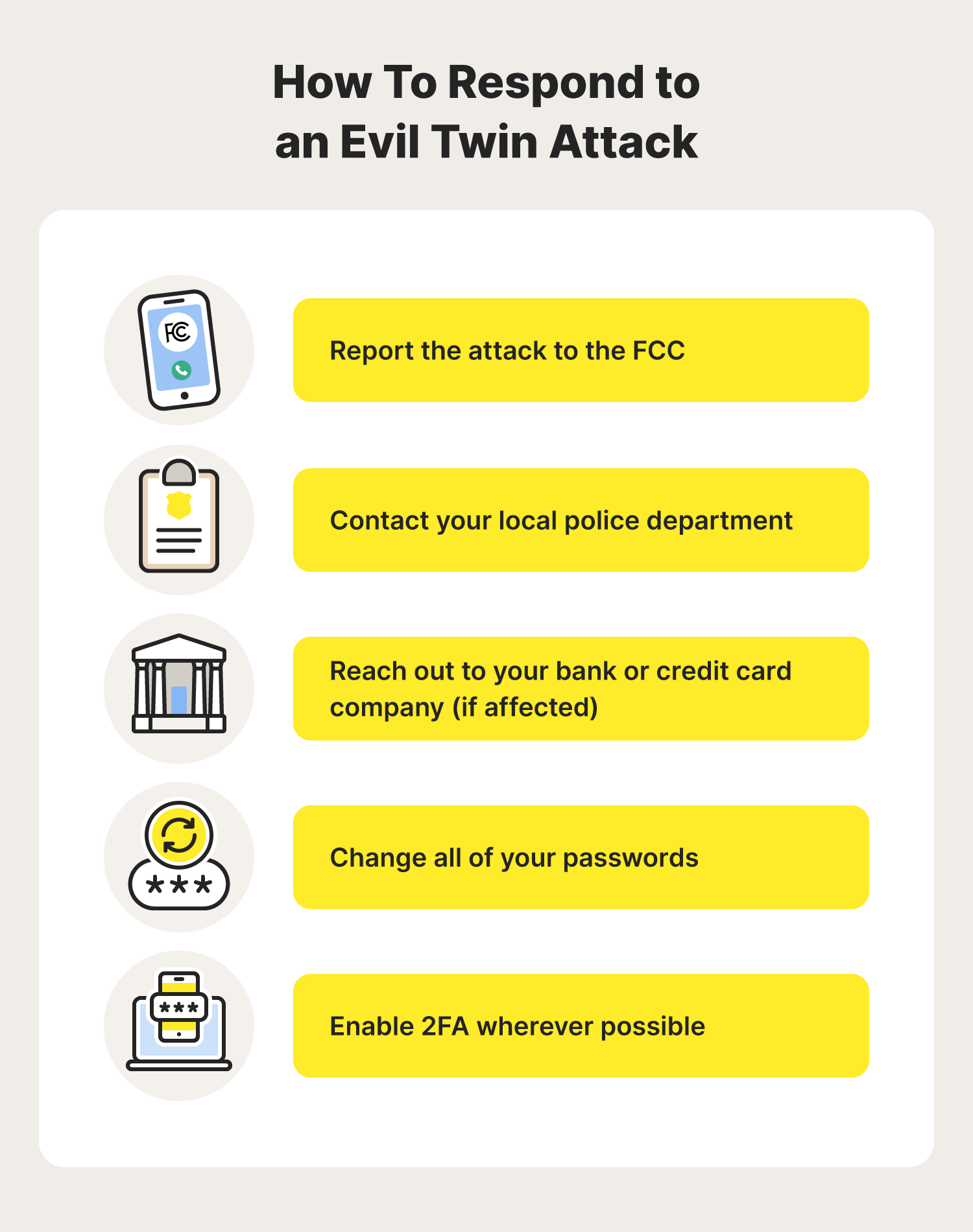
Now that you’ve learned how to detect and avoid evil twin attacks, you may wonder how you should respond if one slips through the cracks. Don’t worry, we’ve got you covered.
If you are impacted by an evil twin attack, you should:
- Report the attack to the Federal Communications Commission (FCC).
- Contact your local police department.
- Reach out to your bank or credit card company (if affected).
- Change all your passwords.
- Enable 2FA wherever possible.
Whether you’re traveling or you’re at your favorite coffee shop, an evil twin attack is only one of the risks associated with public Wi-Fi. To ensure you’re always surfing the web as safely as possible, consider educating yourself on the dos and don’ts of public Wi-Fi.
FAQs about evil twin attacks
Let’s look at some common questions surrounding evil twin attacks.
Do evil twin attacks involve free Wi-Fi?
Yes, evil twin attacks are a type of attack hackers use involving free Wi-Fi. These attacks are commonly done in public areas where the Wi-Fi attacker can impersonate a legitimate public Wi-Fi connection.
How do evil twin attacks affect you?
Evil twin attacks allow hackers to snoop on your internet activity, which may allow them to steal login credentials, credit card information, and other details that could even lead to identity theft. In addition, an evil twin network could use its fake captive portal pages as a way to spread different types of malware.
What’s the difference between a rogue access point and an evil twin attack?
The difference between a rogue access point attack and an evil twin attack is that a rogue access point is an unauthorized device that is plugged into a real network and controlled by a hacker. On the other hand, an evil twin attack is a separate network set up to impersonate a legitimate Wi-Fi hotspot.
What is a malicious hotspot?
A malicious hotspot is a Wi-Fi hotspot set up intentionally to take advantage of unsuspecting Wi-Fi users, whether to spy on their internet activity or infect their devices with malware. An evil twin Wi-Fi network is an example of a malicious hotspot.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.





Want more?
Follow us for all the latest news, tips, and updates.