What is a zip bomb and how does it work?

Zip bombs are destructive malware that use expanding files to overwhelm operating systems. Learn how these malicious files work and how to identify them. Then, get Norton 360 Deluxe to scan compressed files to help detect and block zip bombs and other malware.
What is a zip bomb?
A zip bomb is a type of malware that masquerades as an inconspicuous file until you unzip it—causing it to rapidly expand and make your device crash. This malicious software—also known as a decompression bomb, archive bomb, or "zip of death"— uses compression algorithms to generate smaller files than uncompressed ones.
The main objective of a zip bomb is to trick the victim's program or system into sending over more resources during the decompression process, resulting in crashes, DDoS attacks, and overall system instability.
Once unzipped, the zip bomb download expands and can unleash multiple petabytes worth of useless and repetitive data, overloading the device’s memory and overworking the central processing unit (CPU).
Cybercriminals typically set off zip bombs to:
- Render a device unusable
- Disrupt systems and software
- Disable antivirus software
- Create an opening for malware attacks like viruses, trojans, and spyware
- Retaliate against individuals, organizations, and other entities
- Show off the cybercriminal's capabilities
How do zip bombs work?
A zip bomb uses recursive compression, compressing files multiple times within an archive. This process exploits existing compression algorithms in ZIP applications; with the compounding of each iteration, the compressed file size grows exponentially.
For example, a file might start at just a few kilobytes, but after many rounds of compression, it might expand to hundreds of gigabytes or even terabytes.
Using infinite decompression loops that trick decompression tools, zip bombs end up exacerbating the system or specific program. These loops use a series of never-ending structures that eat up many system resources, causing decompression tools to get stuck in a continuous, unending cycle of extraction attempts.
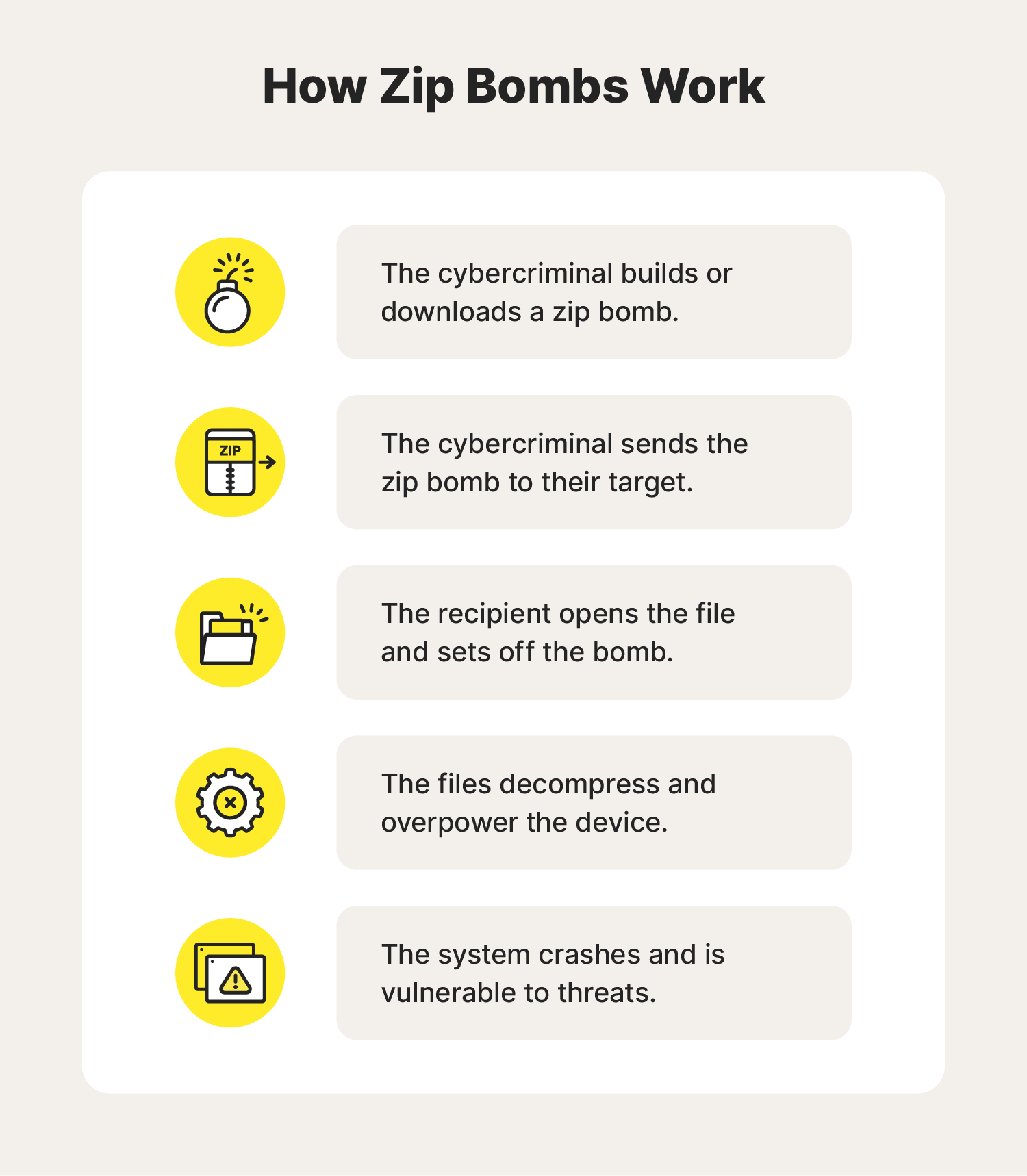
Here’s how zip bombs work in more detailed steps:
- The cybercriminal adds large amounts of useless and repetitive data to a zip file and compresses it or downloads an existing zip bomb.
- The cybercriminal sends the zip bomb to their target, usually via email.
- The target receives the file and attempts to unzip and open it.
- The decompression process begins, causing the decompressed layers to grow exponentially.
- The rapid expansion overwhelms system resources, leading to a denial of service (DoS) attack, system crashes, and ultimately leaving the system unstable and vulnerable to cybersecurity threats.
What happens if you open a zip bomb file?
If you open a zip bomb file, it will start decompressing. Depending on its design, it may expand to an overwhelming size and consume all available system resources. Zip bombs can potentially cause:
- Memory and CPU overload
- System crashes and slowdowns
- Data loss and corruption
- Denial of service
- Operational disruptions
To remove malware safely, you’ll need to use a reputable antivirus that can scan for malware to help detect and quarantine online threats like zip bombs. If that doesn’t work, you may need to enlist the help of an IT expert.
How to detect a zip bomb download
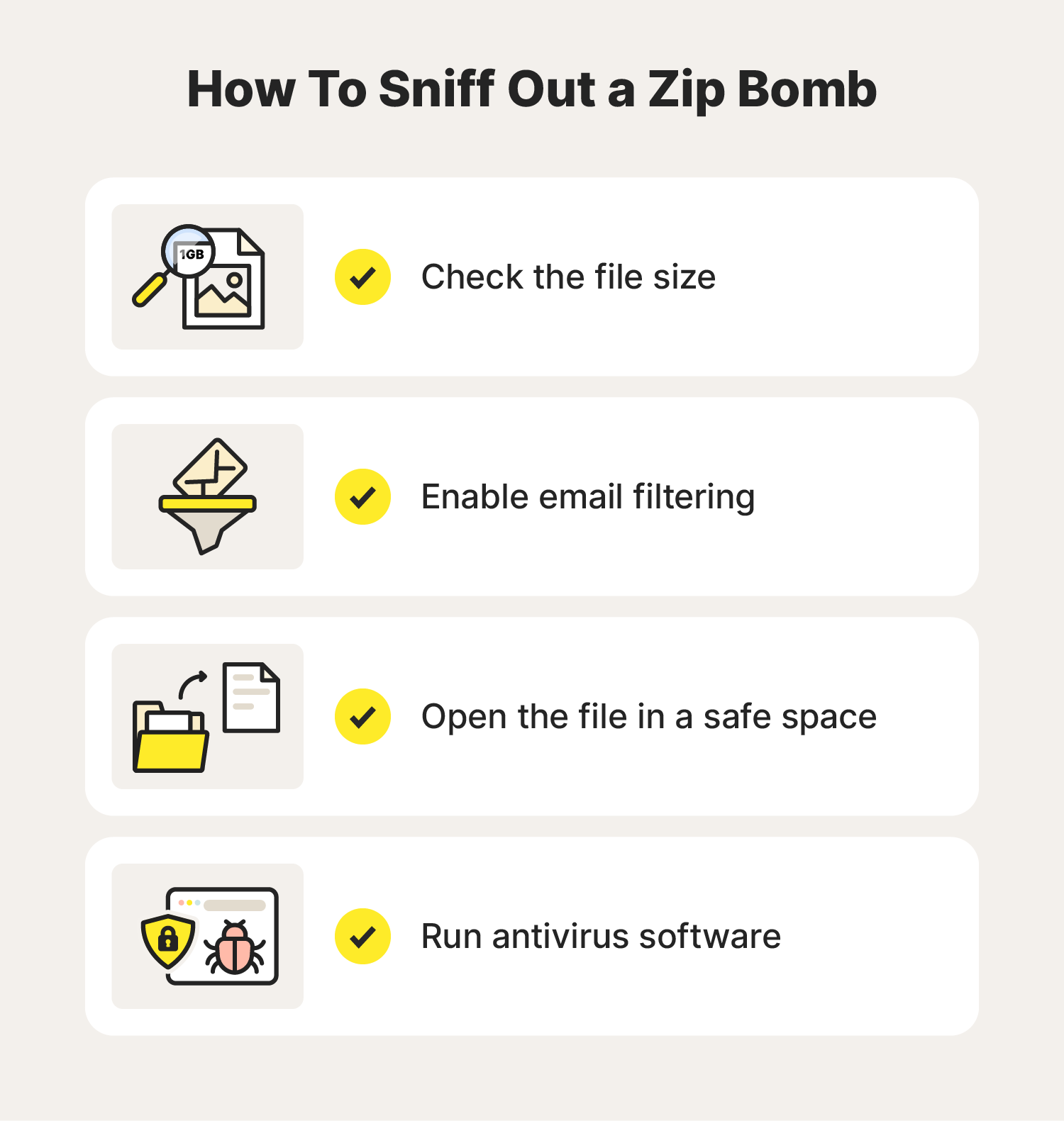
There are a few strategies you can use to determine if a zip file is actually a zip bomb:
- Use antivirus software
- Check the file size
- Enable email filtering
- Open the file in a safe environment
Follow along in this section and learn how to detect a zip bomb download before you accidentally “set it off” to prevent data loss and avoid time-consuming repairs.
Check the file size
Make sure that the zip file is a reasonable size for the type of files you expect to receive. There is no standard dictating what file size is “too large” or more likely to be a decompression bomb. But most documents, photos, and even some videos only take up a few gigabytes. In fact, you can download an entire high-definition Disney movie to watch offline, and it would only take up to 2–4 gigabytes of space.
On the other hand, you also need to watch for files that appear too small, indicating that the sender over-compressed the file to hide its contents. In other words, be wary of any compressed files with unexpected file sizes. For reference, these are the typical file sizes for various types of media files:
- Photos: A single, high-quality photo taken on a smartphone is usually less than 2 megabytes (MB); a RAW image taken on a professional camera can be as large as 40 MB.
- Videos: Video files with 4k resolution and a high download speed can take up 84 MB of space for one minute of footage.
- PDFs: A text-only PDF document is usually 10 kilobytes (KB). However, PDF file size can change depending on various factors, including font, page size, and visual elements.
- E-books: A 300-page e-book typically eats up about 2.6 MB of space. However, file sizes can vary greatly depending on the length of the text.
Enable email filtering
Most email service providers offer robust email security features, such as filtering that can analyze incoming messages and detect threats. They typically do this by scrutinizing file sizes, assessing compression ratios, and scanning for spammy messages. If your provider detects an issue, it will flag the email as high-risk and may even re-route it to your spam folder—keeping you from unknowingly decompressing a malicious file.
Open the file in a safe space
To eliminate the risk of crashing your system, use a sandbox environment (a protected space) to decompress a zip file and ensure it’s free of malware before opening it on your device. This tactic does require more technical expertise. But if you have the know-how or access to tech support, it’s one of the safest ways to see how an archive file will consume resources and if it’s safe to unzip on your device.
Run antivirus software
Scan files with antivirus software like Norton 360 Deluxe before you unzip them to help detect threats like zip bombs and other types of malware. Strong antivirus tools can help automate file inspection by analyzing file structures, compression ratios, and other patterns associated with malicious archives. If the scan comes back clear, the file is probably safe.
Reliable antivirus software is a great resource. Of course, you should still keep an eye out for possible malware to further protect yourself in the face of unknown threats, unexpected encryption techniques, and non-traditional malware signatures.
Help protect your devices against malware
Good digital hygiene will go a long way to helping you stay protected against malware. That means keeping your operating system and other software updated, opening files only from trusted senders, and using online security tools to help detect and block dangerous downloads and suspicious links.
Use Norton 360 Deluxe to scan compressed files to help detect and block malware and isolate potential online hazards. Norton’s enhanced file scanning and threat detection capabilities provide powerful layers of protection to help block zip bombs and fight other malware trying to infect your device.
FAQs about the “zip of death”
Still have questions about zip bombs? Here’s what you need to know.
What do zip bombs do?
Zip bombs expand to an overwhelming size when decompressed to cause system crashes or pave the way for a denial of service attack and other malware downloads.
What is the biggest zip bomb?
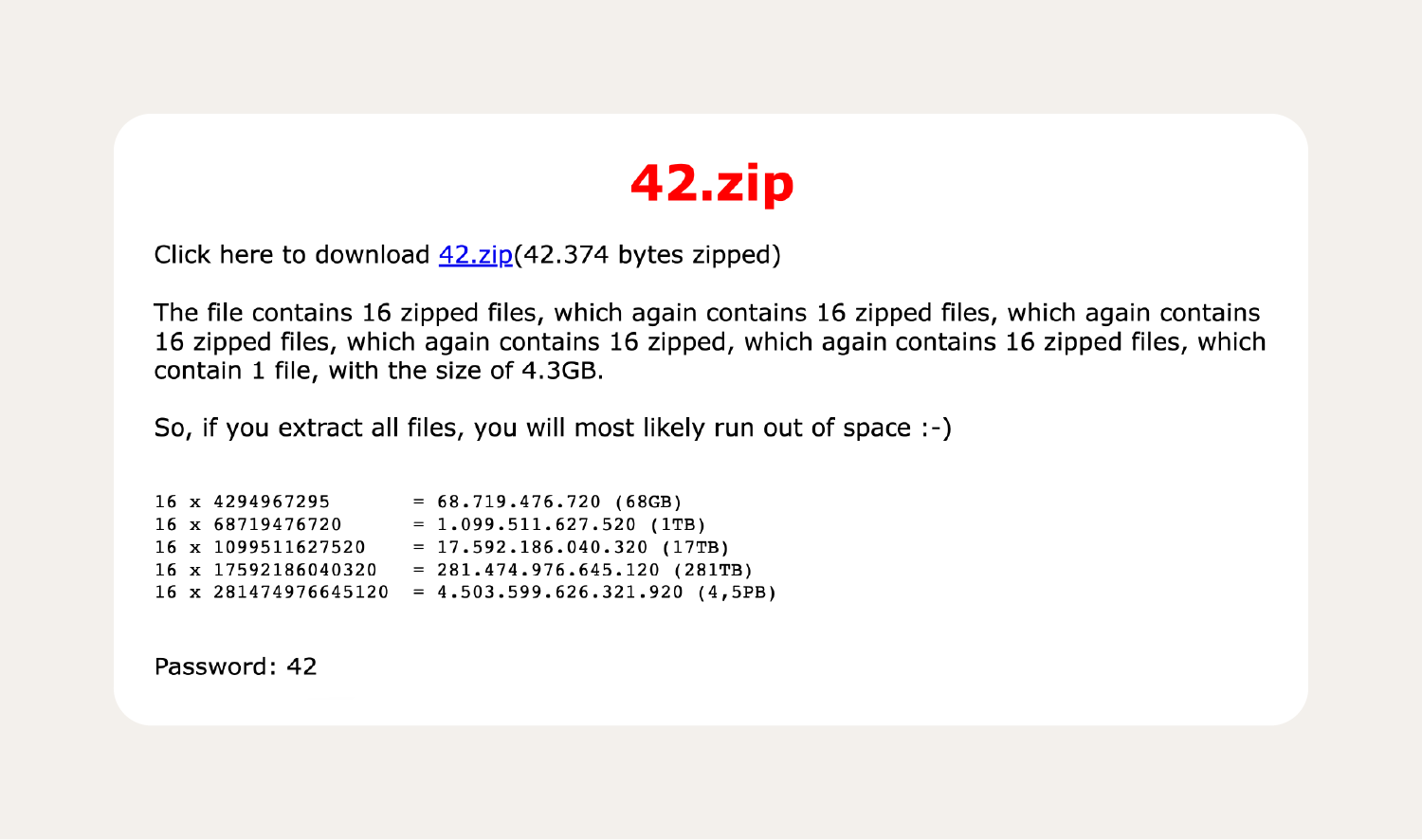
The “42.zip” is one of the largest and best-known zip bombs. When unopened, it appears to hold only 42 kilobytes of data. However, after decompressing, the file can expand to 4.5 petabytes (the equivalent of 4,500 terabytes).
Can you remove a zip bomb?
Possibly, but it can be difficult to undo a zip bomb’s damage, especially if it overwhelms your device's operating system and causes it to shut down. Your best bet is to use a specialized virus removal service to locate and remove the malware. If your device is still operational, you can always try to remove the malware yourself.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.





Want more?
Follow us for all the latest news, tips, and updates.